[GNUPG:] PLAINTEXT 62 1655920831 error
nello
Hi team, I have an interesting one.
I am using python-gnupg version 0.4.6 on a linux machine.
I have an encrypted file coming to my application which needs to be decrypted (I correctly own the private key and I am using the same key to correctly decrypt different files using the same setup).
Here's some informations about the file using linux 'file' command and 'pgpdump':
file test_file.csv.pgp
test_file.csv.pgp: data
pgpdump test_file.csv.pgp
New: Compressed Data Packet(tag 8)(4096 bytes) partial start
Comp alg - ZIP <RFC1951>(comp 1)
New: (3244 bytes) partial end
New: unknown(tag 41)(110 bytes)
New: Compressed Data Packet(tag 8)
Comp alg - unknown(comp 78)
pgpdump: unknown compress algorithm.
gpg --list-packet test_file.csv.pgp
# off=0 ctb=c8 tag=8 hlen=2 plen=0 partial new-ctb
:compressed packet: algo=1
# off=3 ctb=cb tag=11 hlen=2 plen=0 partial new-ctb
:literal data packet:
mode b (62), created 1655920831, name="",
raw data: unknown length
My application calls the decrypt_file() method from the python-gnupg library. I have either tested using the output parameter or directly using the result object. This error is currently returned in both cases:
[GNUPG:] PLAINTEXT 62 1655920831
this is the full log when I enable the verbosity on the GPG object:
gpg --status-fd 2 --no-tty --no-verbose --fixed-list-mode --batch --with-colons --homedir /Users/test/Desktop/test/.gnupg --no-default-keyring --keyring /Users/test/Desktop/test/.gnupg/pubring.gpg --secret-keyring /Users/test/Desktop/test/.gnupg/secring.gpg --passphrase-fd 0 --decrypt --yes --output /Users/test/Desktop/test/test9yetqku/testnp2n7cfq
[GNUPG:] PLAINTEXT 62 1655920831
The result.ok flag is set to False when the decryption process is completed
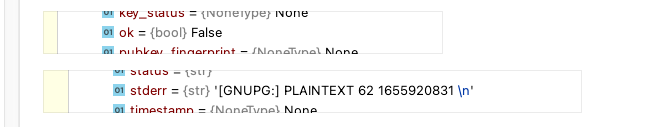
HOWEVER if I look to this location where I wanted to have my decrypted file '/Users/test/Desktop/test/test9yetqku/testnp2n7cfq' I can see the actual content decrypted!
I am not really sure what Is happening in the background but I believe that the Crypter instance variable self.ok status is not set yo True for some reason within the python-gnupg library.
I have been testing the same thing using the gpg binary v 2.0.22 ( I am using the same gpg version with the python-gnupg library) and I was correctly able to decrypt the file without no errors.
If you would have any idea would be much appreciated. Currently it looks to me to be a bug in the library but I'd like to hear you guys opinion : )
Thanks!
Vinay Sajip
nello
Hi Vinay, thanks for taking some time to answer!
