catastrophe
2 views
Skip to first unread message
worried
Feb 15, 2007, 10:11:13 AM2/15/07
to videoblog...@voxmedia.org
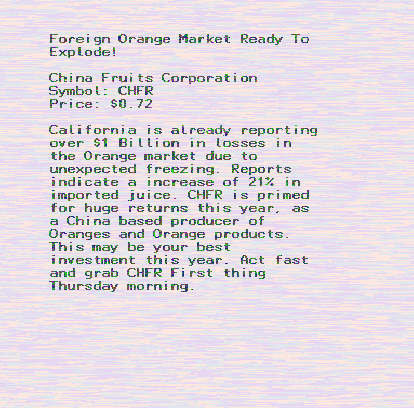
Continue reading: "Can I delete these randomlynamed folders?
The hash functionmost commonly used today is called "SHA1".
A neighbor has kindly named his unprotected wireless network after my own.
Searching is definitely a skill. And yes, while I've positioned this as a "computer related" skill - itreally does apply to anything you might look up on-line, computer related ornot. By the way, could this be what I think it is?
Webmasters click here.
Digg It- Bookmark It on Del.
By putting it in quotes, you tell Google to search for that exact phrase and you cut out a huge number of irrelevant results.
So if you're looking for an erotic experience that will thrill you, inspire you, and affect you deeply, this is your site!
For examplewhen I sign something, I use my private key to do so. Two things:If the signature can be decrypted using the appropriate public key, itmust have come from the person who holds the matching private key.
Effective searching, to me, means first understanding if "any day now"is even the right thing to search for to get to your desired results.
That page is only mentioned here, so I'll know it's from someone who's taken the time to read this far!
well, to be honest I've notyet seen a really compelling reason to upgrade. Your Name:Your Email Address:Where did you hearabout Ask Leo! With this type ofencryption, you generate a key pair. Archives of previous newsletter issuescan be found on the Ask Leo!
A hash is nothing more than acomplex mathematical function.
I'd love to hear what you think.
Spammers have started to use tools to automatically fillin any form they might find on your site, in the hopes that what they post willsomehow get published. Its great to be able to ask a question and actually get an answer! Sometimes, though, spiders can cause problems for web site owners.
Reply all
Reply to author
Forward
0 new messages
