OWASP ZAP Script based authentication settings
3,125 views
Skip to first unread message
Dominik
Mar 30, 2021, 3:21:17 PM3/30/21
to OWASP ZAP User Group
Hi all, hope you can help me.
I am trying to scan this website: https://gutnertest.juno.one/
However first I need to log in. I was not successful using any of the built in methods so I thought that using script based authentication might help.
Also I am setting this up with a script as we use a cookie for session management which tells the server if user is logged in and authenticated.
This is what I am doing:
# 1. Defining context
I open OWASP ZAP and I select Manual Explore, there I enter the website URL, which is https://gutnertest.juno.one/.
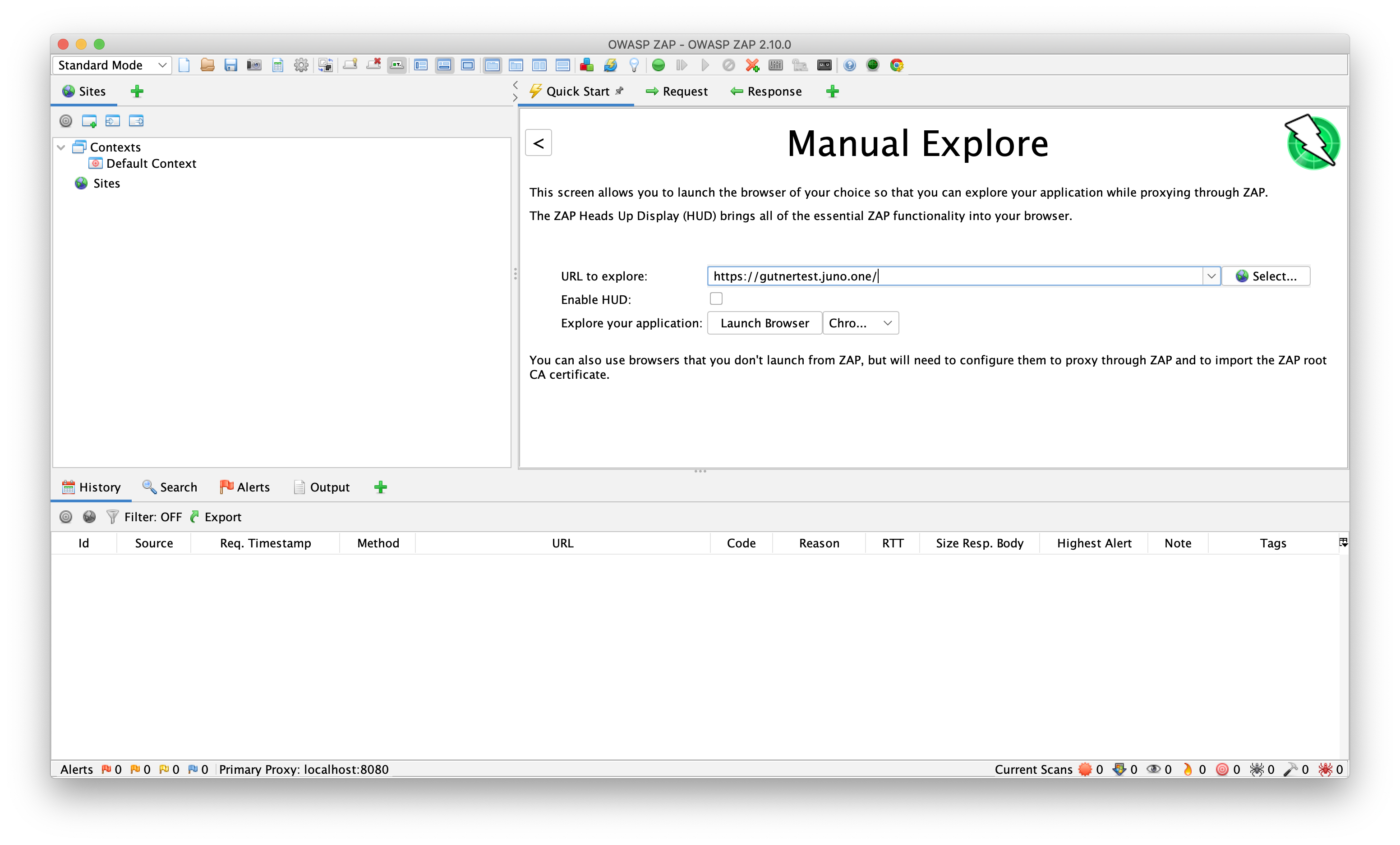
Then I click Launch Browser, the browser is opened and In history I can see all the traffic.
I keep the site open and I set the site as a new context.
This pop up is shown:
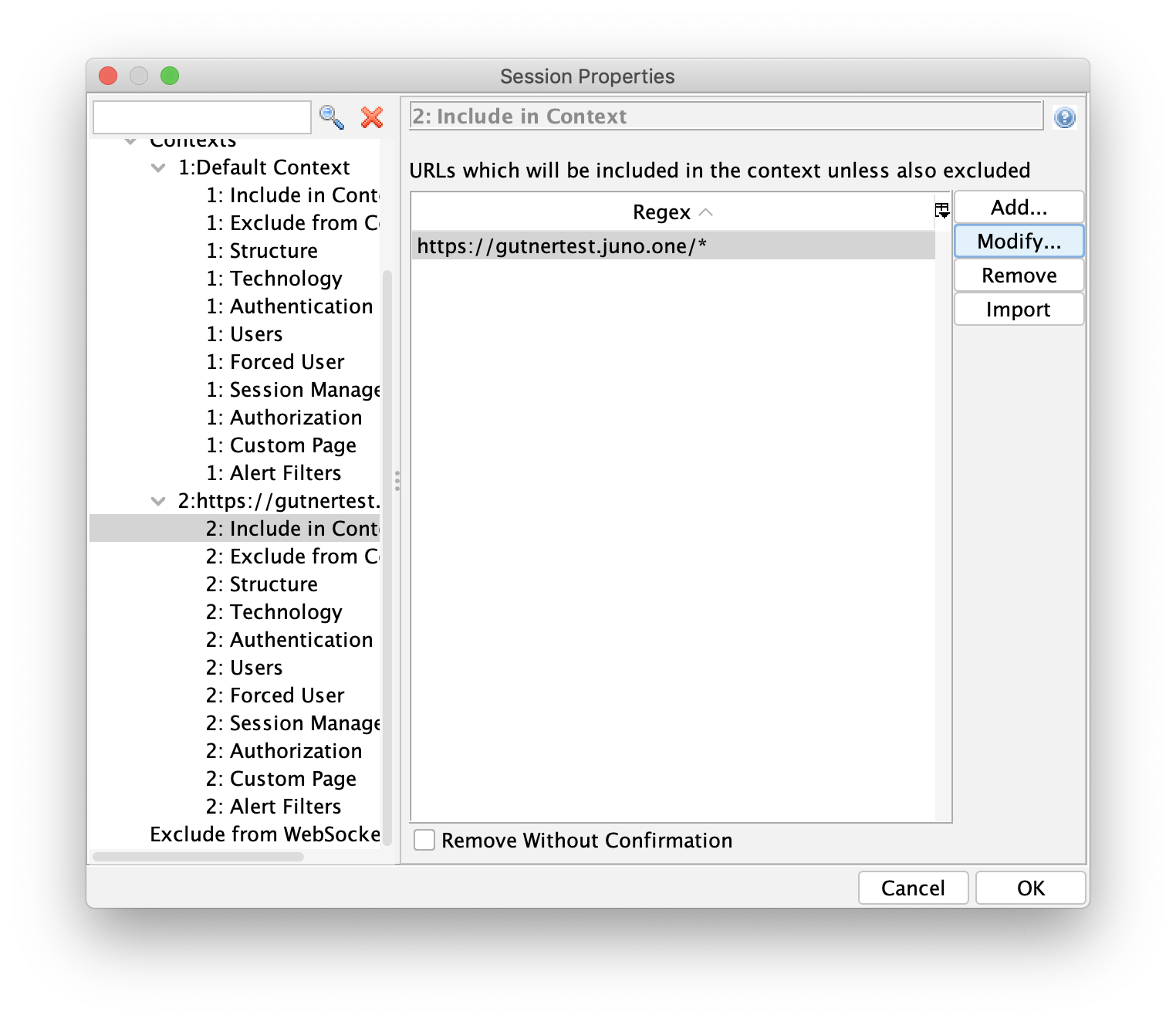
I edit the Regex to URL/ so all the URL that I want to scan will be included.
Then I just click OK.
# 2. Setting up the script
What I do then is I click the Record a new Zest script... and I set it up as follows:

Then I just click Start Recording.
After that I enter my auth details into the site (meaning into the browser I opened in the first step when defining the context):

and then I wait for the page to redirect me to the first page after login (dashboard) and then I close the browser.
After this I stop the script recording.

# 3. Editing the script
The script recorded a lot of steps which seem not important, so I edit the script, deleting some of the steps.
So for example this is how the script looked like at first:

After my edit it looked like this:

So the script comprises of:
1. GET request
2. POST request
3. 2x GET request
Note that I also added Sleep for 30 seconds, because sometimes it takes longer for the login to appear:

Probably not needed? But I am not sure, at least I think It will not do any harm, so I keep it there, if you think it might be causing problems I will remove it.
Anyways, this is my completed script.
# 4. Adding script to context as a script based authentication
After this, I add the script as a script based authentication for my created context in the following way:

After this I set up all the required stuff in the prompt as follows:

I do not set users as this data should be passed in the script (or atleast I belive thats what is happening), because when I look at the ZEST script I can see the data being passed in the POST request:
``` json
"data": "{\"email\":\"myn...@myemail.test\",\"password\":\"myreallystrongpassword\"}",
```
Because of that, I also leave Forced user mode disabled. If this is wrong, please let me know and I will add user as well.
After this I just click OK and believe that the script is added.
# 5. Running the spider
After all the prerequisites are done, I proceed to run the spider on my defined context as follows:

Initially I had a lot of Out of context results, so I also added the following expression into the Context:
``` plaintext
https:\/\/gutnertest.juno.one\/[\w\W]*
```
So my Include in context looks like this:

Now it is scanning some things, and it looks like this:

However it still does not pick up some URLs like:

# My questions
So my questions are:
Have I set up everything correctly? Is there something that should had been set up differently?
Am I really authenticated when spider is running on the website? How can I find out?
Why did the spider not pick up all the URLs (like the example above)?
If I wanted to set this up to run in docker, would it be enought just to pass the context file I just created?
Thank you very much, I would be helpful for any insight, please let me know if you need any additional information and I will supply it.
I am also new to OWASP ZAP and the forum, so please be patient with me :)
Thank you very much
kingthorin+owaspzap
Mar 30, 2021, 4:10:03 PM3/30/21
to OWASP ZAP User Group
URL fragments (everything after the #) are only processed client side. If you're missing a bunch of functionality you probably also need to run the Ajax Spider which actually uses a browser to exercise functionality in your app.
Dominik
Mar 30, 2021, 5:33:21 PM3/30/21
to OWASP ZAP User Group
Thank you for your comment. I also ran ajax spider, however it returned even less items.
Also I suspect that my authentication using the script does not work, as I have a lot of 403 Forbidden errors on most of the requests.
Do you see any error in my authentication settings?
Thank you
Dne úterý 30. března 2021 v 22:10:03 UTC+2 uživatel kingthorin+owaspzap napsal:
Simon Bennetts
Mar 31, 2021, 4:44:45 AM3/31/21
to OWASP ZAP User Group
Unfortunatley setting up authentication can be tricky, and its _really_ hard to give advice as we just dont have enough information.
Forced User Mode is good for manual testing and also for debugging these sorts of problems.
If you cant enable manual mode then you havnt specified enough information.
If you can enable it then to so and make one single request to your app, eg via the Manual Request dialog.
Then look in the history and examine each of the requests and responses. Can you see whats going on?
There is no point moving forwards to spidering or active scanning if you cant get authentication to work in the above case.
Once that is working then you are right, you should not need to use forced user mode with the spider and scanners.
How to tell if authentication is working in these cases?
Thats what the stats are for: https://www.zaproxy.org/docs/desktop/start/features/stats/ - you can access then via the API.
You get more information if you specify both logged-in and logged-out indicators.
If you run the spider and stats.auth.state.loggedin is missing or very low then you have a problem.
If so run the spider for a short period of time - you can stop it manually or constrain it via various config options.
Then look at the requests and responses sent by the spider and see if you can work out whats going on.
If you don't understand how authentication and session handling works in your application then you'll really struggle to configure ZAP to understand them so thats the first place to start.
Cheers,
Simon
Dominik
Mar 31, 2021, 5:08:02 AM3/31/21
to OWASP ZAP User Group
Hi Simon,
thanks for your comment. I usually do automated tests using selenium, where upon authentication there is no further need to care about authentication mechanics, as all this is automatic withing the browser.
I am new to pentesting, so I am struggling with the basic stuff unfortunately, however I confirmed with developers how the authentication works and its basically exactly what I wrote in my original message:
1. Upon signing in, multiple cookies are stored
2. These cookies hold tokens and values which are passed with every single request
If I test the Authentication script it works and I get status 200 OK for my POST log in request, when I check the other requests they also contain in header the required parameters, however I still get a lot of Forbidden responses.
I think I did configure the authentication incorrectly, because it works by itself - meaning if I click run when in the script dialog, but it does not work within the context.
I would like to later use the different types of scan, so I dismissed my original ideal to route selenium through ZAP Proxy because I think the result would be worse than while performing the active scan and so on.
I also tested manual authentication option, but it did not help me either.
I am mainly interested whether there is any significant error in my configuration, because from what I understand this should work as its sending the required values in headers...
Thank you very much
Dne středa 31. března 2021 v 10:44:45 UTC+2 uživatel psi...@gmail.com napsal:
Reply all
Reply to author
Forward
0 new messages
