Problem with ACL
34 views
Skip to first unread message
javed...@gmail.com
Nov 10, 2021, 10:08:15 AM11/10/21
to rundeck-discuss
Hello,
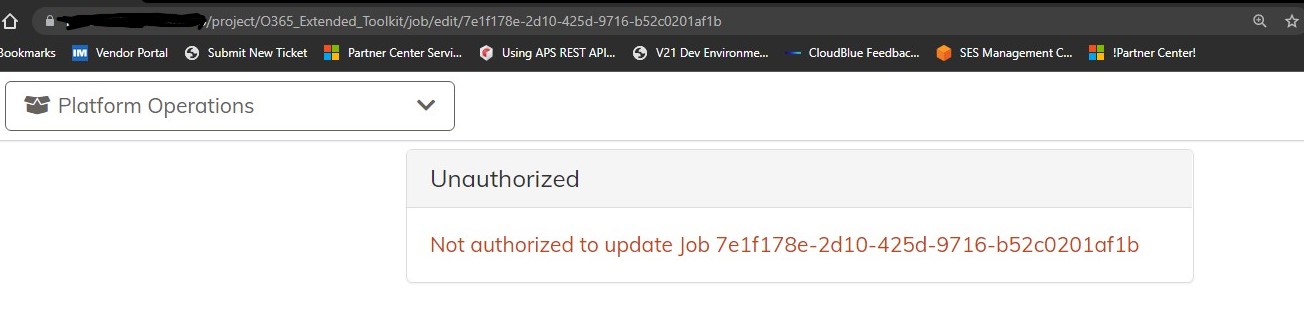
I am trying to create a ACL that will allow the user to view and edit the jobs but not delete them, not manage scm, for all jobs within all projects.
When I try to test this and edit the job I get an error:

Trying to tail the log but there is just too much information printed there for this one attempt to edit the job, can someone share with me what permission is missing?
I see 3 sets of evaluations trigger and trying to find which one is the problem. attached is my ACL file.
The log when trying to edit the job
-------------------------------------------------
Project_ACL:
[2021-11-10T15:58:10,917] WARN authorization.LoggingAuthorization - Evaluating Decision for: res<type:project_acl, name:O365_Extended_Toolkit> subject<Username:test_user Group:poweruser> action<read> env<rundeck:auth:env:application:rundeck>: authorized: false: REJECTED, reason: REJECTED, evaluations: ACLRule</etc/rundeck/poweruser.aclpolicy[1][type:resource][rule: 1]>{'User Application level access control, applies to creating/deleting projects, admin of user profiles, viewing projects and reading system information.' context={application='rundeck'} type='resource' equals , resource={kind=system} for: { group='poweruser'} allow=[read, enable_executions, disable_executions]} REJECTED for action read => REJECTED (0ms)
[2021-11-10T15:58:10,917] WARN authorization.LoggingAuthorization - Evaluating Decision for: res<type:project_acl, name:O365_Extended_Toolkit> subject<Username:test_user Group:poweruser> action<admin> env<rundeck:auth:env:application:rundeck>: authorized: false: REJECTED, reason: REJECTED, evaluations: ACLRule</etc/rundeck/poweruser.aclpolicy[1][type:resource][rule: 1]>{'User Application level access control, applies to creating/deleting projects, admin of user profiles, viewing projects and reading system information.' context={application='rundeck'} type='resource' equals , resource={kind=system} for: { group='poweruser'} allow=[read, enable_executions, disable_executions]} REJECTED for action admin => REJECTED (0ms)
[2021-11-10T15:58:10,918] WARN authorization.LoggingAuthorization - Evaluating Decision for: res<type:project_acl, name:O365_Extended_Toolkit> subject<Username:test_user Group:poweruser> action<read> env<rundeck:auth:env:application:rundeck>: authorized: false: REJECTED, reason: REJECTED, evaluations: ACLRule</etc/rundeck/poweruser.aclpolicy[1][type:resource][rule: 1]>{'User Application level access control, applies to creating/deleting projects, admin of user profiles, viewing projects and reading system information.' context={application='rundeck'} type='resource' equals , resource={kind=system} for: { group='poweruser'} allow=[read, enable_executions, disable_executions]} REJECTED for action read => REJECTED (0ms)
[2021-11-10T15:58:10,918] WARN authorization.LoggingAuthorization - Evaluating Decision for: res<type:project_acl, name:O365_Extended_Toolkit> subject<Username:test_user Group:poweruser> action<admin> env<rundeck:auth:env:application:rundeck>: authorized: false: REJECTED, reason: REJECTED, evaluations: ACLRule</etc/rundeck/poweruser.aclpolicy[1][type:resource][rule: 1]>{'User Application level access control, applies to creating/deleting projects, admin of user profiles, viewing projects and reading system information.' context={application='rundeck'} type='resource' equals , resource={kind=system} for: { group='poweruser'} allow=[read, enable_executions, disable_executions]} REJECTED for action admin => REJECTED (0ms)
Resource:
[2021-11-10T15:58:10,925] WARN authorization.LoggingAuthorization - Evaluating Decision for: res<type:resource, kind:plugin> subject<Username:test_user Group:poweruser> action<read> env<rundeck:auth:env:application:rundeck>: authorized: false: REJECTED, reason: REJECTED, evaluations: ACLRule</etc/rundeck/poweruser.aclpolicy[1][type:resource][rule: 1]>{'User Application level access control, applies to creating/deleting projects, admin of user profiles, viewing projects and reading system information.' context={application='rundeck'} type='resource' equals , resource={kind=system} for: { group='poweruser'} allow=[read, enable_executions, disable_executions]} REJECTED for action read => REJECTED (0ms)
[2021-11-10T15:58:10,925] WARN authorization.LoggingAuthorization - Evaluating Decision for: res<type:resource, kind:plugin> subject<Username:test_user Group:poweruser> action<admin> env<rundeck:auth:env:application:rundeck>: authorized: false: REJECTED, reason: REJECTED, evaluations: ACLRule</etc/rundeck/poweruser.aclpolicy[1][type:resource][rule: 1]>{'User Application level access control, applies to creating/deleting projects, admin of user profiles, viewing projects and reading system information.' context={application='rundeck'} type='resource' equals , resource={kind=system} for: { group='poweruser'} allow=[read, enable_executions, disable_executions]} REJECTED for action admin => REJECTED (0ms)
[2021-11-10T15:58:10,925] WARN authorization.LoggingAuthorization - Evaluating Decision for: res<type:resource, kind:plugin> subject<Username:test_user Group:poweruser> action<install> env<rundeck:auth:env:application:rundeck>: authorized: false: REJECTED, reason: REJECTED, evaluations: ACLRule</etc/rundeck/poweruser.aclpolicy[1][type:resource][rule: 1]>{'User Application level access control, applies to creating/deleting projects, admin of user profiles, viewing projects and reading system information.' context={application='rundeck'} type='resource' equals , resource={kind=system} for: { group='poweruser'} allow=[read, enable_executions, disable_executions]} REJECTED for action install => REJECTED (0ms)
[2021-11-10T15:58:10,925] WARN authorization.LoggingAuthorization - Evaluating Decision for: res<type:resource, kind:plugin> subject<Username:test_user Group:poweruser> action<admin> env<rundeck:auth:env:application:rundeck>: authorized: false: REJECTED, reason: REJECTED, evaluations: ACLRule</etc/rundeck/poweruser.aclpolicy[1][type:resource][rule: 1]>{'User Application level access control, applies to creating/deleting projects, admin of user profiles, viewing projects and reading system information.' context={application='rundeck'} type='resource' equals , resource={kind=system} for: { group='poweruser'} allow=[read, enable_executions, disable_executions]} REJECTED for action admin => REJECTED (0ms)
System:
[2021-11-10T15:58:10,925] WARN authorization.LoggingAuthorization - Evaluating Decision for: res<kind:system, type:resource> subject<Username:test_user Group:poweruser> action<admin> env<rundeck:auth:env:application:rundeck>: authorized: false: REJECTED, reason: REJECTED, evaluations: ACLRule</etc/rundeck/poweruser.aclpolicy[1][type:resource][rule: 1]>{'User Application level access control, applies to creating/deleting projects, admin of user profiles, viewing projects and reading system information.' context={application='rundeck'} type='resource' equals , resource={kind=system} for: { group='poweruser'} allow=[read, enable_executions, disable_executions]} REJECTED for action admin => REJECTED (0ms)
[2021-11-10T15:58:10,925] WARN authorization.LoggingAuthorization - Evaluating Decision for: res<kind:system, type:resource> subject<Username:test_user Group:poweruser> action<admin> env<rundeck:auth:env:application:rundeck>: authorized: false: REJECTED, reason: REJECTED, evaluations: ACLRule</etc/rundeck/poweruser.aclpolicy[1][type:resource][rule: 1]>{'User Application level access control, applies to creating/deleting projects, admin of user profiles, viewing projects and reading system information.' context={application='rundeck'} type='resource' equals , resource={kind=system} for: { group='poweruser'} allow=[read, enable_executions, disable_executions]} REJECTED for action admin => REJECTED (0ms)
[2021-11-10T15:58:10,925] WARN authorization.LoggingAuthorization - Evaluating Decision for: res<kind:system, type:resource> subject<Username:test_user Group:poweruser> action<admin> env<rundeck:auth:env:application:rundeck>: authorized: false: REJECTED, reason: REJECTED, evaluations: ACLRule</etc/rundeck/poweruser.aclpolicy[1][type:resource][rule: 1]>{'User Application level access control, applies to creating/deleting projects, admin of user profiles, viewing projects and reading system information.' context={application='rundeck'} type='resource' equals , resource={kind=system} for: { group='poweruser'} allow=[read, enable_executions, disable_executions]} REJECTED for action admin => REJECTED (0ms)
[2021-11-10T15:58:10,926] WARN authorization.LoggingAuthorization - Evaluating Decision for: res<kind:system, type:resource> subject<Username:test_user Group:poweruser> action<admin> env<rundeck:auth:env:application:rundeck>: authorized: false: REJECTED, reason: REJECTED, evaluations: ACLRule</etc/rundeck/poweruser.aclpolicy[1][type:resource][rule: 1]>{'User Application level access control, applies to creating/deleting projects, admin of user profiles, viewing projects and reading system information.' context={application='rundeck'} type='resource' equals , resource={kind=system} for: { group='poweruser'} allow=[read, enable_executions, disable_executions]} REJECTED for action admin => REJECTED (0ms)
rac...@rundeck.com
Nov 10, 2021, 2:49:15 PM11/10/21
to rundeck-discuss
Hi Osman,
Could you try with the following ACL? (just change the project, job and user name)
description: project context.
context:
project: ProjectEXAMPLE
for:
resource:
- allow: [run,read]
job:
- equals:
name: JobA
allow: [read,update]
node:
- allow: [read]
by:
username: user
---
description: app context.
context:
application: 'rundeck'
for:
project:
- match:
name: ProjectEXAMPLE
allow: [read]
storage:
- allow: [read]
by:
username: user
Feel free to modify it.
Regards!
javed...@gmail.com
Nov 10, 2021, 5:56:56 PM11/10/21
to rundeck...@googlegroups.com
Hello,
This works but isn't it possible to use a wildcard regex in the job name? I want the user to be able to edit any job but not delete it. Otherwise I have to specify each job by name.
--
You received this message because you are subscribed to a topic in the Google Groups "rundeck-discuss" group.
To unsubscribe from this topic, visit https://groups.google.com/d/topic/rundeck-discuss/m1oEGUNdoJQ/unsubscribe.
To unsubscribe from this group and all its topics, send an email to rundeck-discu...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/rundeck-discuss/7930543c-73bb-4aad-b205-afc35c423434n%40googlegroups.com.
javed...@gmail.com
Nov 10, 2021, 6:20:31 PM11/10/21
to rundeck...@googlegroups.com
Hello,
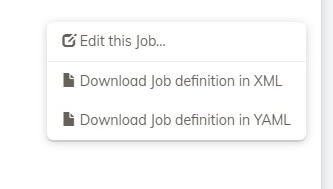
There is a challenge here, if I allow [read,update] it also allows downloading the job definition also.
If I remove "read" the "edit this job..." button shows but I am not allowed to edit.
Is there a way to allow user to edit the job but prevent download of definitions?

```
description: Allow Updating Specific Jobs along with running others
context:
project: '.*'
context:
project: '.*'
for:
resource:
- allow: [run,read]
job:
- allow: [view,run,runAs,kill,killAs]
- equals:
name: 'Job A'
allow: [read,update]
- equals:
name: 'Job B'
- equals:
name: 'Job A'
allow: [read,update]
- equals:
name: 'Job B'
allow: [read,update]
node:
- allow: [read]
by:
group: poweruser
---
description: app context.
context:
application: 'rundeck'
for:
project:
- match:
name: '.*'
allow: [read]
storage:
- allow: [read]
by:
group: poweruser
```
rac...@rundeck.com
Nov 11, 2021, 8:04:01 AM11/11/21
to rundeck-discuss
Hi Osman,
The "download" options are linked with the "view" action, here is a related enhancement request, please add your use case to the thread.
Greetings!
Reply all
Reply to author
Forward
0 new messages
