Is using WiFiClientSecure alone with a MQTTS server enable encyption
946 views
Skip to first unread message
Balasundram Arunn
Apr 20, 2017, 6:05:20 AM4/20/17
to MQTT
Hi All,
I want to implement encryption for MQTT in ESP8266. The SSL authorization is not required for my project. I am using pubsubclient esp8266 mqtt library and WiFiClientSecure to connect my MQTTs server. However client.verify function always return false.
My question is since I need only encryption, Can I get rid of verify() function? Is using WiFiClientSecure alone provide encryption to the packets?
Paul Fremantle
Apr 20, 2017, 7:02:52 AM4/20/17
to mq...@googlegroups.com
Hi
Firstly, my understanding is that verify is required.
Secondly, if you encrypt the message, but you encrypt it to the wrong server (i.e. an attacker) then encryption is pointless, so even if you can make it work without verify, you shouldn't!
What is the problem with verify. It works ok for me.
You can use openssl to identify the right serial number to verify:
e.g.
> openssl s_client -connect test.mosquitto.org:8883 2>&1|openssl x509 -noout -serial
serial=803F2238FAFB5CE9
Paul
--
To learn more about MQTT please visit http://mqtt.org
---
You received this message because you are subscribed to the Google Groups "MQTT" group.
To unsubscribe from this group and stop receiving emails from it, send an email to mqtt+unsubscribe@googlegroups.com.
To post to this group, send email to mq...@googlegroups.com.
Visit this group at https://groups.google.com/group/mqtt.
For more options, visit https://groups.google.com/d/optout.
Paul Fremantle
Doctoral Researcher, University of Portsmouth, School of Computing
Visiting Scientist, Institute of the Architecture of Application Systems, Stuttgart
Visiting Lecturer, Software Engineering Programme, Oxford University
Co-Founder, WSO2
Apache Member and Committer
Apache Member and Committer
twitter: pzfreo / skype: paulfremantle / blog: http://pzf.fremantle.org
urs.epp...@switch.ch
Apr 22, 2017, 3:40:45 AM4/22/17
to MQTT
I'd like to learn more about what you are doing, then I might be able to help with more concrete advice.
I built the following setup: ESP-device <-> MQTT <-> node-red
Instead of using SSL to secure the data transmission between the ESP and MQTT, I used AES encryption to secure the data transmitted between the ESP and node-red. It is also secured against a replay attack. It was a pain, but it works now.
But I plan to use SSL in the future between ESP and MQTT and get rid of the AES encryption.
Message has been deleted
Paul Fremantle
Apr 24, 2017, 5:11:22 AM4/24/17
to mq...@googlegroups.com
You should put the server hostname in the verify.
Paul
On 24 Apr 2017 8:32 am, "Balasundram Arunn" <vba...@gmail.com> wrote:
We have an MQTTs server and from ESP8266 we need to connect and PUBLISH a message. The packets need to be encrypted in this communication. I have tried to verify the fingerprint of the server using verify method by it always results "TLS cannot be verified".WiFiClientSecure secureClient;PubSubClient client(MQTT_SERVER, PORT, callback, secureClient);if (client.connect((char*) clientName.c_str(),"rabbit","rabbit")){boolean verified = secureClient.verify(fingerprint,"server IP");Serial.print(verified ? "verified tls!" : "unverified tls");}
Balasundram Arunn
Apr 24, 2017, 6:24:14 AM4/24/17
to MQTT, paul.fr...@port.ac.uk
Thanks a lot for the assistance. I will check by using a host name. Won't this work with server IP?
On Monday, April 24, 2017 at 2:41:22 PM UTC+5:30, Paul Fremantle wrote:
You should put the server hostname in the verify.Paul
On 24 Apr 2017 8:32 am, "Balasundram Arunn" <vba...@gmail.com> wrote:
We have an MQTTs server and from ESP8266 we need to connect and PUBLISH a message. The packets need to be encrypted in this communication. I have tried to verify the fingerprint of the server using verify method by it always results "TLS cannot be verified".WiFiClientSecure secureClient;PubSubClient client(MQTT_SERVER, PORT, callback, secureClient);if (client.connect((char*) clientName.c_str(),"rabbit","rabbit")){boolean verified = secureClient.verify(fingerprint,"server IP");Serial.print(verified ? "verified tls!" : "unverified tls");}
--
To learn more about MQTT please visit http://mqtt.org
---
You received this message because you are subscribed to the Google Groups "MQTT" group.
To unsubscribe from this group and stop receiving emails from it, send an email to mqtt+uns...@googlegroups.com.
Balasundram Arunn
Apr 24, 2017, 6:42:02 AM4/24/17
to MQTT, paul.fr...@port.ac.uk
I Have tried to verify the Adafruit IO server using verify() method . It connects to the MQTT broker successfully but returns unverified TLS.
WiFiClientSecure secureClient;
PubSubClient client(io.adafruit.com, 8883, callback, secureClient);
const char* fingerprint = "95 BC F9 80 31 B7 44 E4 CF 7E 4A F1 A8 95 4A A9 F2 58 73 7A";
if (client.connect((char*) clientName.c_str(),"username","ac26fbc2449640fbb4013c31caaxxxxx"))
{
Serial.print("MTQQ Connected\n");
boolean verified = secureClient.verify(fingerprint,"io.adafruit.com"); //mqtt_server.toString().c_str()
Serial.print(verified ? "verified tls!" : "unverified tls");
}
On Monday, April 24, 2017 at 2:41:22 PM UTC+5:30, Paul Fremantle wrote:
You should put the server hostname in the verify.Paul
On 24 Apr 2017 8:32 am, "Balasundram Arunn" <vba...@gmail.com> wrote:
We have an MQTTs server and from ESP8266 we need to connect and PUBLISH a message. The packets need to be encrypted in this communication. I have tried to verify the fingerprint of the server using verify method by it always results "TLS cannot be verified".WiFiClientSecure secureClient;PubSubClient client(MQTT_SERVER, PORT, callback, secureClient);if (client.connect((char*) clientName.c_str(),"rabbit","rabbit")){boolean verified = secureClient.verify(fingerprint,"server IP");Serial.print(verified ? "verified tls!" : "unverified tls");}
--
To learn more about MQTT please visit http://mqtt.org
---
You received this message because you are subscribed to the Google Groups "MQTT" group.
To unsubscribe from this group and stop receiving emails from it, send an email to mqtt+uns...@googlegroups.com.
Paul Fremantle
Apr 24, 2017, 7:11:16 AM4/24/17
to Balasundram Arunn, MQTT
That doesn't look like the right serial for io.adafruit.com:
I think the serial is:
37D78A0B08602951C3CCC2EF489101C6
Where did you get that one from?
Paul
Balasundram Arunn
Apr 25, 2017, 12:39:36 AM4/25/17
to MQTT, vba...@gmail.com
I got the fingerprint from the following code
In the verify function we have to use SHA1 fingerprint right? (did you mention SHA1 fingerprint as serial
??)
However, I have tested with the serial you have provided and still its return false.
const char* fingerprintAIO= "37 D7 8A 0B 08 60 29 51 C3 CC C2 EF 48 91 01 C6";
if (client.connect((char*) clientName.c_str(),"vbaxxx","ac26fbc2449640fbb4013c31caaxxxx"))
{
Serial.print("MTQQ Connected\n");
boolean verified = secureClient.verify(fingerprintAIO,"io.adafruit.com");
Paul Fremantle
Apr 25, 2017, 3:53:49 AM4/25/17
to mq...@googlegroups.com
Bala
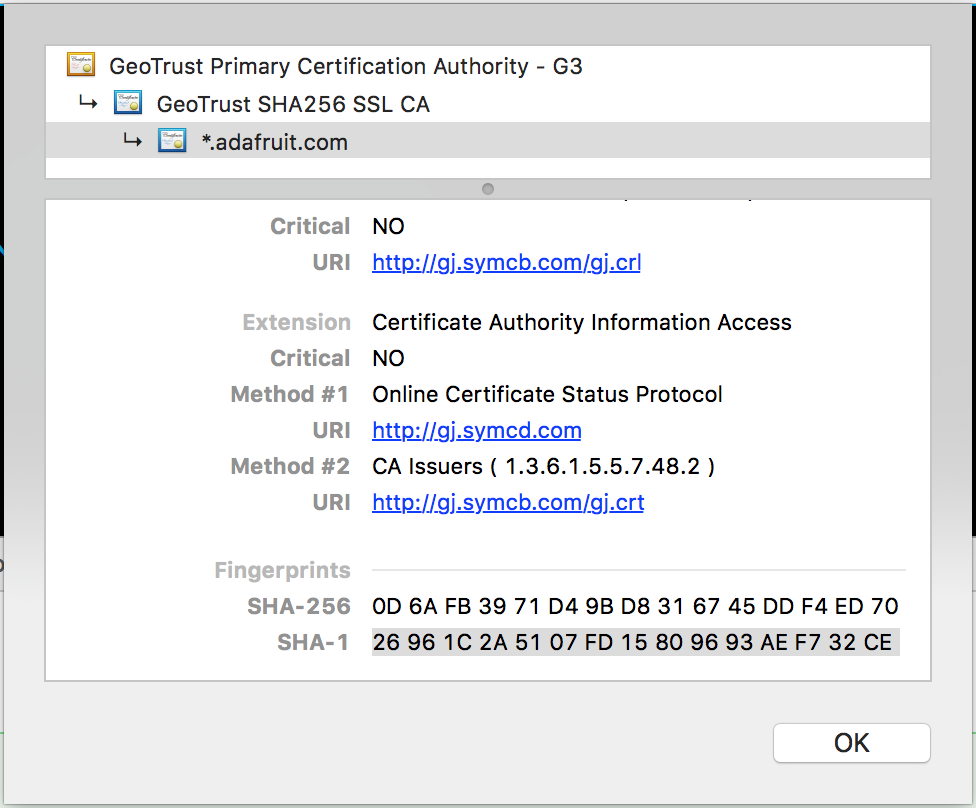
I'm sorry. I was away from my ESP8266 and so I gave you some wrong information!
The latest SHA1 for io.adafruit.com is 26 96 1C 2A 51 07 FD 15 80 96 93 AE F7 32 CE
I can't test this as I don't have an ESP8266 with me right now.

You can't trust a fingerprint in a code example because everytime the cert is updated this changes.
Paul
--
To learn more about MQTT please visit http://mqtt.org
---
You received this message because you are subscribed to the Google Groups "MQTT" group.
To unsubscribe from this group and stop receiving emails from it, send an email to mqtt+unsubscribe@googlegroups.com.
To post to this group, send email to mq...@googlegroups.com.
Visit this group at https://groups.google.com/group/mqtt.
For more options, visit https://groups.google.com/d/optout.
Reply all
Reply to author
Forward
0 new messages
