Rundeck how to do a Microsoft LDAP authetication test
992 views
Skip to first unread message
Diego Alvarez
Jan 17, 2023, 5:43:56 PM1/17/23
to rundeck-discuss
Dear
Looking for a way to test LDAP authentication with a Microsoft LDAP. I have installed Rundeck 4.7.0 on Ubuntu 20.04 lts.
I have tried to setup multiauth and i need to do a test, like the example with war (java -Drundeck.jaaslogin=true -Dloginmodule.conf.name=/etc/rundeck/jaas-multi-auth.conf -Dloginmodule.name=multiauth -jar rundeck-4.9.0-20230111.war --testauth).
My java version:
java -version
openjdk version "11.0.16" 2022-07-19
OpenJDK Runtime Environment (build 11.0.16+8-post-Ubuntu-0ubuntu120.04)
OpenJDK 64-Bit Server VM (build 11.0.16+8-post-Ubuntu-0ubuntu120.04, mixed mode, sharing)
openjdk version "11.0.16" 2022-07-19
OpenJDK Runtime Environment (build 11.0.16+8-post-Ubuntu-0ubuntu120.04)
OpenJDK 64-Bit Server VM (build 11.0.16+8-post-Ubuntu-0ubuntu120.04, mixed mode, sharing)
Thanks in advanced for the help
Best regards.
rac...@rundeck.com
Jan 17, 2023, 5:50:49 PM1/17/23
to rundeck-discuss
Diego Alvarez
Jan 23, 2023, 2:10:35 PM1/23/23
to rundeck-discuss
Thank you for your reply. I already see the command on the rundeck guide.
But i believe it should be different for an install on Debian derived system installation.
If i try to use the command:
But i believe it should be different for an install on Debian derived system installation.
If i try to use the command:
"
java -Drundeck.jaaslogin=true -Dloginmodule.conf.name=jaas-loginmodule.conf -Dloginmodule.name=ldap -jar rundeck-4.9.0-20230111.war --testauth
Error: Unable to access jarfile rundeck-4.9.0-20230111.war
Error: Unable to access jarfile rundeck-4.9.0-20230111.war
"
same result if i add "sudo" before the command.
rac...@rundeck.com
Jan 23, 2023, 2:18:51 PM1/23/23
to rundeck-discuss
Hi Diego,
In Debian/Ubuntu-based systems you need to create or edit the /etc/default/rundeckd file and then, add the LDAP parameters, e.g:
RDECK_JVM_OPTS="-Drundeck.jaaslogin=true \
-Djava.security.auth.login.config=/etc/rundeck/jaas-ldap.conf \
-Dloginmodule.name=ldap"
-Djava.security.auth.login.config=/etc/rundeck/jaas-ldap.conf \
-Dloginmodule.name=ldap"
This process is explained here.
To test directly on the war file, the war file is located at /var/lib/rundeck/bootstrap/ path.
Regards!
Diego Alvarez
Jan 27, 2023, 4:01:27 PM1/27/23
to rundeck-discuss
Dear
/etc/default/rundeckd
I managed to get LDAP working. But only with port 389. I have already added ad cert to the trusted repo. Also try adding
RDECK_JVM_OPTS="-Drundeck.jaaslogin=true \
-Djava.security.auth.login.config=/etc/rundeck/jaas-"the-name-of-my-jaas-file".conf \
-Dloginmodule.name="the-name-of-my-login-module-in-jaas-file" \
-Djavax.net.ssl.trustStore=/path/to/your/truststore"
to
/etc/default/rundeckd
.
The error we see in service log, if we put into jaas config 636 port, is this:
"ERROR
jaas.JettyCachingLdapLoginModule - Naming error"
JAAS file:
"
multiauth {
com.dtolabs.rundeck.jetty.jaas.JettyCachingLdapLoginModule sufficient
debug="true"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
providerUrl="ldap://MY-AD:389"
bindDn="CN=NN ,CN=Users,DC=MINE,DC=local"
bindPassword="PASS"
authenticationMethod="simple"
forceBindingLogin="true"
userBaseDn="dc= MINE ,dc= local "
userRdnAttribute="sAMAccountName"
userIdAttribute="sAMAccountName"
userPasswordAttribute="unicodePwd"
userObjectClass="user"
roleBaseDn=" DC=MINE,DC=local "
roleNameAttribute="cn"
roleMemberAttribute="member"
roleObjectClass="group"
cacheDurationMillis="300000"
reportStatistics="true";
org.eclipse.jetty.plus.jaas.spi.PropertyFileLoginModule required
debug="true"
useFirstPass="true"
file="/etc/rundeck/realm.properties";
};
com.dtolabs.rundeck.jetty.jaas.JettyCachingLdapLoginModule sufficient
debug="true"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
providerUrl="ldap://MY-AD:389"
bindDn="CN=NN ,CN=Users,DC=MINE,DC=local"
bindPassword="PASS"
authenticationMethod="simple"
forceBindingLogin="true"
userBaseDn="dc= MINE ,dc= local "
userRdnAttribute="sAMAccountName"
userIdAttribute="sAMAccountName"
userPasswordAttribute="unicodePwd"
userObjectClass="user"
roleBaseDn=" DC=MINE,DC=local "
roleNameAttribute="cn"
roleMemberAttribute="member"
roleObjectClass="group"
cacheDurationMillis="300000"
reportStatistics="true";
org.eclipse.jetty.plus.jaas.spi.PropertyFileLoginModule required
debug="true"
useFirstPass="true"
file="/etc/rundeck/realm.properties";
};
"
Any ideas?
Suggestion are taken.
Does any one has an example with for jaas file with 636?
Thanks in advanced.
Best regards.
Diego Alvarez
Jan 30, 2023, 10:34:35 AM1/30/23
to rundeck-discuss
Dear
Thank you for your answer.
Already added sudo
keytool -import -alias "AD name that matches the certificate" -file
"file created with add cert info".crt -keystore $JAVA_HOME/lib/security/cacerts -storepass
changeit.
The file sample appears to be for Open LDAP, we are using Microsoft. But it seems that the only difference between your sample and mine is the port (389 to 636).
As a mentioned before the error "ERROR jaas.JettyCachingLdapLoginModule - Naming error", is what trouble us. Is there any way to get more information?
Do you have a sample file with 636 port, for Windows server LDAP?
In this explaination there is a reference to use war to test the connection (even in ubuntu). Do you if there is an example for that ?
"
In Debian/Ubuntu-based systems you need to create or edit the /etc/default/rundeckd file and then, add the LDAP parameters, e.g:
RDECK_JVM_OPTS="-Drundeck.jaaslogin=true \
-Djava.security.auth.login.config=/etc/rundeck/jaas-ldap.conf \
-Dloginmodule.name=ldap"
-Djava.security.auth.login.config=/etc/rundeck/jaas-ldap.conf \
-Dloginmodule.name=ldap"
This process is explained here.
To test directly on the war file, the war file is located at /var/lib/rundeck/bootstrap/ path.
"
Thank you.
Best regards.
rac...@rundeck.com
Jan 30, 2023, 2:51:16 PM1/30/23
to rundeck-discuss
Hi Diego,
Could you post the full service.log content at the moment of trying to log in to take a look?
Regards.
Kai E.
Jan 31, 2023, 3:34:30 AM1/31/23
to rundeck-discuss
Hi Diego,
userRdnAttribute="sAMAccountName"
userIdAttribute="sAMAccountName"
userPasswordAttribute="unicodePwd"
userObjectClass="user"
this config is working for us with LDAPS on Port 636.
Have you checked if port 636 is connectable?
Have you checked if port 636 is connectable?
curl -v telnet://ldap-server:636
JAAS-File:
activedirectory {
com.dtolabs.rundeck.jetty.jaas.JettyCachingLdapLoginModule required
debug="true"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
providerUrl="ldaps://ldap.domain.com"
bindDn="bind...@domain.com"
bindPassword="xxxxxxxxx"
authenticationMethod="simple"
forceBindingLogin="true"
userBaseDn="OU=Users,DC=domain,DC=com"
com.dtolabs.rundeck.jetty.jaas.JettyCachingLdapLoginModule required
debug="true"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
providerUrl="ldaps://ldap.domain.com"
bindDn="bind...@domain.com"
bindPassword="xxxxxxxxx"
authenticationMethod="simple"
forceBindingLogin="true"
userBaseDn="OU=Users,DC=domain,DC=com"
userRdnAttribute="sAMAccountName"
userIdAttribute="sAMAccountName"
userPasswordAttribute="unicodePwd"
userObjectClass="user"
roleBaseDn="OU=Resource Groups,DC=domain,DC=com"
roleNameAttribute="cn"
roleMemberAttribute="member:1.2.840.113556.1.4.1941:"
roleObjectClass="group"
roleSearchSubtree="true"
cacheDurationMillis="300000"
reportStatistics="true";
};
Regards,
Kai
roleNameAttribute="cn"
roleMemberAttribute="member:1.2.840.113556.1.4.1941:"
roleObjectClass="group"
roleSearchSubtree="true"
cacheDurationMillis="300000"
reportStatistics="true";
};
Regards,
Kai
Diego Alvarez
Jan 31, 2023, 9:32:34 AM1/31/23
to rundeck-discuss
Dear
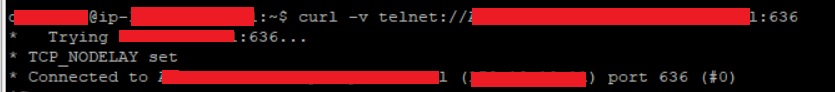
We added the certificate the first with a request to ad on 636.
We also test the curl

This is the log, from the moment we try to connect to LDAP, setting jaas with port 636
"
[2023-01-31T14:22:44,618] ERROR jaas.JettyCachingLdapLoginModule - Naming error
javax.naming.NamingException: LDAP connection has been closed
at com.sun.jndi.ldap.LdapRequest.getReplyBer(LdapRequest.java:133) ~[?:?]
at com.sun.jndi.ldap.Connection.readReply(Connection.java:443) ~[?:?]
at com.sun.jndi.ldap.LdapClient.ldapBind(LdapClient.java:365) ~[?:?]
at com.sun.jndi.ldap.LdapClient.authenticate(LdapClient.java:214) ~[?:?]
at com.sun.jndi.ldap.LdapCtx.connect(LdapCtx.java:2895) ~[?:?]
at com.sun.jndi.ldap.LdapCtx.<init>(LdapCtx.java:348) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getLdapCtxFromUrl(LdapCtxFactory.java:262) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getUsingURL(LdapCtxFactory.java:226) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getUsingURLs(LdapCtxFactory.java:280) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getLdapCtxInstance(LdapCtxFactory.java:185) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getInitialContext(LdapCtxFactory.java:115) ~[?:?]
at javax.naming.spi.NamingManager.getInitialContext(NamingManager.java:730) ~[?:?]
at javax.naming.InitialContext.getDefaultInitCtx(InitialContext.java:305) ~[?:?]
at javax.naming.InitialContext.init(InitialContext.java:236) ~[?:?]
at javax.naming.InitialContext.<init>(InitialContext.java:208) ~[?:?]
at javax.naming.directory.InitialDirContext.<init>(InitialDirContext.java:101) ~[?:?]
at com.dtolabs.rundeck.jetty.jaas.JettyCachingLdapLoginModule.initialize(JettyCachingLdapLoginModule.java:916) ~[classes!/:?]
at javax.security.auth.login.LoginContext.invoke(LoginContext.java:737) ~[?:?]
at javax.security.auth.login.LoginContext$4.run(LoginContext.java:672) ~[?:?]
at javax.security.auth.login.LoginContext$4.run(LoginContext.java:670) ~[?:?]
at java.security.AccessController.doPrivileged(Native Method) ~[?:?]
at javax.security.auth.login.LoginContext.invokePriv(LoginContext.java:670) ~[?:?]
at javax.security.auth.login.LoginContext.login(LoginContext.java:581) ~[?:?]
at org.springframework.security.authentication.jaas.AbstractJaasAuthenticationProvider.authenticate(AbstractJaasAuthenticationProvider.java:173) ~[spring-security-core-5.6.1.jar!/:5.6.1]
at org.rundeck.security.RundeckJaasAuthenticationProvider.super$2$authenticate(RundeckJaasAuthenticationProvider.groovy) ~[classes!/:?]
at jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method) ~[?:?]
at jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62) ~[?:?]
at jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) ~[?:?]
at java.lang.reflect.Method.invoke(Method.java:566) ~[?:?]
at org.codehaus.groovy.reflection.CachedMethod.invoke(CachedMethod.java:107) ~[groovy-3.0.9.jar!/:3.0.9]
at groovy.lang.MetaMethod.doMethodInvoke(MetaMethod.java:323) ~[groovy-3.0.9.jar!/:3.0.9]
at groovy.lang.MetaClassImpl.invokeMethod(MetaClassImpl.java:1268) ~[groovy-3.0.9.jar!/:3.0.9]
at org.codehaus.groovy.runtime.ScriptBytecodeAdapter.invokeMethodOnSuperN(ScriptBytecodeAdapter.java:144) ~[groovy-3.0.9.jar!/:3.0.9]
at org.rundeck.security.RundeckJaasAuthenticationProvider.authenticate(RundeckJaasAuthenticationProvider.groovy:39) ~[classes!/:?]
at org.springframework.security.authentication.ProviderManager.authenticate(ProviderManager.java:182) ~[spring-security-core-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter.attemptAuthentication(UsernamePasswordAuthenticationFilter.java:85) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at grails.plugin.springsecurity.web.authentication.GrailsUsernamePasswordAuthenticationFilter.attemptAuthentication(GrailsUsernamePasswordAuthenticationFilter.groovy:53) ~[spring-security-core-5.0.0-plain.jar!/:?]
at org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter.doFilter(AbstractAuthenticationProcessingFilter.java:223) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter.doFilter(AbstractAuthenticationProcessingFilter.java:213) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:336) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at grails.plugin.springsecurity.web.authentication.logout.MutableLogoutFilter.doFilter(MutableLogoutFilter.groovy:64) ~[spring-security-core-5.0.0-plain.jar!/:?]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:336) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:110) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:80) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:336) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at grails.plugin.springsecurity.web.SecurityRequestHolderFilter.doFilter(SecurityRequestHolderFilter.groovy:58) ~[spring-security-core-5.0.0-plain.jar!/:?]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:336) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:211) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:183) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.eclipse.jetty.servlet.FilterHolder.doFilter(FilterHolder.java:193) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler$Chain.doFilter(ServletHandler.java:1626) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.grails.web.servlet.mvc.GrailsWebRequestFilter.doFilterInternal(GrailsWebRequestFilter.java:77) ~[grails-web-mvc-5.1.9.jar!/:5.1.9]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.eclipse.jetty.servlet.FilterHolder.doFilter(FilterHolder.java:193) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler$Chain.doFilter(ServletHandler.java:1626) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.grails.web.filters.HiddenHttpMethodFilter.doFilterInternal(HiddenHttpMethodFilter.java:67) ~[grails-web-mvc-5.1.9.jar!/:5.1.9]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.eclipse.jetty.servlet.FilterHolder.doFilter(FilterHolder.java:193) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler$Chain.doFilter(ServletHandler.java:1626) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.springframework.web.filter.CharacterEncodingFilter.doFilterInternal(CharacterEncodingFilter.java:201) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.eclipse.jetty.servlet.FilterHolder.doFilter(FilterHolder.java:193) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler$Chain.doFilter(ServletHandler.java:1626) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.springframework.boot.actuate.metrics.web.servlet.WebMvcMetricsFilter.doFilterInternal(WebMvcMetricsFilter.java:96) ~[spring-boot-actuator-2.6.6.jar!/:2.6.6]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.eclipse.jetty.servlet.FilterHolder.doFilter(FilterHolder.java:193) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler$Chain.doFilter(ServletHandler.java:1626) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.springframework.web.filter.CorsFilter.doFilterInternal(CorsFilter.java:91) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.eclipse.jetty.servlet.FilterHolder.doFilter(FilterHolder.java:193) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler$Chain.doFilter(ServletHandler.java:1626) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler.doHandle(ServletHandler.java:552) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ScopedHandler.handle(ScopedHandler.java:143) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.security.SecurityHandler.handle(SecurityHandler.java:600) ~[jetty-security-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.HandlerWrapper.handle(HandlerWrapper.java:127) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ScopedHandler.nextHandle(ScopedHandler.java:235) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.session.SessionHandler.doHandle(SessionHandler.java:1624) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ScopedHandler.nextHandle(ScopedHandler.java:233) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ContextHandler.doHandle(ContextHandler.java:1440) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ScopedHandler.nextScope(ScopedHandler.java:188) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler.doScope(ServletHandler.java:505) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.session.SessionHandler.doScope(SessionHandler.java:1594) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ScopedHandler.nextScope(ScopedHandler.java:186) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ContextHandler.doScope(ContextHandler.java:1355) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ScopedHandler.handle(ScopedHandler.java:141) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.HandlerWrapper.handle(HandlerWrapper.java:127) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.Server.handle(Server.java:516) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.HttpChannel.lambda$handle$1(HttpChannel.java:487) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.HttpChannel.dispatch(HttpChannel.java:732) [jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.HttpChannel.handle(HttpChannel.java:479) [jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.HttpConnection.onFillable(HttpConnection.java:277) [jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.AbstractConnection$ReadCallback.succeeded(AbstractConnection.java:311) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.FillInterest.fillable(FillInterest.java:105) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.ssl.SslConnection$DecryptedEndPoint.onFillable(SslConnection.java:555) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.ssl.SslConnection.onFillable(SslConnection.java:410) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.ssl.SslConnection$2.succeeded(SslConnection.java:164) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.FillInterest.fillable(FillInterest.java:105) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.ChannelEndPoint$1.run(ChannelEndPoint.java:104) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.runTask(EatWhatYouKill.java:338) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.doProduce(EatWhatYouKill.java:315) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.tryProduce(EatWhatYouKill.java:173) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.run(EatWhatYouKill.java:131) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.ReservedThreadExecutor$ReservedThread.run(ReservedThreadExecutor.java:409) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.QueuedThreadPool.runJob(QueuedThreadPool.java:883) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.QueuedThreadPool$Runner.run(QueuedThreadPool.java:1034) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at java.lang.Thread.run(Thread.java:829) [?:?]
javax.naming.NamingException: LDAP connection has been closed
at com.sun.jndi.ldap.LdapRequest.getReplyBer(LdapRequest.java:133) ~[?:?]
at com.sun.jndi.ldap.Connection.readReply(Connection.java:443) ~[?:?]
at com.sun.jndi.ldap.LdapClient.ldapBind(LdapClient.java:365) ~[?:?]
at com.sun.jndi.ldap.LdapClient.authenticate(LdapClient.java:214) ~[?:?]
at com.sun.jndi.ldap.LdapCtx.connect(LdapCtx.java:2895) ~[?:?]
at com.sun.jndi.ldap.LdapCtx.<init>(LdapCtx.java:348) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getLdapCtxFromUrl(LdapCtxFactory.java:262) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getUsingURL(LdapCtxFactory.java:226) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getUsingURLs(LdapCtxFactory.java:280) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getLdapCtxInstance(LdapCtxFactory.java:185) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getInitialContext(LdapCtxFactory.java:115) ~[?:?]
at javax.naming.spi.NamingManager.getInitialContext(NamingManager.java:730) ~[?:?]
at javax.naming.InitialContext.getDefaultInitCtx(InitialContext.java:305) ~[?:?]
at javax.naming.InitialContext.init(InitialContext.java:236) ~[?:?]
at javax.naming.InitialContext.<init>(InitialContext.java:208) ~[?:?]
at javax.naming.directory.InitialDirContext.<init>(InitialDirContext.java:101) ~[?:?]
at com.dtolabs.rundeck.jetty.jaas.JettyCachingLdapLoginModule.initialize(JettyCachingLdapLoginModule.java:916) ~[classes!/:?]
at javax.security.auth.login.LoginContext.invoke(LoginContext.java:737) ~[?:?]
at javax.security.auth.login.LoginContext$4.run(LoginContext.java:672) ~[?:?]
at javax.security.auth.login.LoginContext$4.run(LoginContext.java:670) ~[?:?]
at java.security.AccessController.doPrivileged(Native Method) ~[?:?]
at javax.security.auth.login.LoginContext.invokePriv(LoginContext.java:670) ~[?:?]
at javax.security.auth.login.LoginContext.login(LoginContext.java:581) ~[?:?]
at org.springframework.security.authentication.jaas.AbstractJaasAuthenticationProvider.authenticate(AbstractJaasAuthenticationProvider.java:173) ~[spring-security-core-5.6.1.jar!/:5.6.1]
at org.rundeck.security.RundeckJaasAuthenticationProvider.super$2$authenticate(RundeckJaasAuthenticationProvider.groovy) ~[classes!/:?]
at jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method) ~[?:?]
at jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62) ~[?:?]
at jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) ~[?:?]
at java.lang.reflect.Method.invoke(Method.java:566) ~[?:?]
at org.codehaus.groovy.reflection.CachedMethod.invoke(CachedMethod.java:107) ~[groovy-3.0.9.jar!/:3.0.9]
at groovy.lang.MetaMethod.doMethodInvoke(MetaMethod.java:323) ~[groovy-3.0.9.jar!/:3.0.9]
at groovy.lang.MetaClassImpl.invokeMethod(MetaClassImpl.java:1268) ~[groovy-3.0.9.jar!/:3.0.9]
at org.codehaus.groovy.runtime.ScriptBytecodeAdapter.invokeMethodOnSuperN(ScriptBytecodeAdapter.java:144) ~[groovy-3.0.9.jar!/:3.0.9]
at org.rundeck.security.RundeckJaasAuthenticationProvider.authenticate(RundeckJaasAuthenticationProvider.groovy:39) ~[classes!/:?]
at org.springframework.security.authentication.ProviderManager.authenticate(ProviderManager.java:182) ~[spring-security-core-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter.attemptAuthentication(UsernamePasswordAuthenticationFilter.java:85) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at grails.plugin.springsecurity.web.authentication.GrailsUsernamePasswordAuthenticationFilter.attemptAuthentication(GrailsUsernamePasswordAuthenticationFilter.groovy:53) ~[spring-security-core-5.0.0-plain.jar!/:?]
at org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter.doFilter(AbstractAuthenticationProcessingFilter.java:223) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter.doFilter(AbstractAuthenticationProcessingFilter.java:213) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:336) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at grails.plugin.springsecurity.web.authentication.logout.MutableLogoutFilter.doFilter(MutableLogoutFilter.groovy:64) ~[spring-security-core-5.0.0-plain.jar!/:?]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:336) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:110) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:80) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:336) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at grails.plugin.springsecurity.web.SecurityRequestHolderFilter.doFilter(SecurityRequestHolderFilter.groovy:58) ~[spring-security-core-5.0.0-plain.jar!/:?]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:336) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:211) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:183) ~[spring-security-web-5.6.1.jar!/:5.6.1]
at org.eclipse.jetty.servlet.FilterHolder.doFilter(FilterHolder.java:193) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler$Chain.doFilter(ServletHandler.java:1626) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.grails.web.servlet.mvc.GrailsWebRequestFilter.doFilterInternal(GrailsWebRequestFilter.java:77) ~[grails-web-mvc-5.1.9.jar!/:5.1.9]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.eclipse.jetty.servlet.FilterHolder.doFilter(FilterHolder.java:193) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler$Chain.doFilter(ServletHandler.java:1626) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.grails.web.filters.HiddenHttpMethodFilter.doFilterInternal(HiddenHttpMethodFilter.java:67) ~[grails-web-mvc-5.1.9.jar!/:5.1.9]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.eclipse.jetty.servlet.FilterHolder.doFilter(FilterHolder.java:193) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler$Chain.doFilter(ServletHandler.java:1626) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.springframework.web.filter.CharacterEncodingFilter.doFilterInternal(CharacterEncodingFilter.java:201) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.eclipse.jetty.servlet.FilterHolder.doFilter(FilterHolder.java:193) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler$Chain.doFilter(ServletHandler.java:1626) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.springframework.boot.actuate.metrics.web.servlet.WebMvcMetricsFilter.doFilterInternal(WebMvcMetricsFilter.java:96) ~[spring-boot-actuator-2.6.6.jar!/:2.6.6]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.eclipse.jetty.servlet.FilterHolder.doFilter(FilterHolder.java:193) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler$Chain.doFilter(ServletHandler.java:1626) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.springframework.web.filter.CorsFilter.doFilterInternal(CorsFilter.java:91) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117) ~[spring-web-5.3.20.jar!/:5.3.20]
at org.eclipse.jetty.servlet.FilterHolder.doFilter(FilterHolder.java:193) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler$Chain.doFilter(ServletHandler.java:1626) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler.doHandle(ServletHandler.java:552) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ScopedHandler.handle(ScopedHandler.java:143) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.security.SecurityHandler.handle(SecurityHandler.java:600) ~[jetty-security-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.HandlerWrapper.handle(HandlerWrapper.java:127) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ScopedHandler.nextHandle(ScopedHandler.java:235) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.session.SessionHandler.doHandle(SessionHandler.java:1624) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ScopedHandler.nextHandle(ScopedHandler.java:233) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ContextHandler.doHandle(ContextHandler.java:1440) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ScopedHandler.nextScope(ScopedHandler.java:188) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.servlet.ServletHandler.doScope(ServletHandler.java:505) ~[jetty-servlet-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.session.SessionHandler.doScope(SessionHandler.java:1594) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ScopedHandler.nextScope(ScopedHandler.java:186) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ContextHandler.doScope(ContextHandler.java:1355) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.ScopedHandler.handle(ScopedHandler.java:141) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.handler.HandlerWrapper.handle(HandlerWrapper.java:127) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.Server.handle(Server.java:516) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.HttpChannel.lambda$handle$1(HttpChannel.java:487) ~[jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.HttpChannel.dispatch(HttpChannel.java:732) [jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.HttpChannel.handle(HttpChannel.java:479) [jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.server.HttpConnection.onFillable(HttpConnection.java:277) [jetty-server-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.AbstractConnection$ReadCallback.succeeded(AbstractConnection.java:311) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.FillInterest.fillable(FillInterest.java:105) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.ssl.SslConnection$DecryptedEndPoint.onFillable(SslConnection.java:555) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.ssl.SslConnection.onFillable(SslConnection.java:410) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.ssl.SslConnection$2.succeeded(SslConnection.java:164) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.FillInterest.fillable(FillInterest.java:105) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.io.ChannelEndPoint$1.run(ChannelEndPoint.java:104) [jetty-io-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.runTask(EatWhatYouKill.java:338) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.doProduce(EatWhatYouKill.java:315) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.tryProduce(EatWhatYouKill.java:173) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.run(EatWhatYouKill.java:131) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.ReservedThreadExecutor$ReservedThread.run(ReservedThreadExecutor.java:409) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.QueuedThreadPool.runJob(QueuedThreadPool.java:883) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at org.eclipse.jetty.util.thread.QueuedThreadPool$Runner.run(QueuedThreadPool.java:1034) [jetty-util-9.4.48.v20220622.jar!/:9.4.48.v20220622]
at java.lang.Thread.run(Thread.java:829) [?:?]
"
Thank you. For your help.
Kai E.
Jan 31, 2023, 10:52:25 AM1/31/23
to rundeck-discuss
Did you just changed the port form :389 to :636?
You need to change from providerUrl="ldap://MY-AD:389" to providerUrl="ldaps://MY-AD:636"
It could help if you would post your anonymized config for LDAPS.
You need to change from providerUrl="ldap://MY-AD:389" to providerUrl="ldaps://MY-AD:636"
It could help if you would post your anonymized config for LDAPS.
Regards,
Kai
Kai
Diego Alvarez
Jan 31, 2023, 12:36:28 PM1/31/23
to rundeck-discuss
Dear
at com.sun.jndi.ldap.LdapCtx.connect(LdapCtx.java:2895) ~[?:?]
at com.sun.jndi.ldap.LdapCtx.<init>(LdapCtx.java:348) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getLdapCtxFromUrl(LdapCtxFactory.java:262) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getUsingURL(LdapCtxFactory.java:226) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getUsingURLs(LdapCtxFactory.java:280) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getLdapCtxInstance(LdapCtxFactory.java:185) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getInitialContext(LdapCtxFactory.java:115) ~[?:?]
No luck. If I use the example and put in jaas file (I replaced in the info below, my ldap name with MY_AD)
"
com.dtolabs.rundeck.jetty.jaas.JettyCachingLdapLoginModule sufficient
debug="true"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
debug="true"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
providerUrl="ldaps://MY_AD"
......
"
The error
The error
"
ERROR jaas.JettyCachingLdapLoginModule - Naming error
javax.naming.CommunicationException: simple bind failed: "MY_AD":636
at com.sun.jndi.ldap.LdapClient.authenticate(LdapClient.java:219) ~[?:?]
javax.naming.CommunicationException: simple bind failed: "MY_AD":636
at com.sun.jndi.ldap.LdapClient.authenticate(LdapClient.java:219) ~[?:?]
at com.sun.jndi.ldap.LdapCtx.connect(LdapCtx.java:2895) ~[?:?]
at com.sun.jndi.ldap.LdapCtx.<init>(LdapCtx.java:348) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getLdapCtxFromUrl(LdapCtxFactory.java:262) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getUsingURL(LdapCtxFactory.java:226) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getUsingURLs(LdapCtxFactory.java:280) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getLdapCtxInstance(LdapCtxFactory.java:185) ~[?:?]
at com.sun.jndi.ldap.LdapCtxFactory.getInitialContext(LdapCtxFactory.java:115) ~[?:?]
.......
... 102 more
... 102 more
"
And is the same if jaas file has 636 port:
"
com.dtolabs.rundeck.jetty.jaas.JettyCachingLdapLoginModule sufficient
debug="true"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
debug="true"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
providerUrl="ldaps://MY_AD:636"
......
"
The error
The error
"
ERROR jaas.JettyCachingLdapLoginModule - Naming error
javax.naming.CommunicationException: simple bind failed: MY_AD:636
ERROR jaas.JettyCachingLdapLoginModule - Naming error
javax.naming.CommunicationException: simple bind failed: MY_AD:636
"
After if change I restarted rundeckd service.
After if change I restarted rundeckd service.
-The only doubt for jaas file. In the bind info, the user account is different. Do I need to change this for MS Win?
- bindDn="bind...@domain.com" (example)
- bindDn="CN=user,CN=Users,DC=NAME,DC=local" (I cannot put info for compliance policy)
Should i put user@mydomain? From what AD attribute i should take this reference, for the connection service account.
- bindDn="bind...@domain.com" (example)
- bindDn="CN=user,CN=Users,DC=NAME,DC=local" (I cannot put info for compliance policy)
Should i put user@mydomain? From what AD attribute i should take this reference, for the connection service account.
-Why does the config works with port 389, getting information for users to validate and with ldaps we get a "naming error"?
Thank you.
Best regards.
Kai E.
Feb 1, 2023, 2:38:26 AM2/1/23
to rundeck-discuss
As written before, a complete anonymized configuration file could help to solve the problem further.
bindDn="bind...@domain.com" works for us. Maybe you just try it out.
bindDn="bind...@domain.com" works for us. Maybe you just try it out.
And have you tested if LDAPS works correctly?
https://support.google.com/cloudidentity/answer/9190869
Regards
Kai
https://support.google.com/cloudidentity/answer/9190869
Regards
Kai
Diego Alvarez
Feb 1, 2023, 10:29:07 AM2/1/23
to rundeck...@googlegroups.com
Dear
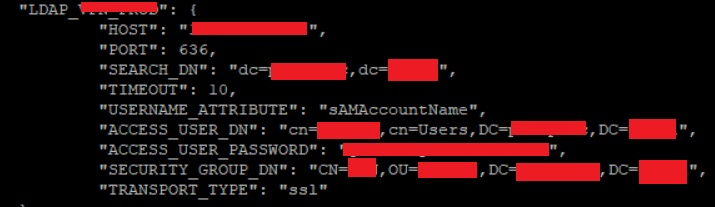
In a previous conversation y shared the jaas file config (with 389 and ldap. Later tests use 636 and ldaps). Please let me know if you need another file reference
Secure request to our ldap are working, from another servers. Like an ubuntu with the following config on json file

From the current server we are able to query the certificate using 636.
And using the curl test we also get connected
"
curl -v telnet://AD:636
curl -v telnet://AD:636
* Trying "IP":636...
* TCP_NODELAY set
* Connected to AD (IP) port 636 (#0)
"
* TCP_NODELAY set
* Connected to AD (IP) port 636 (#0)
"
In a previous conversation y shared the jaas file config (with 389 and ldap. Later tests use 636 and ldaps). Please let me know if you need another file reference
tests with 636
"multiauth {
com.dtolabs.rundeck.jetty.jaas.JettyCachingLdapLoginModule sufficient
debug="true"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
com.dtolabs.rundeck.jetty.jaas.JettyCachingLdapLoginModule sufficient
debug="true"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
providerUrl="ldaps://AD:636"
bindDn="CN=NN ,CN=Users,DC=MINE,DC=local"
........
........
"
bindDn="CN=NN ,CN=Users,DC=MINE,DC=local"
........
........
"
"
multiauth {
com.dtolabs.rundeck.jetty.jaas.JettyCachingLdapLoginModule sufficient
debug="true"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
multiauth {
com.dtolabs.rundeck.jetty.jaas.JettyCachingLdapLoginModule sufficient
debug="true"
contextFactory="com.sun.jndi.ldap.LdapCtxFactory"
providerUrl="ldaps://AD"
bindDn="CN=NN ,CN=Users,DC=MINE,DC=local"
........
........
bindDn="CN=NN ,CN=Users,DC=MINE,DC=local"
........
........
"
service log error with those test:
"ERROR jaas.JettyCachingLdapLoginModule - Naming error"
-Regarding bindDn
bindDn, supposed to be, the account that we use to connect to LDAP. And the only attribute value for the user with user@domain is, userPrincipalName. Or where to i get the value for "bind...@domain.com" ?
Thank you.
--
You received this message because you are subscribed to the Google Groups "rundeck-discuss" group.
To unsubscribe from this group and stop receiving emails from it, send an email to rundeck-discu...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/rundeck-discuss/bbc4bd34-349d-4f5e-a855-343e2077ccafn%40googlegroups.com.
Diego Alvarez
Feb 1, 2023, 10:56:01 AM2/1/23
to rundeck-discuss
Dear
No luck.
I tried with
bindDn:
-user@domain
-user
Restarting the service between changes.
No luck.
Best regards.
Diego Alvarez
Feb 3, 2023, 8:08:16 AM2/3/23
to rundeck-discuss
Dear
Could the issue be that the certificate is SHA-1?
Maybe the login module cannot use this version,or the java installed version, or rundeck version.
Thank you.
Best regards.
Jin Mao
Feb 3, 2023, 11:00:38 AM2/3/23
to rundeck...@googlegroups.com
Does the hostname in providerUrl match the name in the ssl certificate? I would use FQDN everywhere to be sure.
To view this discussion on the web visit https://groups.google.com/d/msgid/rundeck-discuss/bddb37ce-d209-4d34-a011-c5864631ba94n%40googlegroups.com.
Diego Alvarez
Feb 3, 2023, 11:37:50 AM2/3/23
to rundeck-discuss
Dear
At first we use ip in the jaas file. When we started using the certificate, we created a record on ubuntu /etc/hosts file, with AD FQDN and IP. The jaas file know uses the FQDN, and the certificate detail (CN) matches that name also.
Thank you.
Best regards.
Reply all
Reply to author
Forward
0 new messages
