Doubts with trace_reader vine
42 views
Skip to first unread message
gogineni kailashnath
Apr 19, 2021, 12:09:09 PM4/19/21
to BitBlaze User Discussion group
Hello,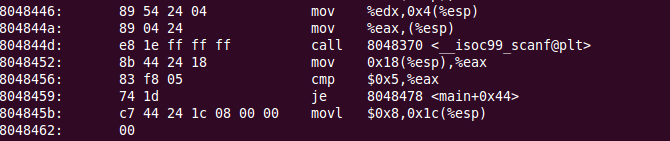
.png?part=0.1&view=1)
We are trying to use openSSL with TEMU for performing tainting (whole packet and file level tainting also works - reference paper - https://www2.seas.gwu.edu/~tlan/papers/CP_SC_2019.pdf). When we finish the tainting we get the results such as 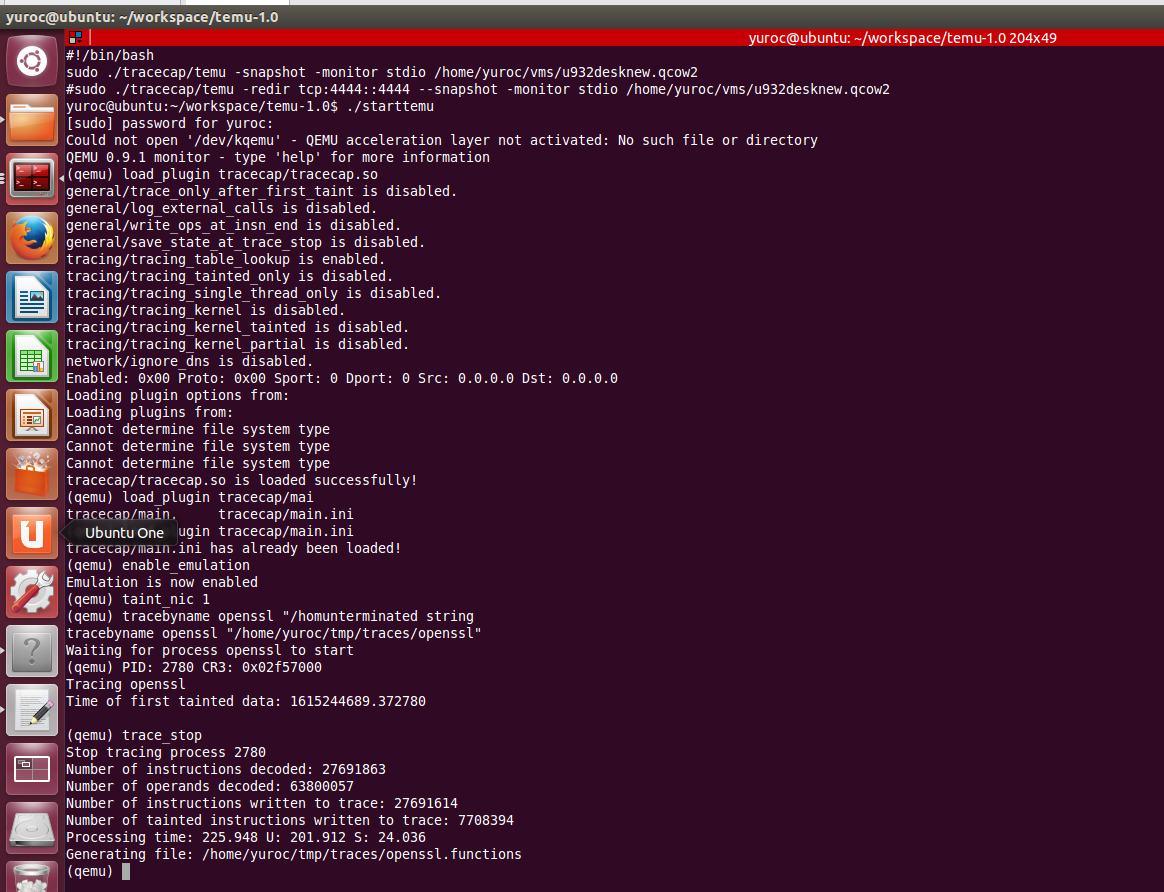

Then we used, vine to get the binary to get the human readable format. But our aim is to take a basic block from the file generated by trace_reader and map it to the address of the dump of openssl binary. But the problem we faced is, the instruction address of trace_reader generated binary and normal openssl dump binary are not matching. So, can anyone help to solve this problem? (the trace_reader generated binary has some instructions starting with b7xxxxx, but in our openssl binary all the instruction addresses start from 8xxxx)
Openssl binary example:

tainted binary:
.png?part=0.1&view=1)
Heng Yin
Apr 19, 2021, 3:23:51 PM4/19/21
to bitblaz...@googlegroups.com
this is just a simple question about rebasing. During execution, your openssl is loaded into a region starting at b7. In disassemblers like IDA or Ghidra, you can rebase the openssl binary to be consistent with the base address during execution.
--
---
You received this message because you are subscribed to the Google Groups "BitBlaze User Discussion group" group.
To unsubscribe from this group and stop receiving emails from it, send an email to bitblaze-user...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/bitblaze-users/aa7d1fc7-9eda-4eda-a43e-578490252974n%40googlegroups.com.
Reply all
Reply to author
Forward
0 new messages
