"select your tenant" pop up after Wazuh upgrade
504 views
Skip to first unread message
filip faredge
Aug 13, 2021, 12:14:27 AM8/13/21
to Wazuh mailing list
Hello,
I have recently upgraded my Wazuh single node from 7.10 to 7.10.2 following the official doco ( https://documentation.wazuh.com/current/upgrade-guide/upgrading-wazuh.html )
Now every time a user logs in there is this annoying popup :
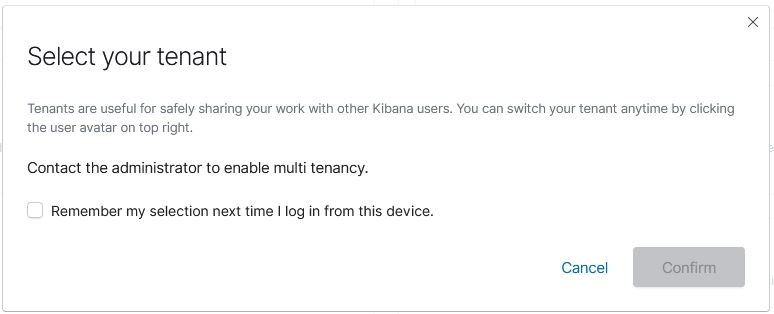
Now every time a user logs in there is this annoying popup :
The "confirm" button is greyed out and the "remember selection" tick does nothing
How can I disable it ?
Do I need to enable the multi tenancy now ?
How can I disable it ?
Do I need to enable the multi tenancy now ?
Regards
Filip
José Fernández
Aug 13, 2021, 5:18:34 AM8/13/21
to Wazuh mailing list
Hello Filip,
This pop-up comes from Kibana 7.10.2 and, it cannot be disabled. You can hide in the majority of cases by enabling the multitenancy and setting a default option.
Example of our kibana.yml:
opendistro_security.multitenancy.enabled: true
opendistro_security.multitenancy.tenants.preferred: ["Private", "Global"]
server.defaultRoute: /app/wazuh?security_tenant=global
This configuration will perform security_tenant=global by default and will avoid the pop-up.
I hope it helps to you, don't hesitate to ask us if you have any doubt.
This pop-up comes from Kibana 7.10.2 and, it cannot be disabled. You can hide in the majority of cases by enabling the multitenancy and setting a default option.
Example of our kibana.yml:
opendistro_security.multitenancy.enabled: true
opendistro_security.multitenancy.tenants.preferred: ["Private", "Global"]
server.defaultRoute: /app/wazuh?security_tenant=global
This configuration will perform security_tenant=global by default and will avoid the pop-up.
I hope it helps to you, don't hesitate to ask us if you have any doubt.
filip faredge
Aug 16, 2021, 8:39:13 PM8/16/21
to Wazuh mailing list
Hi José,
Thank you for your response.
After enabling the multitenancy Kibana would fail to start in my scenario.
I am posting here next steps hopefully this will help someone else in the future
Not sure if this is needed but after reading different forums I enabled during my experiments the following part in in /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/config.yml
config:
dynamic:
do_not_fail_on_forbidden: false
kibana:
# Kibana multitenancy
multitenancy_enabled: true
server_username: admin
#index: '.kibana'
Which did not resolve the issue.
When I checked for listening ports I noticed my kibana listening process on port 443 would not show up.
After much searching I found the relevant error:
["error","plugins","opendistroSecurityKibana"],"pid":14733,"message":"{ Error: Authorization Exception\n at respond (/usr/share/kibana/node_modules/elasticsearch/src/lib/transport.js:349:15)\n at checkRespForFailure (/usr/share/kibana/node_modules/elasticsearch/src/lib/transport.js:306:7)\n at HttpConnector.<anonymous> (/usr/share/kibana/node_modules/elasticsearch/src/lib/connectors/http.js:173:7)\n at IncomingMessage.wrapper (/usr/share/kibana/node_modules/lodash/lodash.js:4949:19)\n at IncomingMessage.emit (events.js:203:15)\n at endReadableNT (_stream_readable.js:1145:12)\n at process._tickCallback (internal/process/next_tick.js:63:19)\n status: 403,\n displayName: 'AuthorizationException',\n message: 'Authorization Exception',\n path: '/_opendistro/_security/tenantinfo',\n query: {},\n body: undefined,\n statusCode: 403,\n response: '',\n toString: [Function],\n toJSON: [Function] }"}
which led me to user permissions.
Not fully understanding the users permissions intricacies between different components of the stack I was trying different things.
What seemed to finally work for me is using the same user in /etc/kibana/kibana.yml and /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/config.yml which is in my case kibanaserver
At some point I had user admin in both kibana.yml and config.yml but the error persisted.
I do not know why admin user did not work but changing to kibanaserver in both location seemed to do the trick.
Jose,
If you don't mind I will pick your brain.
Do you have any comment on the above ?
Do you normally need to edit the /elasticsearch/plugins/opendistro_security/securityconfig/config.yml file or the kibana change alone should have been sufficient ?
Is there any high level documentation for Wazuh explaining the multi tenancy and what can be accomplished with it? All the document I saw are quickly very technical and are not including Wazuh in the examples.
My initial thinking is we have Wazuh agents from different customers reporting to the Wazuh server. Can we use multitenancy so that Customer A can login and see only his X Agents (and its relevant security events/vulnerabilities etc) and customer B sees only his Y agents ?
Kind regards
Filip
filip faredge
Aug 26, 2021, 12:05:42 AM8/26/21
to Wazuh mailing list
Hi,
Maybe other users have any input on this matter ?
Do you normally need to edit the /elasticsearch/plugins/opendistro_security/securityconfig/config.yml file or the kibana change alone should have been sufficient ?
Is there any high level documentation for Wazuh explaining the multi tenancy and what can be accomplished with it? All the document I saw are quickly very technical and are not including Wazuh in the examples.
My initial thinking is we have Wazuh agents from different customers reporting to the Wazuh server. Can we use multitenancy so that Customer A can login and see only his X Agents (and its relevant security events/vulnerabilities etc) and customer B sees only his Y agents ?
Kind regards
Filip
José Fernández
Sep 20, 2021, 10:00:10 AM9/20/21
to Wazuh mailing list
Hello Filip,
Sorry for the late reply. I have been researching that matter. I set up various statements to share with you.
- The kibanaserver user is the default one in OpenDistro default multi-tenant configuration, in the Kibana server configuration too. I assume that this user has specific permissions to this matter rather than the admin user. Anyway, I have tested with wazuh-docker deployment to set up admin in kibana.yml and config.yml of OpenDistro security then all seems to work as expected. Probably you will need to set up additional permissions for the admin user. I will attach my security configuration with images.
- You have to change both files, kibana.yml and config.yml.
- The multi-tenant allows you to split Kibana information/dashboards and information into different working spaces but, it doesn't forbid access to data. The access to the data is managed by Document Level Security (DLS) or roles/indices configuration. To better explain to the tenant will keep different dashboards for different enterprise roles like directors/managers/employees/etc. You can take a look at OpenDistro official documentation to get a detailed explanation https://opendistro.github.io/for-elasticsearch-docs/docs/security/access-control/multi-tenancy/
To summarize, there is no document of multi-tenant with Wazuh because it is a Kibana targeted feature.
Sorry for the late reply. I have been researching that matter. I set up various statements to share with you.
- The kibanaserver user is the default one in OpenDistro default multi-tenant configuration, in the Kibana server configuration too. I assume that this user has specific permissions to this matter rather than the admin user. Anyway, I have tested with wazuh-docker deployment to set up admin in kibana.yml and config.yml of OpenDistro security then all seems to work as expected. Probably you will need to set up additional permissions for the admin user. I will attach my security configuration with images.
- You have to change both files, kibana.yml and config.yml.
- The multi-tenant allows you to split Kibana information/dashboards and information into different working spaces but, it doesn't forbid access to data. The access to the data is managed by Document Level Security (DLS) or roles/indices configuration. To better explain to the tenant will keep different dashboards for different enterprise roles like directors/managers/employees/etc. You can take a look at OpenDistro official documentation to get a detailed explanation https://opendistro.github.io/for-elasticsearch-docs/docs/security/access-control/multi-tenancy/
To summarize, there is no document of multi-tenant with Wazuh because it is a Kibana targeted feature.
0 new messages
