Skip to first unread message
Vo Duy dot Com
<voduydotcom@gmail.com>May 2, 2022, 9:58:42 AM5/2/22
to [hoidap.voduy.com] Forum Support: Domain, Hosting, VPS, Server...

STEP 1: Install aaPanel (CentOS)
yum install -y wget && wget -O install.sh http://www.aapanel.com/script/install_6.0_en.sh && bash install.sh forum
(Install LAMP: Apache PHP MySQL)
More documentation:
https://forum.aapanel.com/d/9-aapanel-linux-panel-6812-installation-tutorial
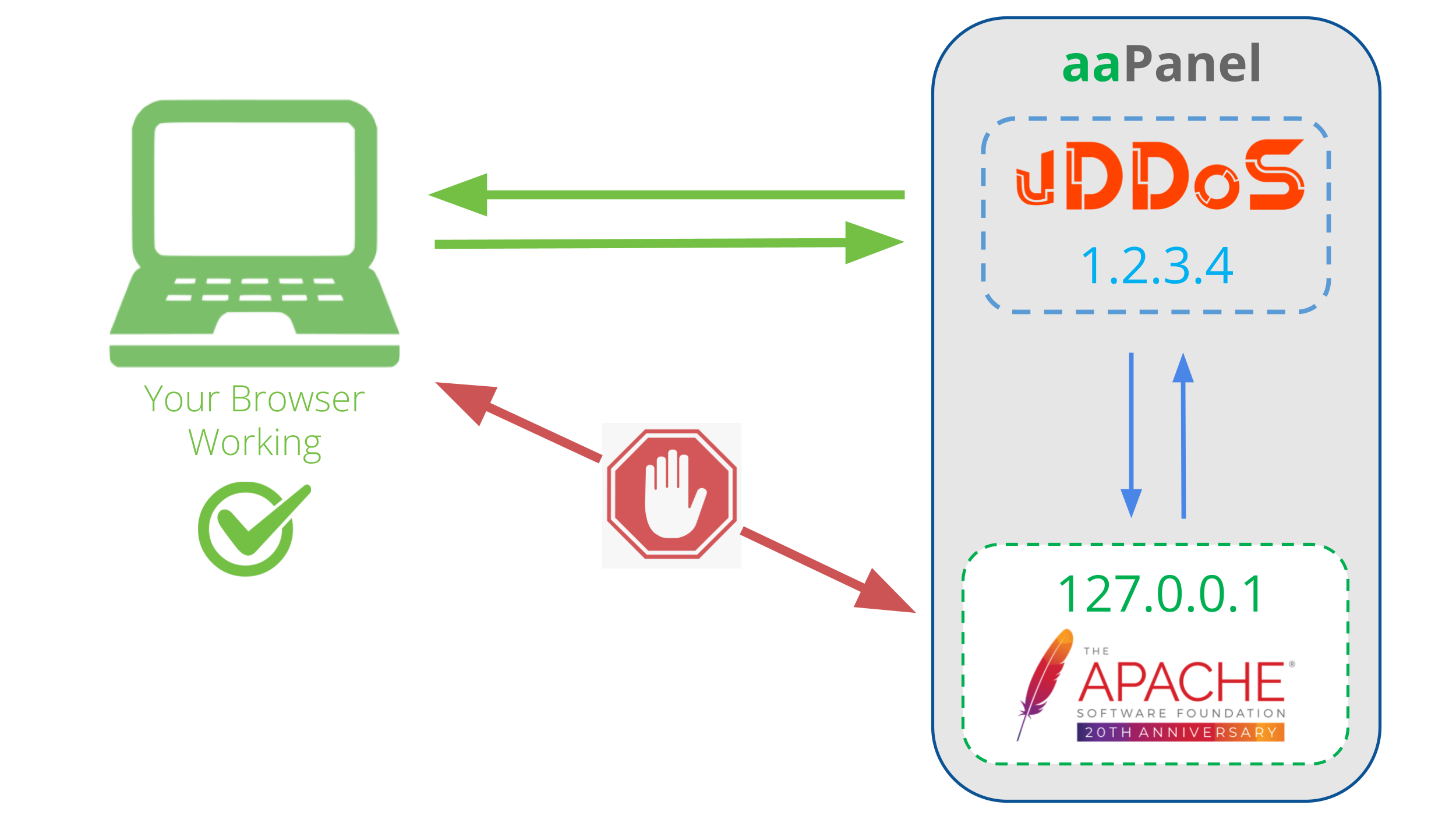
STEP 2: Install vDDoS Proxy Protection
vDDoS Proxy Protection is free software to provide a Reverse Proxy Server HTTP(S) protocols. It act as a Layer 7 Firewall Filter & Mitigate DOS, DDOS, SYN Floods, or HTTP Floods attack to protect your website.
wget https://files.voduy.com/vDDoS-Proxy-Protection/latest.sh ; chmod 700 latest.sh ; bash latest.sh
More documentation:
https://vddos.voduy.com
STEP 3: Change Apache Default IP
By default aaPanel LAMP uses Apache running on IP port 0.0.0.0:80, 0.0.0.0:443. We can reconfigure these Webservers to listen on another IP so that vDDoS can proxy on them.
[NOTE: you need to add at least 1 website (HTTPS) to aaPanel before continuing (you can use self-signed ssl certificate)]
Change Apache Default IP:
cp /www/server/apache/conf/httpd.conf /www/server/apache/conf/httpd.conf.vddosbak
nano /www/server/apache/conf/httpd.conf
Find:
Listen 80
Listen 443
Change to:
Listen 127.0.0.1:80
Listen 127.0.0.1:443
Save & Restart Apache:
service httpd restart
Re-Check Apache port:
[root@aaPanel ~]# netstat -lntup|grep httpd
tcp 0 0 127.0.0.1:443 0.0.0.0:* LISTEN 2738/httpd
tcp 0 0 127.0.0.1:80 0.0.0.0:* LISTEN 2738/httpd
tcp6 0 0 :::888 :::* LISTEN 2738/httpd
STEP 4: Config vDDoS Proxy Protection
For example, the IP Addr of your server is 1.2.3.4:
nano /vddos/conf.d/website.conf
# Website Listen Backend Cache Security SSL-Prikey SSL-CRTkey
default http://1.2.3.4:80 http://127.0.0.1:80 no no no no
default https://1.2.3.4:443 https://127.0.0.1:443 no no /vddos/ssl/your-domain.com.pri /vddos/ssl/your-domain.com.crt
Restart vDDoS service after you have configured:
/usr/bin/vddos restart
STEP 5: Config vDDoS Auto Add
vDDoS Auto Add is a addon support for vDDoS Proxy Protection - Monitor Domains/Aliasdomains/Subdomains in Panel Hosting, Web Server, List Domain, Virtual Host... and automatically add them into the website.conf file.
nano /vddos/auto-add/setting.conf
# Default Setting for vddos-add command:
SSL auto
DNS_sleep 66
DNS_alias_mode no
Cache no
Security no
HTTP_Listen http://1.2.3.4:80
HTTPS_Listen https://1.2.3.4:443
HTTP_Backend http://127.0.0.1:80
HTTPS_Backend https://127.0.0.1:443
Set Crontab:
echo '*/15 * * * * root /usr/bin/vddos-autoadd webserver apache' >> /etc/crontab
STEP 6: Config vDDoS Auto Switch
vDDoS Auto Switch is a addon support for vDDoS Proxy Protection - Automatically identifies overloaded websites and changes their Security Mode.
nano /vddos/auto-switch/setting.conf
# This is the default configuration for "sensor-switch.sh" and "vddos-autoswitch.sh"
hostname="vDDoS Master" #(Name this server, it will show up in Email notifications)
vddos_master_slave_mode="no" #(Turn on "yes" if your system has slave servers, want to sync affter switch like master)
backend_url_check="no" #(Put the URL of the backend. Ex: https://1.1.1.1:8443/ (make sure Backend status response is "200"))
send_notifications="no" #(Turn on "yes" if you want receive notification)
smtp_server="smtps://smtp.gmail.com" #(SMTP Server)
smtp_username="x...@gmail.com" #(Your Mail)
smtp_password="xxxxxxxxxxxxx" #(Get your Apps password for Gmail from https://security.google.com/settings/security/apppasswords)
send_notifications_to="xx...@gmail.com" #(Your Email Address will receive notification)
maximum_allowable_delay_for_backend=2 #(Means: If Backend (status response "200") is slower than 2s, vDDoS will enable challenge mode)
maximum_allowable_delay_for_website=2 #(Means: If Website (status response "200") is slower than 2s, vDDoS will enable challenge mode)
default_switch_mode_not_attack="no" #(Default Mode vDDoS use when it's not under attacked)
default_switch_mode_under_attack="high" #(Default Mode vDDoS use when it's under attack)
default_waiting_time_to_release="60" #(For example 60 minutes, release time from challenge)
Crontab vDDoS Auto Switch:
echo '*/5 * * * * root /usr/bin/vddos-autoswitch checkalldomain high' >> /etc/crontab
echo '0 */3 * * * root /usr/bin/vddos-switch allsite no && /usr/bin/vddos reload' >> /etc/crontab
echo '* * * * * root /usr/bin/vddos-sensor' >> /etc/crontab
More documentation:
https://github.com/duy13/vDDoS-Auto-Switch
Vo Duy dot Com
<voduydotcom@gmail.com>May 2, 2022, 10:08:50 PM5/2/22
to [hoidap.voduy.com] Forum Support: Domain, Hosting, VPS, Server...
Something we will get 520 in CloudFlare when using vDDoS proxy for Apache, the real reason for this problem lies in Apache, Apache being configured with https requiring an http/2 upgrade status in respone http and make CloudFlare not understand, thus CloudFlare has returned error 520 occasionally.
aaPanel:
nano /www/server/apache/conf/httpd.conf
<IfModule http2_module>
ProtocolsHonorOrder On
#Protocols h2 http/1.1
Protocols http/1.1 h2
</IfModule>
Edit:
#Protocols h2 http/1.1
To:
Protocols http/1.1 h2
aaPanel:
nano /www/server/apache/conf/httpd.conf
<IfModule http2_module>
ProtocolsHonorOrder On
#Protocols h2 http/1.1
Protocols http/1.1 h2
</IfModule>
Edit:
#Protocols h2 http/1.1
To:
Protocols http/1.1 h2
Vo Duy dot Com
<voduydotcom@gmail.com>Jul 23, 2022, 11:22:21 AM7/23/22
to [hoidap.voduy.com] Forum Support: Domain, Hosting, VPS, Server...
nano /www/server/apache/conf/extra/mod_remoteip.conf
RemoteIPHeader X-Forwarded-For
RemoteIPInternalProxy 127.0.0.1
RemoteIPInternalProxy 1.2.3.4
#LoadModule remoteip_module modules/mod_remoteip.so
RemoteIPHeader X-Forwarded-For
RemoteIPInternalProxy 127.0.0.1
RemoteIPInternalProxy 1.2.3.4
Vo Duy dot Com
<voduydotcom@gmail.com>Aug 21, 2022, 3:26:10 AM8/21/22
to [hoidap.voduy.com] Forum Support: Domain, Hosting, VPS, Server...
[AntiDDoS] for aaPanel with vDDoS Proxy Protection (LNMP Nginx Version)
STEP 1: Install aaPanel (CentOS)
yum install -y wget && wget -O install.sh http://www.aapanel.com/script/install_6.0_en.sh && bash install.sh forum
(Install LNMP: Nginx PHP MySQL)
More documentation:
https://forum.aapanel.com/d/9-aapanel-linux-panel-6812-installation-tutorial
STEP 2: Install vDDoS Proxy Protection
vDDoS Proxy Protection is free software to provide a Reverse Proxy Server HTTP(S) protocols. It act as a Layer 7 Firewall Filter & Mitigate DOS, DDOS, SYN Floods, or HTTP Floods attack to protect your website.
wget https://files.voduy.com/vDDoS-Proxy-Protection/latest.sh ; chmod 700 latest.sh ; bash latest.sh
More documentation:
https://vddos.voduy.com
STEP 3: Change Nginx Default Port
By default aaPanel LNMP uses Nginx running on IP port 0.0.0.0:80, 0.0.0.0:443. We can reconfigure these Webservers to listen on another IP so that vDDoS can proxy on them.
[NOTE: you need to add at least 1 website (HTTPS) to aaPanel before continuing (you can use self-signed ssl certificate)]
cat /vddos/ssl/your-domain.com.*
Change Nginx Default Port:
cp -r /www/server/panel/vhost/nginx /www/server/panel/vhost/nginx.vddos.bak
Change port for HTTP:
s='80;' ; r='88;'
sed -i "s#$s#$r#g" /www/server/panel/vhost/nginx/*.conf
Change port for HTTPS:
s='443' ; r='999'
sed -i "s#$s#$r#g" /www/server/panel/vhost/nginx/*.conf
Save & Restart Nginx:
service nginx restart
Re-Check Nginx port:
[root@vps-aaPanel ~]# netstat -lntup|grep nginx
tcp 0 0 0.0.0.0:999 0.0.0.0:* LISTEN 24074/nginx: master
tcp 0 0 0.0.0.0:88 0.0.0.0:* LISTEN 24074/nginx: master
tcp 0 0 0.0.0.0:888 0.0.0.0:* LISTEN 24074/nginx: master
default https://0.0.0.0:443 https://1.2.3.4:999 no no /vddos/ssl/your-domain.com.pri /vddos/ssl/your-domain.com.crt
Restart vDDoS service after you have configured:
/usr/bin/vddos restart
STEP 5: Config vDDoS Auto Add
vDDoS Auto Add is a addon support for vDDoS Proxy Protection - Monitor Domains/Aliasdomains/Subdomains in Panel Hosting, Web Server, List Domain, Virtual Host... and automatically add them into the website.conf file.
nano /vddos/auto-add/setting.conf
HTTPS_Listen https://0.0.0.0:443
HTTP_Backend http://1.2.3.4:88
HTTPS_Backend https://1.2.3.4:999
Set Crontab:
echo '*/15 * * * * root /usr/bin/vddos-autoadd webserver nginx' >> /etc/crontab
STEP 1: Install aaPanel (CentOS)
yum install -y wget && wget -O install.sh http://www.aapanel.com/script/install_6.0_en.sh && bash install.sh forum
More documentation:
https://forum.aapanel.com/d/9-aapanel-linux-panel-6812-installation-tutorial
STEP 2: Install vDDoS Proxy Protection
vDDoS Proxy Protection is free software to provide a Reverse Proxy Server HTTP(S) protocols. It act as a Layer 7 Firewall Filter & Mitigate DOS, DDOS, SYN Floods, or HTTP Floods attack to protect your website.
wget https://files.voduy.com/vDDoS-Proxy-Protection/latest.sh ; chmod 700 latest.sh ; bash latest.sh
More documentation:
https://vddos.voduy.com
By default aaPanel LNMP uses Nginx running on IP port 0.0.0.0:80, 0.0.0.0:443. We can reconfigure these Webservers to listen on another IP so that vDDoS can proxy on them.
[NOTE: you need to add at least 1 website (HTTPS) to aaPanel before continuing (you can use self-signed ssl certificate)]
Change Nginx Default Port:
cp -r /www/server/panel/vhost/nginx /www/server/panel/vhost/nginx.vddos.bak
Change port for HTTP:
s='80;' ; r='88;'
sed -i "s#$s#$r#g" /www/server/panel/vhost/nginx/*.conf
Change port for HTTPS:
s='443' ; r='999'
sed -i "s#$s#$r#g" /www/server/panel/vhost/nginx/*.conf
Save & Restart Nginx:
service nginx restart
Re-Check Nginx port:
[root@vps-aaPanel ~]# netstat -lntup|grep nginx
tcp 0 0 0.0.0.0:999 0.0.0.0:* LISTEN 24074/nginx: master
tcp 0 0 0.0.0.0:88 0.0.0.0:* LISTEN 24074/nginx: master
tcp 0 0 0.0.0.0:888 0.0.0.0:* LISTEN 24074/nginx: master
nano /vddos/conf.d/website.conf
# Website Listen Backend Cache Security SSL-Prikey SSL-CRTkey
default http://0.0.0.0:80 http://1.2.3.4:88 no no no no# Website Listen Backend Cache Security SSL-Prikey SSL-CRTkey
default https://0.0.0.0:443 https://1.2.3.4:999 no no /vddos/ssl/your-domain.com.pri /vddos/ssl/your-domain.com.crt
Restart vDDoS service after you have configured:
/usr/bin/vddos restart
STEP 5: Config vDDoS Auto Add
vDDoS Auto Add is a addon support for vDDoS Proxy Protection - Monitor Domains/Aliasdomains/Subdomains in Panel Hosting, Web Server, List Domain, Virtual Host... and automatically add them into the website.conf file.
nano /vddos/auto-add/setting.conf
# Default Setting for vddos-add command:
SSL auto
DNS_sleep 66
DNS_alias_mode no
Cache no
Security no
HTTP_Listen http://0.0.0.0:80SSL auto
DNS_sleep 66
DNS_alias_mode no
Cache no
Security no
HTTPS_Listen https://0.0.0.0:443
HTTP_Backend http://1.2.3.4:88
HTTPS_Backend https://1.2.3.4:999
Set Crontab:
echo '*/15 * * * * root /usr/bin/vddos-autoadd webserver nginx' >> /etc/crontab
Vo Duy dot Com
<voduydotcom@gmail.com>Aug 21, 2022, 3:28:05 AM8/21/22
to [hoidap.voduy.com] Forum Support: Domain, Hosting, VPS, Server...
Set Real IP vDDoS Proxy
Ex your server IP Addr is 1.2.3.4:
nano /www/server/nginx/conf/nginx.conf
....
....
#AAPANEL_FASTCGI_CONF_END
set_real_ip_from 127.0.0.1;
set_real_ip_from 1.2.3.4;
real_ip_header X-Forwarded-For;
real_ip_recursive on;
include mime.types;
....
....
Restart Nginx:
service nginx reload
Ex your server IP Addr is 1.2.3.4:
nano /www/server/nginx/conf/nginx.conf
....
....
#AAPANEL_FASTCGI_CONF_END
set_real_ip_from 127.0.0.1;
set_real_ip_from 1.2.3.4;
real_ip_header X-Forwarded-For;
real_ip_recursive on;
include mime.types;
....
....
Restart Nginx:
service nginx reload
Reply all
Reply to author
Forward
0 new messages
