Docker Logs ingestion error
162 views
Skip to first unread message
Dhiraj Ambigapathi
Aug 21, 2023, 5:30:59 AM8/21/23
to Wazuh mailing list
So I've tried multiple blogs to monitor Docker Logs and have failed in getting any right.
wazuh-agent conf

I've a reverse proxy docker, from which I want to extract logs and publish them on wazuh web console. the docker creates the reverse proxy docker logs in /var/lib/docker/container/logs.
Methood 1
I setup Out_format in wazuh_agent to pull docker logs. The Out_format breaks default json parsing, so that I can write a decoder and rules for publishing event.wazuh-agent conf

I checked archives/archieves.log in wazuh manager for the log fetched grom wazuh agent. I did enabled <logall> for this
archive.log

archive.log

Then I wrote decoder and rule to extract and publish event, but it did not publish anything on web console even though The logtest worked.
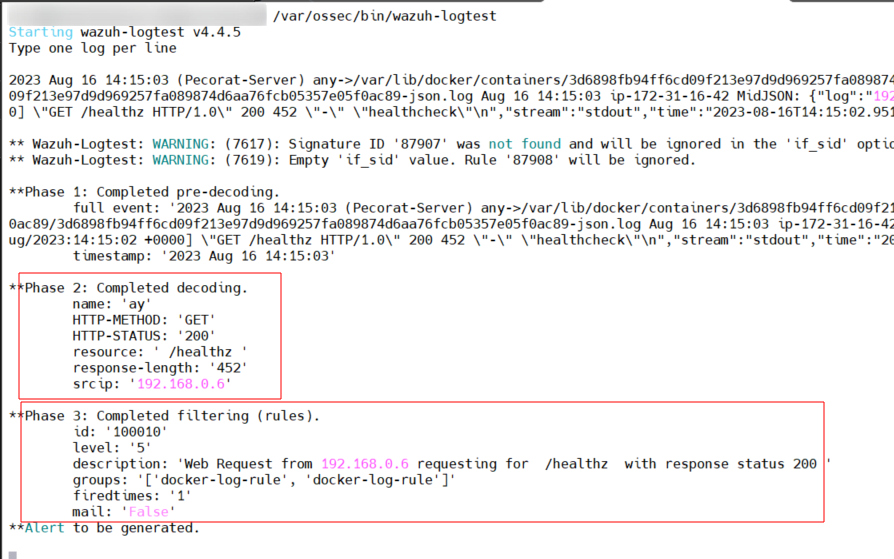

Method 2
I followed following blog docker. But it did not fetch reverse proxy docker logs.
Any help would be much appreciated.
Thanks
I followed following blog docker. But it did not fetch reverse proxy docker logs.
Any help would be much appreciated.
Thanks
victor....@wazuh.com
Aug 22, 2023, 8:34:00 AM8/22/23
to Wazuh mailing list
Hello Dhiraj,
As outlined in the blog post you commented on, when a container is created using the Docker engine, it employs the JSON File logging driver as its default. This method captures logs that can be located at /var/lib/docker/containers/[container-id]/[container-id]-json.log. However, these logs might prove insufficient in identifying the specific container responsible for generating them.
Regarding the localfile configuration, it should not be necessary using of the out_format option. The json logs should be correctly decoded by the default wazuh ruleset. This approach will make your ruleset easier to maintain.
Also, it's pertinent to acknowledge that some warnings have surfaced in the logtest pertaining to your custom ruleset.
Despite all these notes, as you have said, the alert should appear in the dashboard. Did you restart the manager after changing your ruleset?
For the purpose of troubleshooting the issue, could you kindly provide us with your customized decoders and rules, alongside an example of the event? This will help us determine the cause of this problem.
As outlined in the blog post you commented on, when a container is created using the Docker engine, it employs the JSON File logging driver as its default. This method captures logs that can be located at /var/lib/docker/containers/[container-id]/[container-id]-json.log. However, these logs might prove insufficient in identifying the specific container responsible for generating them.
Regarding the localfile configuration, it should not be necessary using of the out_format option. The json logs should be correctly decoded by the default wazuh ruleset. This approach will make your ruleset easier to maintain.
Also, it's pertinent to acknowledge that some warnings have surfaced in the logtest pertaining to your custom ruleset.
Despite all these notes, as you have said, the alert should appear in the dashboard. Did you restart the manager after changing your ruleset?
For the purpose of troubleshooting the issue, could you kindly provide us with your customized decoders and rules, alongside an example of the event? This will help us determine the cause of this problem.
Dhiraj Ambigapathi
Aug 22, 2023, 8:56:15 AM8/22/23
to Wazuh mailing list
Hi Victor,
After spending days on this I came across a blog here. This takes the json as parent decoder as was observed and then uses child decoder to decode it further. I got logs from web app, but I was not able to working parser for mod-security logs. As mentioned before I'm using a reverse proxy docker and I wish to parse web and mod security logs.
I will give the mod security log and can you help me create a working decoder?
Log:
{"log":"{\"transaction\":{\"client_ip\":\"198.199.105.84\",\"time_stamp\":\"Tue Aug 22 12:24:05 2023\",\"server_id\":\"08009b29418b10ad42d8757275cce1b4df950f9a\",\"client_port\":39564,\"host_ip\":\"192.168.0.6\",\"host_port\":443,\"unique_id\":\"169270704533.140418\",\"request\":{\"method\":\"GET\",\"http_version\":1.1,\"uri\":\"/ecp/Current/exporttool/microsoft.exchange.ediscovery.exporttool.application\",\"headers\":{\"Host\":\"18.235.43.100\",\"User-Agent\":\"Mozilla/5.0 zgrab/0.x\",\"Accept\":\"*/*\",\"Accept-Encoding\":\"gzip\"}},\"response\":{\"body\":\"\u003chtml\u003e\\r\\n\u003chead\u003e\u003ctitle\u003e403 Forbidden\u003c/title\u003e\u003c/head\u003e\\r\\n\u003cbody\u003e\\r\\n\u003ccenter\u003e\u003ch1\u003e403 Forbidden\u003c/h1\u003e\u003c/center\u003e\\r\\n\u003chr\u003e\u003ccenter\u003enginx/1.22.1\u003c/center\u003e\\r\\n\u003c/body\u003e\\r\\n\u003c/html\u003e\\r\\n\",\"http_code\":403,\"headers\":{\"Server\":\"nginx/1.22.1\",\"Date\":\"Tue, 22 Aug 2023 12:24:05 GMT\",\"Content-Length\":\"153\",\"Content-Type\":\"text/html\",\"Connection\":\"keep-alive\"}},\"producer\":{\"modsecurity\":\"ModSecurity v3.0.8 (Linux)\",\"connector\":\"ModSecurity-nginx v1.0.3\",\"secrules_engine\":\"Enabled\",\"components\":[\"OWASP_CRS/3.3.4\\\"\"]},\"messages\":[{\"message\":\"Found User-Agent associated with security scanner\",\"details\":{\"match\":\"Matched \\\"Operator `PmFromFile' with parameter `scanners-user-agents.data' against variable `REQUEST_HEADERS:User-Agent' (Value: `Mozilla/5.0 zgrab/0.x' )\",\"reference\":\"o12,5v122,21t:lowercase\",\"ruleId\":\"913100\",\"file\":\"/etc/modsecurity.d/owasp-crs/rules/REQUEST-913-SCANNER-DETECTION.conf\",\"lineNumber\":\"34\",\"data\":\"Matched Data: zgrab found within REQUEST_HEADERS:User-Agent: mozilla/5.0 zgrab/0.x\",\"severity\":\"2\",\"ver\":\"OWASP_CRS/3.3.4\",\"rev\":\"\",\"tags\":[\"modsecurity\",\"application-multi\",\"language-multi\",\"platform-multi\",\"attack-reputation-scanner\",\"paranoia-level/1\",\"OWASP_CRS\",\"capec/1000/118/224/541/310\",\"PCI/6.5.10\"],\"maturity\":\"0\",\"accuracy\":\"0\"}},{\"message\":\"Host header is a numeric IP address\",\"details\":{\"match\":\"Matched \\\"Operator `Rx' with parameter `^[\\\\d.:]+$' against variable `REQUEST_HEADERS:Host' (Value: `18.235.43.100' )\",\"reference\":\"o0,13v96,13\",\"ruleId\":\"920350\",\"file\":\"/etc/modsecurity.d/owasp-crs/rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf\",\"lineNumber\":\"719\",\"data\":\"18.235.43.100\",\"severity\":\"4\",\"ver\":\"OWASP_CRS/3.3.4\",\"rev\":\"\",\"tags\":[\"modsecurity\",\"application-multi\",\"language-multi\",\"platform-multi\",\"attack-protocol\",\"paranoia-level/1\",\"OWASP_CRS\",\"capec/100
0/210/272\",\"PCI/6.5.10\"],\"maturity\":\"0\",\"accuracy\":\"0\"}},{\"message\":\"Inbound Anomaly Score Exceeded (Total Score: 8)\",\"details\":{\"match\":\"Matched \\\"Operator `Ge' with parameter `5' against variable `TX:ANOMALY_SCORE' (Value: `8' )\",\"reference\":\"\",\"ruleId\":\"949110\",\"file\":\"/etc/modsecurity.d/owasp-crs/rules/REQUEST-949-BLOCKING-EVALUATION.conf\",\"lineNumber\":\"81\",\"data\":\"\",\"severity\":\"2\",\"ver\":\"OWASP_CRS/3.3.4\",\"rev\":\"\",\"tags\":[\"modsecurity\",\"application-multi\",\"language-multi\",\"platform-multi\",\"attack-generic\"],\"maturity\":\"0\",\"accuracy\":\"0\"}}]}}\n","stream":"stdout","time":"2023-08-22T12:24:05.085059395Z"}
I will try to make parser in meantime and if I'm successful I'll paste my decoder and rule here.
After spending days on this I came across a blog here. This takes the json as parent decoder as was observed and then uses child decoder to decode it further. I got logs from web app, but I was not able to working parser for mod-security logs. As mentioned before I'm using a reverse proxy docker and I wish to parse web and mod security logs.
I will give the mod security log and can you help me create a working decoder?
Log:
{"log":"{\"transaction\":{\"client_ip\":\"198.199.105.84\",\"time_stamp\":\"Tue Aug 22 12:24:05 2023\",\"server_id\":\"08009b29418b10ad42d8757275cce1b4df950f9a\",\"client_port\":39564,\"host_ip\":\"192.168.0.6\",\"host_port\":443,\"unique_id\":\"169270704533.140418\",\"request\":{\"method\":\"GET\",\"http_version\":1.1,\"uri\":\"/ecp/Current/exporttool/microsoft.exchange.ediscovery.exporttool.application\",\"headers\":{\"Host\":\"18.235.43.100\",\"User-Agent\":\"Mozilla/5.0 zgrab/0.x\",\"Accept\":\"*/*\",\"Accept-Encoding\":\"gzip\"}},\"response\":{\"body\":\"\u003chtml\u003e\\r\\n\u003chead\u003e\u003ctitle\u003e403 Forbidden\u003c/title\u003e\u003c/head\u003e\\r\\n\u003cbody\u003e\\r\\n\u003ccenter\u003e\u003ch1\u003e403 Forbidden\u003c/h1\u003e\u003c/center\u003e\\r\\n\u003chr\u003e\u003ccenter\u003enginx/1.22.1\u003c/center\u003e\\r\\n\u003c/body\u003e\\r\\n\u003c/html\u003e\\r\\n\",\"http_code\":403,\"headers\":{\"Server\":\"nginx/1.22.1\",\"Date\":\"Tue, 22 Aug 2023 12:24:05 GMT\",\"Content-Length\":\"153\",\"Content-Type\":\"text/html\",\"Connection\":\"keep-alive\"}},\"producer\":{\"modsecurity\":\"ModSecurity v3.0.8 (Linux)\",\"connector\":\"ModSecurity-nginx v1.0.3\",\"secrules_engine\":\"Enabled\",\"components\":[\"OWASP_CRS/3.3.4\\\"\"]},\"messages\":[{\"message\":\"Found User-Agent associated with security scanner\",\"details\":{\"match\":\"Matched \\\"Operator `PmFromFile' with parameter `scanners-user-agents.data' against variable `REQUEST_HEADERS:User-Agent' (Value: `Mozilla/5.0 zgrab/0.x' )\",\"reference\":\"o12,5v122,21t:lowercase\",\"ruleId\":\"913100\",\"file\":\"/etc/modsecurity.d/owasp-crs/rules/REQUEST-913-SCANNER-DETECTION.conf\",\"lineNumber\":\"34\",\"data\":\"Matched Data: zgrab found within REQUEST_HEADERS:User-Agent: mozilla/5.0 zgrab/0.x\",\"severity\":\"2\",\"ver\":\"OWASP_CRS/3.3.4\",\"rev\":\"\",\"tags\":[\"modsecurity\",\"application-multi\",\"language-multi\",\"platform-multi\",\"attack-reputation-scanner\",\"paranoia-level/1\",\"OWASP_CRS\",\"capec/1000/118/224/541/310\",\"PCI/6.5.10\"],\"maturity\":\"0\",\"accuracy\":\"0\"}},{\"message\":\"Host header is a numeric IP address\",\"details\":{\"match\":\"Matched \\\"Operator `Rx' with parameter `^[\\\\d.:]+$' against variable `REQUEST_HEADERS:Host' (Value: `18.235.43.100' )\",\"reference\":\"o0,13v96,13\",\"ruleId\":\"920350\",\"file\":\"/etc/modsecurity.d/owasp-crs/rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf\",\"lineNumber\":\"719\",\"data\":\"18.235.43.100\",\"severity\":\"4\",\"ver\":\"OWASP_CRS/3.3.4\",\"rev\":\"\",\"tags\":[\"modsecurity\",\"application-multi\",\"language-multi\",\"platform-multi\",\"attack-protocol\",\"paranoia-level/1\",\"OWASP_CRS\",\"capec/100
0/210/272\",\"PCI/6.5.10\"],\"maturity\":\"0\",\"accuracy\":\"0\"}},{\"message\":\"Inbound Anomaly Score Exceeded (Total Score: 8)\",\"details\":{\"match\":\"Matched \\\"Operator `Ge' with parameter `5' against variable `TX:ANOMALY_SCORE' (Value: `8' )\",\"reference\":\"\",\"ruleId\":\"949110\",\"file\":\"/etc/modsecurity.d/owasp-crs/rules/REQUEST-949-BLOCKING-EVALUATION.conf\",\"lineNumber\":\"81\",\"data\":\"\",\"severity\":\"2\",\"ver\":\"OWASP_CRS/3.3.4\",\"rev\":\"\",\"tags\":[\"modsecurity\",\"application-multi\",\"language-multi\",\"platform-multi\",\"attack-generic\"],\"maturity\":\"0\",\"accuracy\":\"0\"}}]}}\n","stream":"stdout","time":"2023-08-22T12:24:05.085059395Z"}
I will try to make parser in meantime and if I'm successful I'll paste my decoder and rule here.
victor....@wazuh.com
Aug 24, 2023, 4:44:43 AM8/24/23
to Wazuh | Mailing List
Regarding that documentation page, it presents a series of decoders tailored for logs adhering to this particular structure.
**Phase 1: Completed pre-decoding.
full event: '{"log":"192.168.132.1 - - [12/May/2023:14:12:14 +0000] \"GET /users/?id=SELECT+*+FROM+users HTTP/1.1\" 404 153 \"-\" \"curl/7.68.0\" \"-\"\\n\",\"stream\":\"stdout\",\"time\":\"2023-05-12T14:12:14.882936144Z"}'
**Phase 2: Completed decoding.
name: 'web-accesslog-docker'
parent: 'json'
id: '404'
protocol: 'GET'
srcip: '192.168.132.1'
url: '/users/?id=SELECT+*+FROM+users'
Nevertheless, the mod-security logs you've supplied cannot be parsed using this method, as they follow a structure in which a JSON is parsed as a string within the log field of another JSON log. In such a scenario, we are presented with two potential approaches:
1.- You can troubleshoot this situation by creating specific sibling decoders for your fields. Take for example the following decoders as example:
<decoder name="web-sibling">
<parent>json</parent>
<regex>client_ip\\":\\"(\S+)\\"</regex>
<order>client_ip</order>
</decoder>
<decoder name="web-sibling">
<parent>json</parent>
<regex>server_id\\":\\"(\S+)\\"</regex>
<order>server_id</order>
</decoder>
<decoder name="web-sibling">
<parent>json</parent>
<regex>uri\\":\\"(\S+)\\"</regex>
<order>uri</order>
</decoder>
These decoders will gather the URI, server_id, and client_ip values of your logs:
**Phase 1: Completed pre-decoding.
full event: '{"log":"{\"transaction\":{\"client_ip\":\"198.199.105.84...
**Phase 2: Completed decoding.
name: 'json'
client_ip: '198.199.105.84'
server_id: '08009b29418b10ad42d8757275cce1b4df950f9a'
uri: '/ecp/Current/exporttool/microsoft.exchange.ediscovery.exporttool.application'
**Phase 3: Completed filtering (rules).
...
The downside of this approach is that these decoders are difficult to maintain due to the parsing logic included in the log
2.- Change the source of the logs to use plain text or other log format. These will make possible the creation of more readable and maintainable decoders for your ruleset.
If you have any doubts do not hesitate to ask
**Phase 1: Completed pre-decoding.
full event: '{"log":"192.168.132.1 - - [12/May/2023:14:12:14 +0000] \"GET /users/?id=SELECT+*+FROM+users HTTP/1.1\" 404 153 \"-\" \"curl/7.68.0\" \"-\"\\n\",\"stream\":\"stdout\",\"time\":\"2023-05-12T14:12:14.882936144Z"}'
**Phase 2: Completed decoding.
name: 'web-accesslog-docker'
parent: 'json'
id: '404'
protocol: 'GET'
srcip: '192.168.132.1'
url: '/users/?id=SELECT+*+FROM+users'
Nevertheless, the mod-security logs you've supplied cannot be parsed using this method, as they follow a structure in which a JSON is parsed as a string within the log field of another JSON log. In such a scenario, we are presented with two potential approaches:
1.- You can troubleshoot this situation by creating specific sibling decoders for your fields. Take for example the following decoders as example:
<decoder name="web-sibling">
<parent>json</parent>
<regex>client_ip\\":\\"(\S+)\\"</regex>
<order>client_ip</order>
</decoder>
<decoder name="web-sibling">
<parent>json</parent>
<regex>server_id\\":\\"(\S+)\\"</regex>
<order>server_id</order>
</decoder>
<decoder name="web-sibling">
<parent>json</parent>
<regex>uri\\":\\"(\S+)\\"</regex>
<order>uri</order>
</decoder>
These decoders will gather the URI, server_id, and client_ip values of your logs:
**Phase 1: Completed pre-decoding.
full event: '{"log":"{\"transaction\":{\"client_ip\":\"198.199.105.84...
**Phase 2: Completed decoding.
name: 'json'
client_ip: '198.199.105.84'
server_id: '08009b29418b10ad42d8757275cce1b4df950f9a'
uri: '/ecp/Current/exporttool/microsoft.exchange.ediscovery.exporttool.application'
**Phase 3: Completed filtering (rules).
...
The downside of this approach is that these decoders are difficult to maintain due to the parsing logic included in the log
2.- Change the source of the logs to use plain text or other log format. These will make possible the creation of more readable and maintainable decoders for your ruleset.
If you have any doubts do not hesitate to ask
Dhiraj Ambigapathi
Aug 24, 2023, 9:40:40 AM8/24/23
to Wazuh | Mailing List
Thanks soo much, it works. I tried to make regex as specific as possible to avoid conflict in future.
Reply all
Reply to author
Forward
0 new messages
