Multiple enterprise applications as IdPs at Azure AD
706 views
Skip to first unread message
Ganesh Arelly
Nov 19, 2021, 3:18:09 PM11/19/21
to SimpleSAMLphp
Hello all,
We have a strange case when trying to setup SimpleSAMLphp as SP and multiple enterprise applications as IdPs at Azure AD.
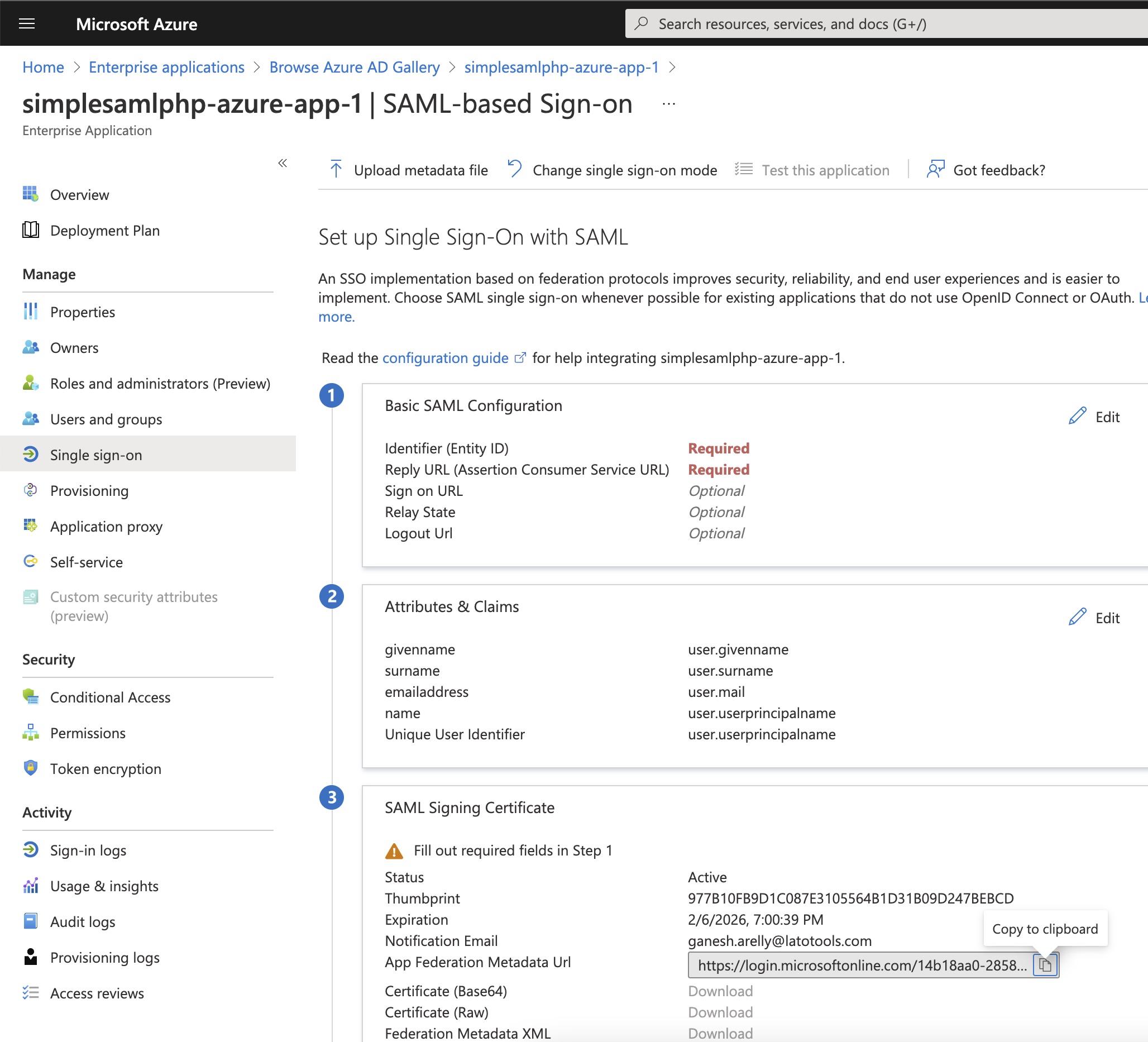
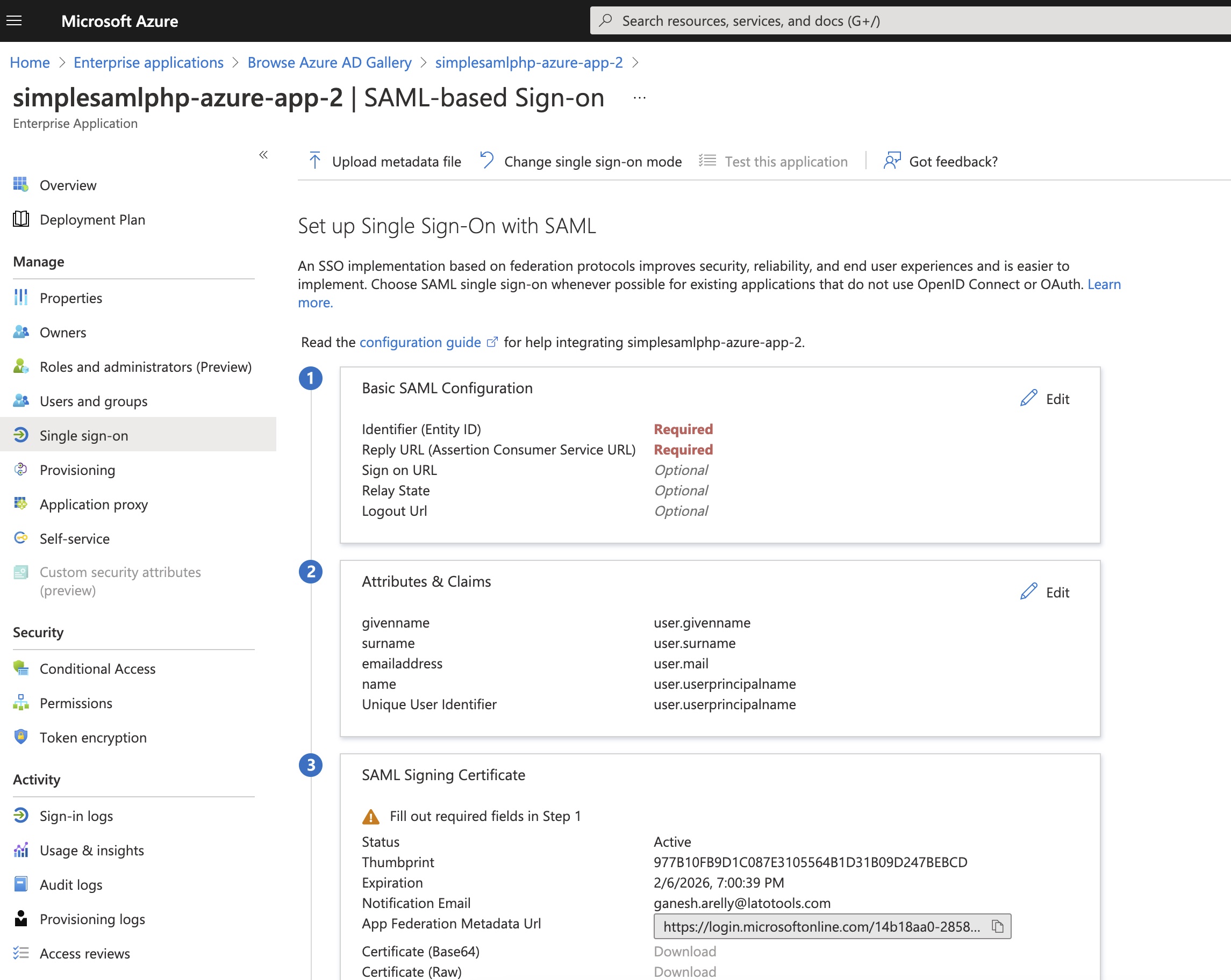
We have 2 enterprise applications at Azure AD. Both apps were given different Identifier (Entity ID) names.Even though both of these apps entity IDs are different, azure metadata url doesn't differentiate the entity ids and also SimpleSAMLphp metadata converter. Metadata urls are pasted here if you would like to convert and view the php code in your local.
simplesamlphp-azure-app-1
Enity ID: simplesamlphp-azure-app-1
Metadata url:
simplesamlphp-azure-app-2
Entity ID: simplesamlphp-azure-app-2
Metadata url:
It's tricky to differentiate these 2 IdPs at authsource. Since both of the app's metadata in saml20-idp-remote.php files contain same idp, there is a conflict.
'app1' => array(
'saml:SP',
'entityID'=> 'app1',
'idp' => 'https://sts.windows.net/14b18aa0-2858-4211-ad45-d6e8e9bece60/',
'discoURL' => null
),
'app2' => array(
'saml:SP',
'entityID'=> 'app2',
'idp' => 'https://sts.windows.net/14b18aa0-2858-4211-ad45-d6e8e9bece60/',
'discoURL' => null
),
The signature is different in those 2 applications metadata and at Azure side, we must have to maintain two groups. Looking for ideas here.
Thanking you guys in advance,
Ganesh Arelly
Peter Schober
Nov 21, 2021, 7:16:26 PM11/21/21
to SimpleSAMLphp
* Ganesh Arelly <ganes...@gmail.com> [2021-11-19 21:18]:
entityID is the same in both cases. So whatever it is you have there
you only have one of it (not two), as far as SAML is concerned.
(That's the extent of what can be said about this without knowing
anything about "Azure" or "enterprise applications" or anything else
that's likely relevant to your problem but not really something this
list can help with: Look at the metadata URLs with cURL or your web
browser: Only one entityID, without even involving SimpleSAMLphp. So
by definition not something SimpleSAMLphp can help with.)
-peter
> SimpleSAMLphp as SP and multiple enterprise applications as IdPs at
> Azure AD.
> We have 2 enterprise applications at Azure AD. Both apps were given
> different Identifier (Entity ID) names. Even though both of these apps
> Azure AD.
> We have 2 enterprise applications at Azure AD. Both apps were given
> entity IDs are different, azure metadata url doesn't differentiate the
> entity ids and also SimpleSAMLphp metadata converter.
The metadata at each URL is the same, modulo signature details. The
> entity ids and also SimpleSAMLphp metadata converter.
entityID is the same in both cases. So whatever it is you have there
you only have one of it (not two), as far as SAML is concerned.
(That's the extent of what can be said about this without knowing
anything about "Azure" or "enterprise applications" or anything else
that's likely relevant to your problem but not really something this
list can help with: Look at the metadata URLs with cURL or your web
browser: Only one entityID, without even involving SimpleSAMLphp. So
by definition not something SimpleSAMLphp can help with.)
-peter
Ganesh Arelly
Nov 22, 2021, 8:11:35 AM11/22/21
to SimpleSAMLphp
Thanks for the message Peter.
Is there a way to do some custom authentication which would be triggered when these kind of SP requests? With that in place, custom code would look for metadata only in specified folders thus no conflicting situations.
Is there a way to do some custom authentication which would be triggered when these kind of SP requests? With that in place, custom code would look for metadata only in specified folders thus no conflicting situations.
Peter Schober
Nov 22, 2021, 8:32:27 AM11/22/21
to SimpleSAMLphp
* Ganesh Arelly <ganes...@gmail.com> [2021-11-22 14:11]:
IDPs? Either way, the answer remains the same: On the SAML level two
IDPs that use the same entityID are the same IDP. That's what entityID
means: It's the granularity to differentiate SAML entities.
No SAML implementation can tell two IDPs apart that use the same
entityID and have the same technical "properties" (protocol endpoints,
keys, e.g. as described in standard SAML 2.0 Metadata) -- not
SimpleSAMLphp, not some other implementation, not using custom code.
You'll need to look at those "enterprise applications" in "Azure" and
change things there (again, no idea what this means or entails),
that's the only place that matters -- at least when using SAML.
Maybe things look differently when using a different protocol, e.g.
SimpleSAMLphp can also be used an an OIDC RP (I think).
-peter
> Thanks for the message Peter.
>
> Is there a way to do some custom authentication which would be triggered
> when these kind of SP requests? With that in place, custom code would look
> for metadata only in specified folders thus no conflicting situations.
I though SimpleSAMLphp is the SP and you're asking about 2 remote
>
> Is there a way to do some custom authentication which would be triggered
> when these kind of SP requests? With that in place, custom code would look
> for metadata only in specified folders thus no conflicting situations.
IDPs? Either way, the answer remains the same: On the SAML level two
IDPs that use the same entityID are the same IDP. That's what entityID
means: It's the granularity to differentiate SAML entities.
No SAML implementation can tell two IDPs apart that use the same
entityID and have the same technical "properties" (protocol endpoints,
keys, e.g. as described in standard SAML 2.0 Metadata) -- not
SimpleSAMLphp, not some other implementation, not using custom code.
You'll need to look at those "enterprise applications" in "Azure" and
change things there (again, no idea what this means or entails),
that's the only place that matters -- at least when using SAML.
Maybe things look differently when using a different protocol, e.g.
SimpleSAMLphp can also be used an an OIDC RP (I think).
-peter
pat...@cirrusidentity.com
Nov 22, 2021, 3:11:13 PM11/22/21
to SimpleSAMLphp
Hi Ganesh,
If you are not using the meta refresh module to pull down the the Azure metadata then you can just create a single entry in your saml20-idp-remote.php file that combines the keys from both Azure Applications.
Peter's suggestion of using OIDC also sounds pretty good.
If you want to go the custom authsource route then you can extend the SP class and override getIdPMetadata() to use the "correct" metadata based on whatever logic your write to know which is the correct metadata.
- Patrick
Ganesh Arelly
Nov 24, 2021, 10:25:24 AM11/24/21
to SimpleSAMLphp
single entry in your saml20-idp-remote.php file that combines the keys from both Azure Applications.
@Patrick, that has helped!
Thanks 🙏
Thanks 🙏
Aaron O
Apr 28, 2025, 4:26:25 PM4/28/25
to SimpleSAMLphp
Hello!
Would you all happen to have an example of how to do this:
single entry in your saml20-idp-remote.php file that combines the keys from both Azure Applications
I've tried but haven't had any luck. Thanks in advance!
Reply all
Reply to author
Forward
0 new messages
