TunnelBlick and High Sierra self signed SSL issues
Brian
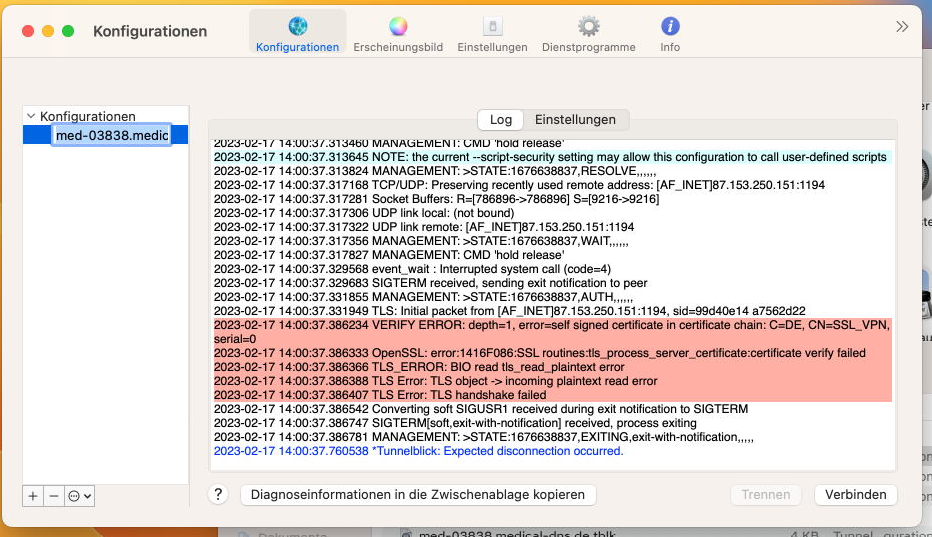
2017-09-29 22:46:32 VERIFY ERROR: depth=0, error=format error in certificate's notBefore field: C=US, ST=NA, L=NA, O=Home, OU=OU, CN=SophosApplianceCertificate_xxxxx, emailAddress=xxxxx
2017-09-29 22:46:32 OpenSSL: error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed
2017-09-29 22:46:32 TLS_ERROR: BIO read tls_read_plaintext error
2017-09-29 22:46:32 TLS Error: TLS object -> incoming plaintext read error
2017-09-29 22:46:32 TLS Error: TLS handshake failed
Molina-Bulla Harold
- "¿Existe el Gran Hermano?" - Winston
- "Claro que existe. El Partido existe. El Gran Hermano es la
encarnación del partido." - O'Brien
- "¿Existe en el mismo sentido en que yo existo?" - Winston
- "Tú no existes." - O'Brien
George Orwell (1984)
-----------------------------------------------------------------
Recuerda: PRISM te está vigilando!!! X)
Y tu no existes!!!
-----------------------------------------------------------------
Harold Molina-Bulla Ph.D.
h.mo...@gmail.org
--
You received this message because you are subscribed to the Google Groups "tunnelblick-discuss" group.
To unsubscribe from this group and stop receiving emails from it, send an email to tunnelblick-dis...@googlegroups.com.
Visit this group at https://groups.google.com/group/tunnelblick-discuss.
For more options, visit https://groups.google.com/d/optout.
Tunnelblick developer
laden...@gmail.com
2017-10-02 19:06:53 VERIFY OK: depth=1, /C=de/L=Dortmund/O=Versatel/CN=Versatel_VPN_CA/emailAddress=ad...@vt-security.de
2017-10-02 19:06:53 VERIFY ERROR: depth=0, error=format error in certificate's notAfter field: /C=de/L=Dortmund/O=Versatel/CN=ASG_1/emailAddress=ad...@vt-security.de
2017-10-02 19:06:53 OpenSSL: error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed
2017-10-02 19:06:53 TLS_ERROR: BIO read tls_read_plaintext error
2017-10-02 19:06:53 TLS Error: TLS object -> incoming plaintext read error
2017-10-02 19:06:53 TLS Error: TLS handshake failed
2017-10-02 19:06:53 Fatal TLS error (check_tls_errors_co), restarting
Tunnelblick developer
I have the same issues ever since upgrading to High Sierra.I now get certificate errors like this:
2017-10-02 19:06:53 VERIFY OK: depth=1, /C=de/L=Dortmund/O=Versatel/CN=Versatel_VPN_CA/emailAddress=admin@vt-security.de
2017-10-02 19:06:53 VERIFY ERROR: depth=0, error=format error in certificate's notAfter field: /C=de/L=Dortmund/O=Versatel/CN=ASG_1/emailAddress=admin@vt-security.de
2017-10-02 19:06:53 OpenSSL: error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed
2017-10-02 19:06:53 TLS_ERROR: BIO read tls_read_plaintext error
2017-10-02 19:06:53 TLS Error: TLS object -> incoming plaintext read error
2017-10-02 19:06:53 TLS Error: TLS handshake failed
2017-10-02 19:06:53 Fatal TLS error (check_tls_errors_co), restarting
HoneyBadger
On Saturday, September 30, 2017 at 7:04:36 AM UTC-4, Brian Hawkins wrote:
abe...@gmail.com
alexi...@gmail.com
Now enforcing:
no fractions
no offsets
seconds must be present
Z is required
digits must be 0-9 (but we don't check that the date/time is valid)
For the test certificate we now get
error 13 at 0 depth lookup: format error in certificate's notBefore field
error 22.pem: verification failed
Tunnelblick developer
doom
Tunnelblick developer
Fabian Stolz