Vulnerabilities
138 views
Skip to first unread message
m
Jan 26, 2022, 8:24:23 AM1/26/22
to Wazuh mailing list
Hi, I've configured the Vulnerability Detection as is shown in the documentation but I have some alerts that I don't understand.
My manager is the 2.4 version and the client is a Windows 10 21H2 version.
I don't have any vulnerability data since two days ago. These are some of the latest alerts:
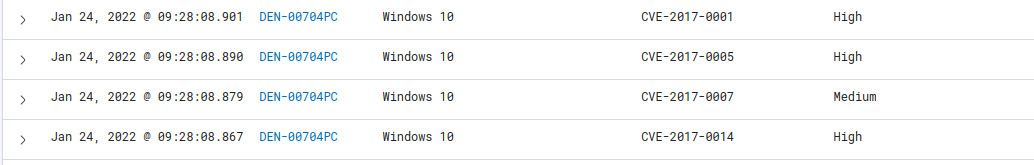
They are supposed to be already patched in my Windows version.
Thank you.
Marcel Kemp
Jan 26, 2022, 11:19:22 AM1/26/22
to m, Wazuh mailing list
Hi m,
Even so, to verify it and to be able to help you better, I would need you to share the following information:
Could you specify the version of the manager again? I will assume that you have version 4.2.0, if not, and it is an old version, I recommend that you update the manager, since the vulnerability detector has been greatly improved and can prevent many false positives.
If it is a recent version of Wazuh, then it is possible that the MSU database is not updated or, the agent does not have a hotfix that fixes these vulnerabilities.
If it is a recent version of Wazuh, then it is possible that the MSU database is not updated or, the agent does not have a hotfix that fixes these vulnerabilities.
And as long as you don't get vulnerabilities from 21H1 agents, it's a known issue that happens on the latest versions of Windows with version 'H', ex: 20H2, 21H1, etc.
The good news is that it has already been fixed in the following PR and will be available when the next version of Wazuh v4.3 is released: https://github.com/wazuh/wazuh/pull/10168
The good news is that it has already been fixed in the following PR and will be available when the next version of Wazuh v4.3 is released: https://github.com/wazuh/wazuh/pull/10168
Even so, to verify it and to be able to help you better, I would need you to share the following information:
- What version of the OS does Wazuh collect on the Windows agent?
- To check that syscollector has synchronized correctly or missing some hotfix, could you show me the list of patches that the agent contains?
- Finally, activate debug mode to get more information about the problem.
To get the patch list and OS version, you can get the information directly from the manager with the following commands (where 001.db is the Windows agent in question):
sqlite3 /var/ossec/queue/db/001.db "select * from sys_hotfixes;"sqlite3 /var/ossec/queue/db/001.db "select * from sys_osinfo;"
Or you can get them from the WUI, heading to the section: Agents -> Select Windows Agent -> Inventory Data.
Where you will find at the beginning information about the agent (from there I need the OS field, as in the following example: OS: Microsoft Windows Server 2019 Datacenter 10.0.17763) and below a list in the Windows updates section with all the patches installed on the agent.
To activate debug mode, open the file /var/ossec/etc/local_internal_options.conf and add the line wazuh_modules.debug = 2 (or use the next command: echo "wazuh_modules.debug=2" >> /var/ossec/etc/local_internal_options.conf ).
Once done, restart wazuh -> /var/ossec/bin/wazuh-control restart, then wait for a full scan to run for Windows agent and finally check the log (ossec.log) again to see the new information.
And to see only the log referring to vulnerability-detector, you can use:
cat /var/ossec/logs/ossec.log | grep vuln
Remember once you get the necessary data, remove the debug line and restart again the manager to avoid disk space problems.
If you have any questions, don't hesitate to ask.
--
You received this message because you are subscribed to the Google Groups "Wazuh mailing list" group.
To unsubscribe from this group and stop receiving emails from it, send an email to wazuh+un...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/wazuh/4cb42634-4aa7-462d-85a0-883e1b7c037en%40googlegroups.com.
m
Jan 27, 2022, 5:50:05 AM1/27/22
to Wazuh mailing list
Hi Marcel,
First of all, thanks for your answer.
Here you have the information you asked for:
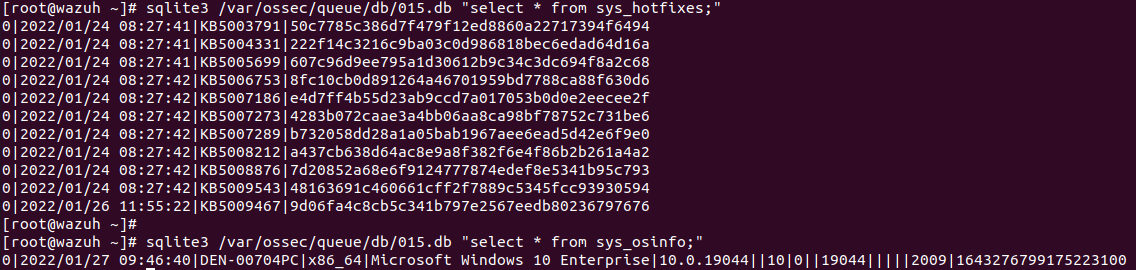
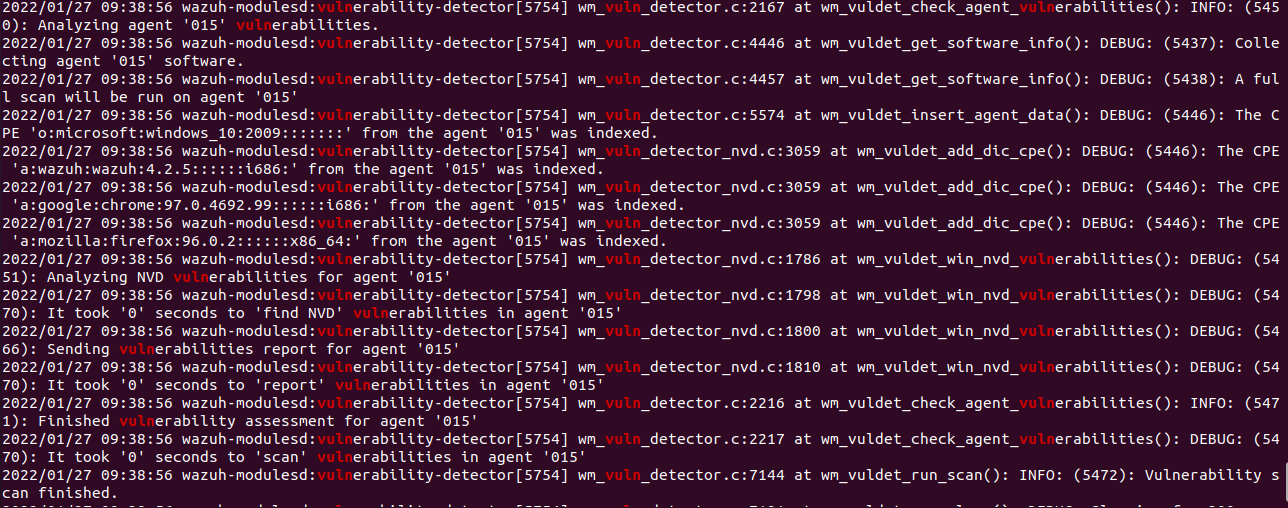
And these are the last 15 log lines after the debug mode activation:
Thank you.
Marcel Kemp
Feb 1, 2022, 4:31:13 AM2/1/22
to m, Wazuh mailing list
Hi again m,
Sorry for the late reply.
Based on the information you've shared, it doesn't appear to have detected the vulnerabilities you shared in the image in the first post (and it appears that the agent tables needed for the scanner are synced correctly).
For the rest, it seems to work as it should, except for the problem of the latest versions of Windows that contain the 'H' in their version, since it can be seen in the debug messages that it tries to match the 2009 version with the NVD, for which does not find any system vulnerability.
And in the case of the agent software packages, it is matching correctly with those that can be translated with the CPE_Helper, but since they are updated, they do not have any vulnerability, so they do not generate any report.
Sorry for the late reply.
Based on the information you've shared, it doesn't appear to have detected the vulnerabilities you shared in the image in the first post (and it appears that the agent tables needed for the scanner are synced correctly).
- Could you check if these vulnerabilities still appear?
For the rest, it seems to work as it should, except for the problem of the latest versions of Windows that contain the 'H' in their version, since it can be seen in the debug messages that it tries to match the 2009 version with the NVD, for which does not find any system vulnerability.
- CPE: 'o:microsoft:windows_10:2009:::::::' from the agent '015'
We are in the testing phase for the release of version 4.3, below I link an issue in case you want to know the progress of the release: https://github.com/wazuh/wazuh/issues/10954
And in the case of the agent software packages, it is matching correctly with those that can be translated with the CPE_Helper, but since they are updated, they do not have any vulnerability, so they do not generate any report.
I hope it helps. If you have any other questions, just ask.
To view this discussion on the web visit https://groups.google.com/d/msgid/wazuh/bddfb9a4-a67c-440e-8f5c-8abb38e4ccfan%40googlegroups.com.
Reply all
Reply to author
Forward
0 new messages
