Problems tracking down Cross Site Scripting (DOM Based)
879 views
Skip to first unread message
TeeWeTee
Feb 1, 2021, 12:49:52 PM2/1/21
to OWASP ZAP User Group
ZAP reports several issues with "Cross Site Scripting (DOM Based)". I don't remember installing this additional rule but obviously I did ;-D
It states that the following vulnerabilities were found:
https://<someurl>/resources#jaVasCript:/*-/*`/*\`/*'/*"/**/(/* */oNcliCk=alert() )//%0D%0A%0d%0a//</stYle/</titLe/</teXtarEa/</scRipt/--!>\x3csVg/<sVg/oNloAd=alert()//>\x3e
https://<someurl>/resources/#javascript:alert(1)
I used active scanning in HUD where I am (normally) able to see the details of the calls. However not in this case. If I open the details where I can see the Request and Response, the response is empty and strangely the request URL is missing the the attack string (everything starting from # is not shown).
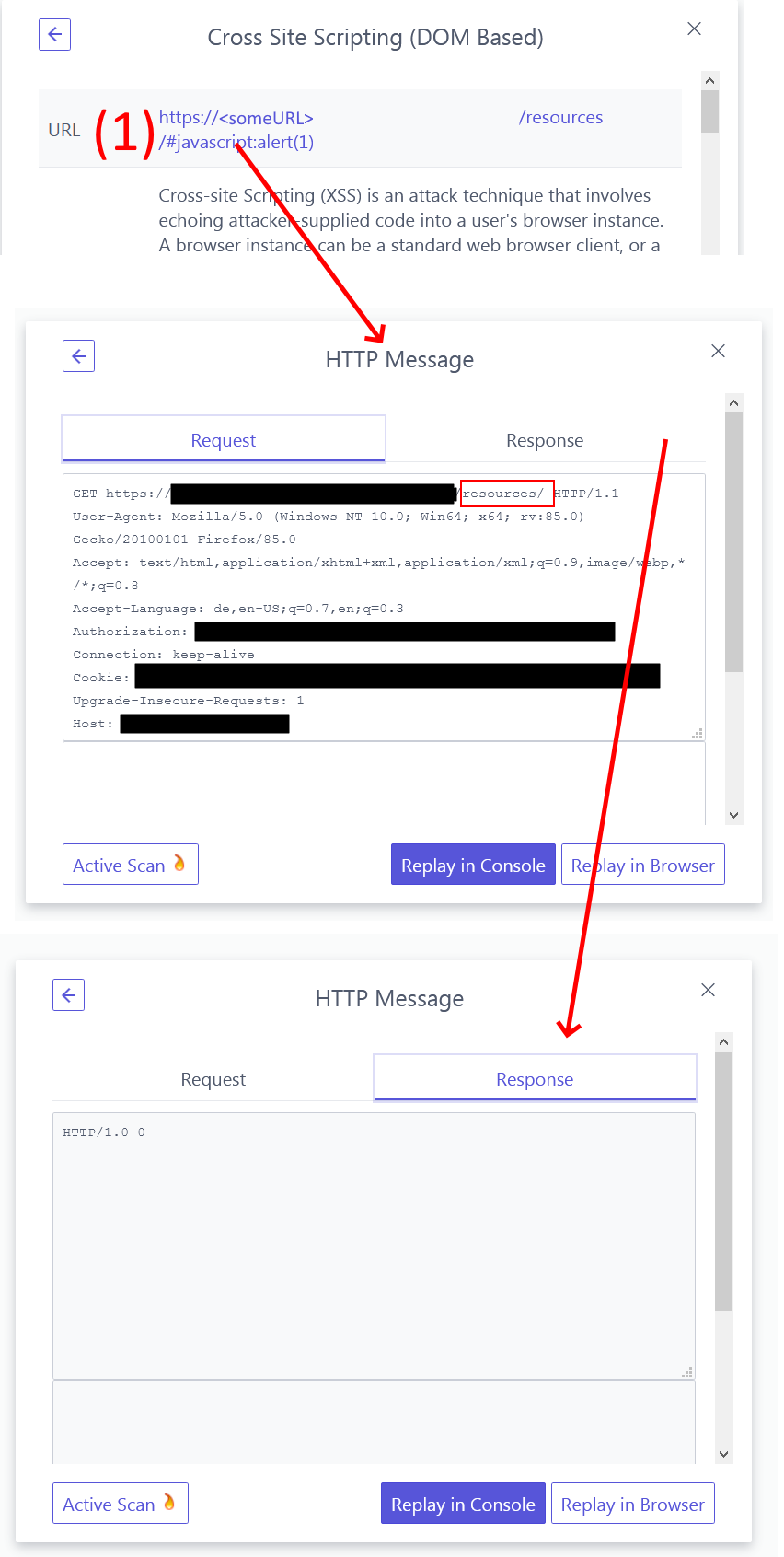
If I replay in console or in browser - the response window is
filling, however there is no JavaScript pop-up. I just see an error
message and get a 404 - which is correct and expected behavior.
So basically I tried everything but was
not able to trigger the popup. So I wanted to ask how I am able to
reproduce this? Or is this a known issue / a false positive?
kingthorin+owaspzap
Feb 1, 2021, 5:49:16 PM2/1/21
to OWASP ZAP User Group
Fragments arent sent to the server theyre onky processed client side. Reproduction depends on your browser and it's settings. Some modern browsers attempt to protect users from such issues.
TeeWeTee
Feb 2, 2021, 8:05:13 AM2/2/21
to OWASP ZAP User Group
Yes I have also read this. However I tried all the browsers (Firefox, Chrome, IE, IE emulation with older versions, ...) and even curl but was not able to reproduce this. Is there any known way how I am able to reproduce this? Any known working Browsers or am I somehow able to see what ZAP is reacting on (since the detail pages from my screenshot are not helpful)?
kingthorin+owaspzap
Feb 2, 2021, 12:35:20 PM2/2/21
to OWASP ZAP User Group
You won't be able to reproduce it in curl, because DOM based XSS requires execution of JavaScript.
JuiceShop is subject to DOM XSS, so if you can get that working then you'll know your browser isn't the blocker:
Note the first payload you listed includes onclick handling so may require a click to trigger the XSS, the second uses javascript:alert(1) which is essentially a URL and would also likely require a click. Zap's desktop UI might give you some further details, and viewing/inspecting the page source may also give you some insight (after having visited the page via one of the injected URLs). [Note as of ummmm Firefox 71 the "javascript:" handler no longer executes when used manually.]
TeeWeTee
Feb 2, 2021, 6:49:48 PM2/2/21
to OWASP ZAP User Group
I tried around a bit and the easiest thing was to create a local html page and drag and drop it into the browser (I attached it for anybody who is interested). Then firefox and chrome directly show a JavaScript popup.
Now I "just" need to find the real places of window.location / document.location and like and fix it...
Thanks for your help.![]()
Simon Bennetts
Feb 3, 2021, 7:42:12 AM2/3/21
to OWASP ZAP User Group
Thanks for letting us know!
Do you think there is anything else ZAP could do to make this easier to diagnose?
TvT
Feb 3, 2021, 10:43:14 AM2/3/21
to zaprox...@googlegroups.com
Yes, probably in this case more information would be good.
ZAP is really helpful and most of the errors are self explanatory and I had no problem tracking down the causes. Looking at an issue, its details, attack URLs or the request / response makes it usually quite obvious what to do.
Out of 15 issues I only had problems with two and one of them was
immediately fixed after posting it here.
So this remaining one is a tough nut to crack.
- At first I did check the server side quite intensively. Since it is a client side thing it obviously didn't help
- then I analyzed what '#' inside a link means, which led me to "fragments". This would have been helpful in the description of the error.
- then I intensively tried to reproduce the error but I couldn't. Probably modern browsers prevent such things from happening (and I tried like 15 different browsers/browser versions)
- It felt like a ZAP bug that the request/response section was empty (my above screenshots) and also that later the attack-string in the URL is missing (is irritating).
- then I posted here and kingthorin suggested to install the juice-shop and let ZAP run against it. I did however the DOM-XSS wasn't found. Maybe I need to crawl better...
- he also suggested that a click might be necessary - which was the helpful hint. I created a test page and then I was able to trigger the error for the first time (even though the code has nothing to do with our application). But my example helped me to see that this might be an actual issue...
So what can be improved?
- the error description. E.g. mentioning the whole fragments / Clientside thing
- the request/response "suddenly" is empty or shows not all the information (but in many other cases it did and is thus a valuable place for info) => Some advice that this can be the case would be good.
- the issue was reported by ZAP, so it did react to something (e.g. javascript execution?) and whatever it was, it would be helpful if it could be made more transparent somehow?
- the "source" page/link where those ZAP identified vulnerable links are used, would be helpful. (The actual link ZAP reported does not contain any HTML/JS in our case). I kind of narrowed it down by stopping the active scan shortly after the error appeared and then I checked the links in the ZAP console.
--
You received this message because you are subscribed to a topic in the Google Groups "OWASP ZAP User Group" group.
To unsubscribe from this topic, visit https://groups.google.com/d/topic/zaproxy-users/tcnjPkVUNjM/unsubscribe.
To unsubscribe from this group and all its topics, send an email to zaproxy-user...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/zaproxy-users/276ec156-6ac4-4abf-bd9c-05fac3309a90n%40googlegroups.com.
Andres Nieves
Feb 23, 2021, 1:25:01 PM2/23/21
to OWASP ZAP User Group
Hi! Ive been dealing with this issue, since Im intending to scan SAP, this is gonna be recurring.
Developing customizations on the plugin is the recommended way to overcome this issue and keep ZAP scans automated? Should I aim to use zap in a selenium test as a proxy insted?
Thanks in advance
Developing customizations on the plugin is the recommended way to overcome this issue and keep ZAP scans automated? Should I aim to use zap in a selenium test as a proxy insted?
Thanks in advance
Reply all
Reply to author
Forward
0 new messages
