CVE-2022-21449 related to graal-sdk
15 views
Skip to first unread message
Mohit A. Jampala
Feb 9, 2023, 12:15:02 PM2/9/23
to OWASP ZAP Developer Group
Hi,
We use zaproxy and we execute `zap.sh -cmd -addonupdate -addonlist -suppinfo` to get the latest plugins.
From my understanding, this is getting GraalVM (i.e. https://github.com/zaproxy/zap-extensions/blob/main/addOns/graaljs/graaljs.gradle.kts) of version `20.2.0`. This particular version is flagged to contain CVE-2022-21449 -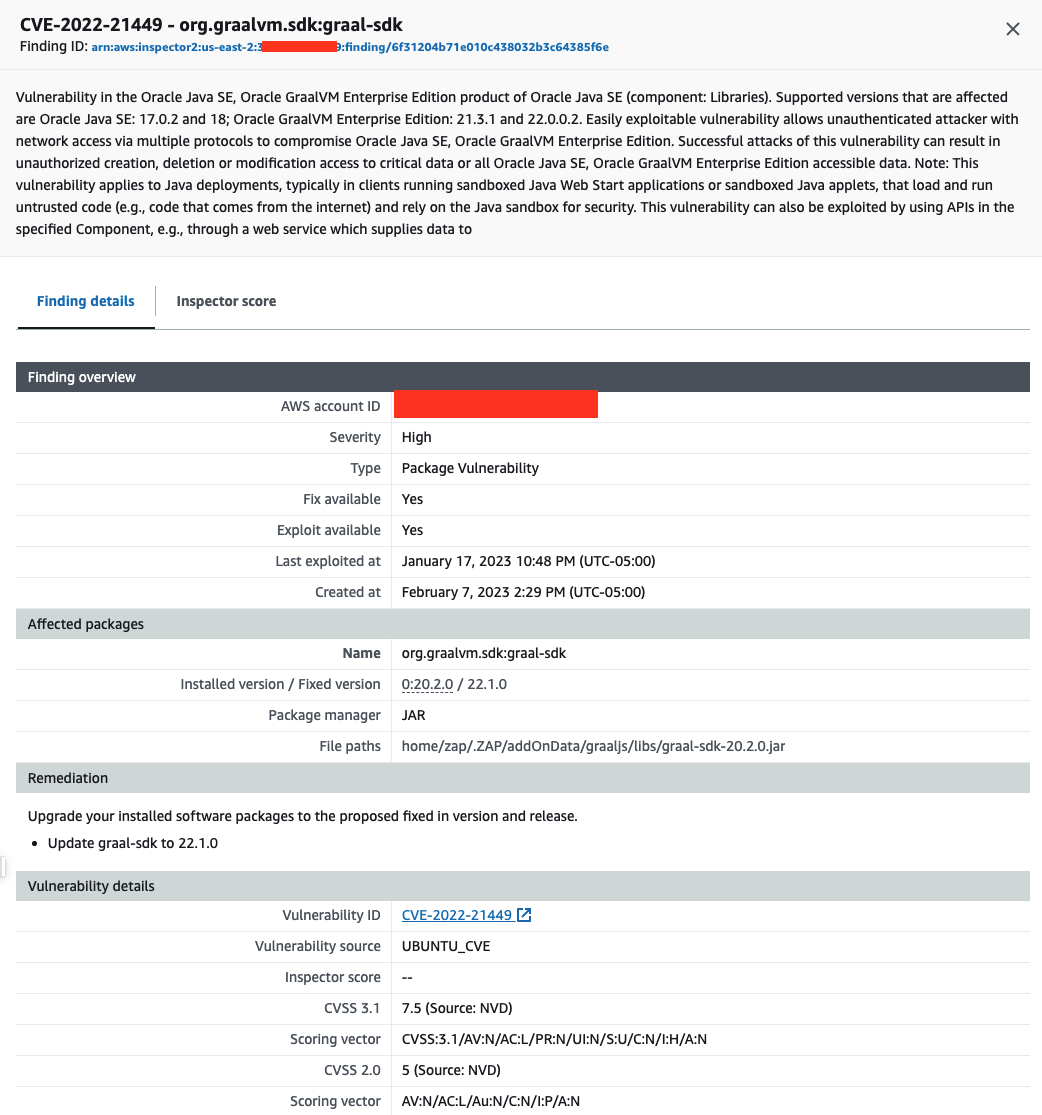
From my understanding, this is getting GraalVM (i.e. https://github.com/zaproxy/zap-extensions/blob/main/addOns/graaljs/graaljs.gradle.kts) of version `20.2.0`. This particular version is flagged to contain CVE-2022-21449 -

Questions -
1. Is zaproxy's usage of GraalVM exposed to this CVE (as described by the CVE)?
1. Is zaproxy's usage of GraalVM exposed to this CVE (as described by the CVE)?
2. If it's exposed, is there a way to disable the features/functionality to avoid the usage described by the CVE?
3. Is there a plan to upgrade the graal-sdk version to 22.1.0 to address the CVE? If so, is there an ETA?
3. Is there a plan to upgrade the graal-sdk version to 22.1.0 to address the CVE? If so, is there an ETA?
Thank you,
Mohit
psiinon
Feb 9, 2023, 12:20:45 PM2/9/23
to OWASP ZAP Developer Group
Hi Mohit,
Thank you for letting us know about this issue - we are investigating it right now and will report back asap.
Cheers,
Simon
psiinon
Feb 9, 2023, 12:28:32 PM2/9/23
to OWASP ZAP Developer Group
From the CVE:
- Note: This vulnerability applies to Java deployments, typically in clients running sandboxed Java Web Start applications or sandboxed Java applets, that load and run untrusted code (e.g., code that comes from the internet) and rely on the Java sandbox for security.
ZAP uses GraalVM for user scripting which runs in ZAP and does not use it to load any code, untrusted or otherwise.
In theory a ZAP user could use it to load untrusted code, but that would be very unwise.
Unless anyone disagrees I think this means it does not impact ZAP.
However we will look at upgrading GraalVM to a more recent version soon.
Many thanks,
Simon
Mohit A. Jampala
Feb 10, 2023, 9:46:56 AM2/10/23
to OWASP ZAP Developer Group
Thank you for the quick response, Simon
Reply all
Reply to author
Forward
0 new messages
