Anyone else seeing Binaries built w/ asan support hang on Apple Silicon?
412 views
Skip to first unread message
XSS.Cx
Feb 9, 2021, 1:05:52 AM2/9/21
to address-sanitizer
Hello & Good Day-
Anyone else seeing Binaries built w/ asan support hang on Apple Silicon?
Prior to asking this question, I've done a search for kNumPossibleRegions and have found little to read since 2013 in this Group or elsewhere.
New M1 Mac... Is anyone else seeing Binaries built w/ asan support hang on arm64?
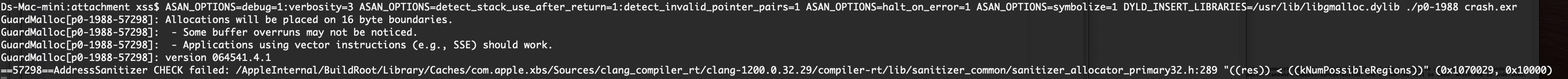
Reproduction Case is for p0-1988. crash.exr and binary compiled with ASAN at URL https://github.com/xsscx/mac-binaries/tree/main/project0-reproduction-cases/p0-1988
ASAN_OPTIONS=debug=1:verbosity=3 ASAN_OPTIONS=detect_stack_use_after_return=1:detect_invalid_pointer_pairs=1 ASAN_OPTIONS=halt_on_error=1 ASAN_OPTIONS=symbolize=1 DYLD_INSERT_LIBRARIES=/usr/lib/libgmalloc.dylib MallocPreScribble=1 ASAN_OPTIONS=SCribble=1 ASAN_OPTIONS+MallocGuardEdge=1 ./p0-1988 crash.exr
..
GuardMalloc[p0-1988-57463]: version 064541.4.1
==57463==AddressSanitizer CHECK failed: /AppleInternal/BuildRoot/Library/Caches/com.apple.xbs/Sources/clang_compiler_rt/clang-1200.0.32.29/compiler-rt/lib/sanitizer_common/sanitizer_allocator_primary32.h:289 "((res)) < ((kNumPossibleRegions))" (0x1070029, 0x10000)
...
uname -a = Darwin Ds-Mac-mini.local 20.3.0 Darwin Kernel Version 20.3.0: Thu Jan 21 00:06:51 PST 2021; root:xnu-7195.81.3~1/RELEASE_ARM64_T8101 arm64
..
Program termination is normal when just run from the command line or within LLDB, its just when injecting DYLD_INSERT_LIBRARIES=/usr/lib/libgmalloc.dylib that ASAN hangs.
If this is known, sorry for the Noise, can someone Post a Link for a Fix.
Otherwise, is this enough for reproduction to identify the problem?
.png?part=0.2&view=1)
Dan Liew
Feb 9, 2021, 7:19:54 PM2/9/21
to address-...@googlegroups.com
Hi,
You shouldn't be trying to use libgmalloc with ASan. They are not compatible with each other. Libgmalloc is a replacement memory allocator that tries to detect buffer overruns using guard pages. ASan also tries to replaces the memory allocator so that it can perform its bug detection. **You cannot use both together**.
Given that ASan detects a superset of issues that gmalloc can find, I would advise you just use ASan without gmalloc.
If you run into issues with ASan (without gmalloc) on macOS please submit feedback to Apple using Feedback Assistant (https://developer.apple.com/bug-reporting/).
Hope that helps,
Dan.
--
You received this message because you are subscribed to the Google Groups "address-sanitizer" group.
To unsubscribe from this group and stop receiving emails from it, send an email to address-saniti...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/address-sanitizer/57818c88-ae70-4241-95db-b65baf5a8acbn%40googlegroups.com.
XSS.Cx
Feb 10, 2021, 9:50:56 AM2/10/21
to address-sanitizer
Hello & Good Day!
Thank you for the response.
==========
tl;dr
==========
QUERY: Is anyone seeing ASAN Hang on Apple Silicon when doing a repro of P0-1988?
RESPONSE: You shouldn't be trying to use libgmalloc with ASan. They are not compatible with each other. Libgmalloc is a replacement memory allocator that tries to detect buffer overruns using guard pages. ASan also tries to replaces the memory allocator so that it can perform its bug detection. **You cannot use both together**.
TAKEAWAY: 100% correct. RTFM https://developer.apple.com/documentation/xcode/diagnosing_memory_thread_and_crash_issues_early
RESOLVED: NO
======================
Discussion & Analysis
======================
A researcher is reproducing various Google P0 Bugs that have been accepted and resolved by Apple Product Security. For example, Google P0-1988, using Intel and Apple Silicon.
The documentation for ASAN usage details that: "The Address Sanitizer tool replaces the malloc(_:) and free(_:) functions with custom implementations. The custom malloc(_:) function surrounds a requested memory block with special off-limits regions, and reports attempts to access those regions. The free(_:) function places a deallocated block into a special quarantine queue, and reports attempts to access that quarantined memory.""
For n00bz - RTFM for ASAN usage at URL https://developer.apple.com/documentation/xcode/diagnosing_memory_thread_and_crash_issues_early
My query was specific to the Reproduction of P0-1988 when run on Apple Silicon and elicited a form of response telling the n00b that he's doing it all wrong, to RTFM, and file at Feedback if any real issues. The Response is expected.
I'll emphasize that I'm ..."not using ASAN with libgmalloc"... but instead reproducing 'Google's use of libgmalloc with ASAN as demonstrated in P0 Bug 1988' on Apple Silicon {and Intel}. Lets look closely at the information provided by Google P0 for Issue 1988 for compilation and execution:
<snip>
The attached OpenEXR [1] image causes a crash in ImageIO on the latest macOS. To reproduce the issue, the attached code (tester.m) can be used. With tester.m compiled with ASAN and using libgmalloc, the image should cause a crash due to an access violation:
% clang -o tester tester.m -framework Foundation -framework CoreGraphics -framework AppKit -fsanitize=address
% DYLD_INSERT_LIBRARIES=/usr/lib/libgmalloc.dylib ./tester crash.exr
</snip>
====
JFTR
====
The build instructions for P0-1988 PoC and are to compile with: -fsanitize=address.
The cli args are: DYLD_INSERT_LIBRARIES=/usr/lib/libgmalloc.dylib ./tester crash.exr
P0's use of -fsanitize=address and DYLD_INSERT_LIBRARIES=/usr/lib/libgmalloc.dylib is _not_ isolated to just P0-1988.
The reproduction case follows the exact instructions of P0-1988 on Apple Silicon {and Intel} and the Result is a Hang on the latest version of MACOS on Apple Silicon {when not using the ASAN memory allocator} while using libgmalloc as indicated in the P0-1988 PoC.
Based on the Response, I will assume that the Report of 'ASAN Hang on Apple Silicon' is Informative, and Closed.
Cheers!
Reply all
Reply to author
Forward
0 new messages
