PSA: DTLS client hello extension permutation will be enabled soon, do interop testing now
491 views
Skip to first unread message
Philipp Hancke
Oct 2, 2023, 10:12:07 AM10/2/23
to discuss...@googlegroups.com, Harald Alvestrand
As announced in
we plan to enable a BoringSSL feature that randomizes the order of TLS extensions in the DTLS client hello soon. This should not have any impact to applications but as usual, some interop testing is required.
Please test your services, in particular if you are not using OpenSSL or BoringSSL and in your scenario(s) the browser is sending the DTLS client hello.
To test, launch Chrome (119.0.6038.0 or later, currency Canary) by starting Chrome with
--force-fieldtrials=WebRTC-PermuteTlsClientHello/Enabled/
and ensure the DTLS connection is still established.
In Wireshark this can be observed in the DTLS client hello, in particular the "use_srtp" extension which is normally last as shown below

will be in a different place like this:
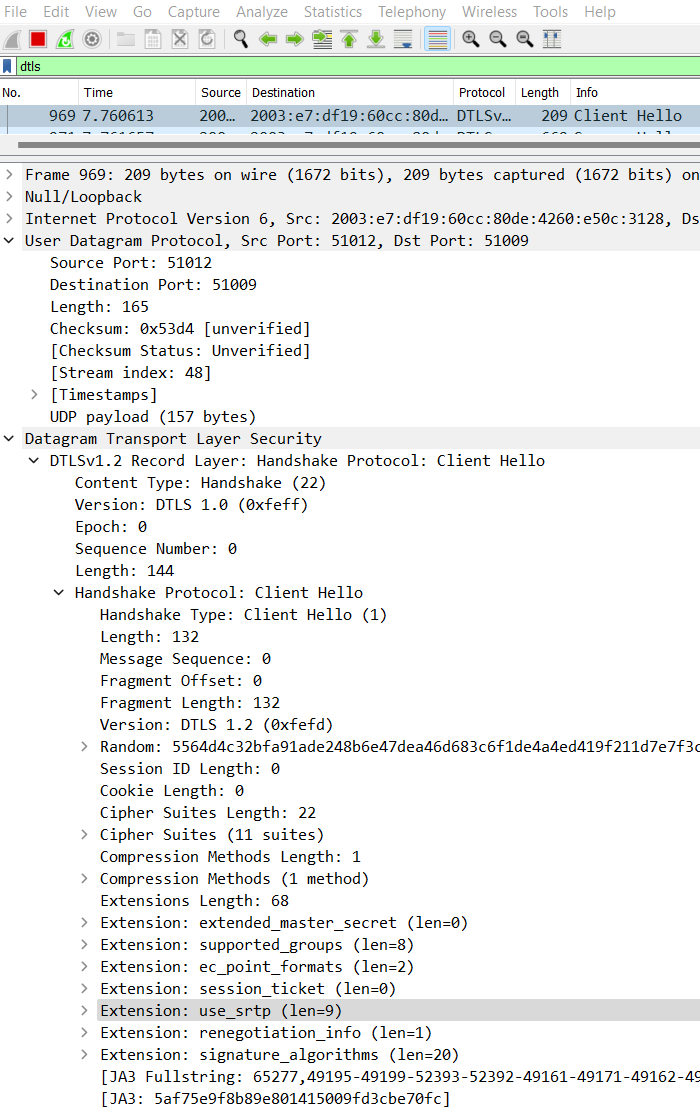
You can enable the feature for testing in M119. We expect to turn it on in stable for some percentage of users in M120 (which ships in December) and enable it for all users some time in M121.
Leave feedback either here or in https://bugs.chromium.org/p/webrtc/issues/detail?id=15467
cheers
Philipp
Iñaki Baz Castillo
Oct 6, 2023, 8:59:01 AM10/6/23
to discuss-webrtc
I confirm that it works fine with mediasoup server. I've tested Canary 119.0.6045.0 in macOS Intel.
Lorenzo Miniero
Oct 17, 2023, 9:33:14 AM10/17/23
to discuss-webrtc
I just tested this with Janus, using Chrome 120.0.6062.2 on Linux, and I can confirm it works fine there too.
Lorenzo
Boris Grozev
Dec 4, 2023, 10:05:42 AM12/4/23
to discuss-webrtc
Works fine with Jitsi/bouncycastle, tested using Chrome 121.0.6151.0 on mac.
Boris
Boris
Reply all
Reply to author
Forward
0 new messages
