1.14.1 Improper File and Folder Permissions (AppData)
26 views
Skip to first unread message
Alexander Zimmermann
Nov 26, 2021, 11:37:06 AM11/26/21
to TortoiseSVN
Hello all,
I'm in the process of an internal company application certification, one part of it is the TortoiseSVN client.
The test team got the latest official stable 1.14.1.29085-x64, they found 2 low and 1 medium "vulnerability".
I would like to kindly ask if you can have a look at them one by one (will do 3 separate posts, as suggested in the report FAQ), and if there is a possibility to adjust for this.
---
Severity: Medium
Vulnerability: Improper File and Folder Permissions
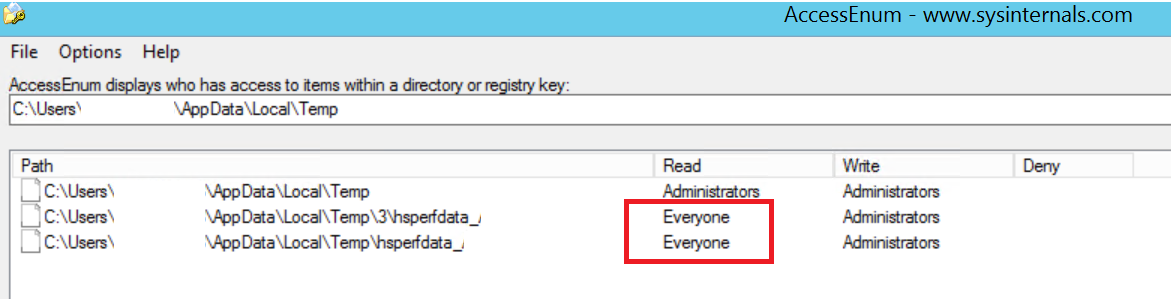
Description: The test team observed that the files and folders of the thick client application have more permissions than required. Attackers can use these excessive files and folders permissions to perform malicious activities. These excessive permissions even lead to DLL hijacking attack.
Screenshot attached
---
Thank you
Alexander
Stefan
Nov 26, 2021, 12:34:52 PM11/26/21
to TortoiseSVN
On Friday, November 26, 2021 at 5:37:06 PM UTC+1 Alexander Zimmermann wrote:
---Severity: MediumVulnerability: Improper File and Folder PermissionsDescription: The test team observed that the files and folders of the thick client application have more permissions than required. Attackers can use these excessive files and folders permissions to perform malicious activities. These excessive permissions even lead to DLL hijacking attack.Screenshot attached
svn/tsvn does not set permissions on those files.
the permissions are automatically inherited from the parent folder. So if those files have more rights than you like, you've set up the folder permissions wrong.
also the name "hsperfdata" indicates that this is not svn/tsvn that creates those. Guess what process most likely is the one who creates those...
Alexander Zimmermann
Nov 29, 2021, 10:30:19 AM11/29/21
to TortoiseSVN
Thank you Stefan for the quick reply. Indeed good catch, that seems to be from Java :-D
Reply all
Reply to author
Forward
0 new messages
