Fwd: Urgent message from Ministry of Education on Cyber Security
Pete Mundy
From: Katrina Casey, Acting Secretary for Education <bull...@education.govt.nz>Subject: Urgent message from Ministry of Education on Cyber Security
Message from Ministry of Education on Cyber Security
Background
We have been made aware of a number of cyber-attacks that have led to school servers being compromised. Where we become aware that a school’s server is potentially affected, we will contact you immediately. Cybercriminals will attack your servers for a number of reasons however our initial assessment is that it is more likely they are motivated to use them as staging posts for other attacks (eg sending spam) or for pure financial gain (eg ransomware), rather than to illegally obtain school data per se.
Recommended action
We recommend that you:Firstly check ALL school servers for any signs of compromise, specifically remote access logs, processes consuming high amounts of processor time (potential Bitcoin mining) and unusual outbound communication including software / applications contacting overseas IP addresses. Your IT provider or school IT staff will be best placed to assist with this.
We also recommend the following to improve your resilience to cyber-attacks.
What to do if a compromise is identified
- Enforce a complex password policy and ensure that default passwords for system accounts are changed.
- Implement two-factor authentication for remote access, such as Remote Desktop Protocol (RDP) and Virtual Private Network (VPN). For more details on VPN go to NetSafe
- Apply regular updates to applications and operating systems to ensure up to date protection against known vulnerabilities.
- Restrict accounts with administrative privileges to make it more difficult for an attacker to install malware and gain access to the wider network.
- Ensure backups are run regularly with separate backups of both data and server images. Check backups on a regular basis to ensure the backups are successful and can be used to restore data.
- Ensure a secure configuration of servers by blocking or disabling all externally facing services and ports by default, and only enabling those actually required. This can include whitelisting or blocking external access to administration panels and not using default login credentials.
- Ensure antivirus software is installed and updated regularly and in all cases no later than 7 days from release of an update from the anti-virus provider.
- Enable comprehensive logging and ensure that at least three months logs are retained and backed up. Logging is critical in a forensic context to establish the cause, extent and duration of any future incident.
If you identify any signs of compromise, we recommend the following:
- Immediately isolate the compromised server(s) from the internet.
- Force a password change for all user accounts, including network accounts.
- Rebuild the server. Rebuilding the server is crucial to ensure removal of all malware and methods of access created by the attackers. If your school seeks to enlist the services of a security provider to conduct a forensic investigation of the incident, they will require access to the server to conduct analysis prior to the server being rebuilt.
If ransomware is identified
If you identify ransomware has been installed:
- Advise the New Zealand Police.
- Advise Netsafe, using ‘The Orb’
- It is strongly recommend that you DO NOT pay the ransom under any circumstances.
- Undertake the steps outlined above.
Forensic analysis
The priority is remediation of any compromised servers. For schools that require information on the method in which they were compromised, please contact us via our details below.Schools IT Helpdesk 0800 CALLICT (0800 225 542) or 09 356 3167, email:cal...@tki.org.nz
NetSafe has additional information on steps to protect your school from cybercriminals.
Information Sharing
If you identify any server that has been compromised, we request that you advise the Ministry’s Security and Privacy team via email security...@education.govt.nz. The information that you provide to us will be used to help with advice and guidance for any other affected schools. This information will be shared with appropriate organisations for coordination of response.
Contact us at: bull...@education.govt.nz | education.govt.nz | Follow us on Twitter
You can update your preferences or unsubscribe from this list
You are receiving this email because you are a key school leader and subscribe to the Ministry Bulletin for School Leaders | He Pitopito Kōrero.
WHS Ict Technician
gre...@staff.cbhs.school.nz
What springs to mind:
a) Test that you can restore to a new VM; cursory glance at the file system; spot check of application-specific data/configuration.
This would confirm that the backup media was good, the backup was complete and restore-able, and the captured state/point in time was as-expected.
But it wouldn't prove that the machine actually worked.
OR
b) Restore and boot the VM with no network connection; log in locally and perform spot checks as per (a).
This would confirm 95% of operation, but still doesn't prove that the machine works as intended.
OR
c) During a designated testing period, bring down the live server and boot a restored copy, check, then revert.
This would prove application-level operation, but might cause undesired side-effects in relation to other systems (particularly related databases/storage/cloud replication) so could only be used for certain servers.
OR
d) Maintain a segregated testing network capable of running enough of the server infrastructure to live-test any given restored machine at any time.
- Ben.
flow in
Blake Richardson
There is an article about this in the press this morning, it seems to hint that it is only schools connected to the N4L network.
Pete Mundy
[citation needed]
http://www.stuff.co.nz/the-press/news/82112042/dozens-of-new-zealand-schools-hacked-access-put-up-for-online-sale
Yeah, but I'd hardly call it a well researched or well written article. It also refers to N4L as an 'education IT company'! I thought they were a network provider...
And it reports that 'School principals said their networks often contained sensitive information such as contact details, attendance records, and pupils' grades.'. Gee, you don't say. And the sky is blue too, but they left that out?!
Matthew Strickland
Patrick Dunford
There is an article about this in the press this morning, it seems to hint that it is only schools connected to the N4L network.
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-sch...@googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
flow in
Julian Davison
i wonder if it is related to the teamviewer exploits my security appliance was stopping? lots of BYOD devices were calling russia
--
flow in
The reason i'm suspecting malware is because all the schools are with n4l - so a failure in n4l filtering would affect them all. We are with n4l but have our own security appliance. In the couple of years that we've had it, its gone from doing very little to stopping hundreds of events a day. The current trend seems to be malware injection via ads on websites. It may be being paranoid, but i feel that my job has shifted in nature significantly in the last few years, towards security and pro-active disaster mitigation, with the networking and sysadmin roles being less prominent (as we move to cloud services)
Blake Richardson
What appliance do you use if you don't mind me asking?
flow in
We use the MX100 from meraki. It is a bit of a pita - i have a restrictive policy per vlan and manually apply less restrictive ones, as it appears their AD integrated policy assignment is not 100%. But it is otherwise very useful.
Patrick Dunford
They suggested a major issue for BYOD is that it was all running in one network with full access to everything else on that network. BYOD devices getting hacked sounds different from BYOD devices hacking into a school server, if the BYOD is a separate network from the servers then it has less to do with hacking the school's servers and more to do with bandwidth use or other nuisances.
J B
Had some cryptoware sneek in which owned the office drive and half of the student drive before it was picked up, wasted right by the AV at the time.
As we had shadow copy and limited user accounts by with separate non-login admin accounts for those that needed them rollback was simple but if the user had been running as admin it could have killed the shadow copies and forced us to use backups instead.
I also saw the possible N4L link in the media article and wondered if it was a case of schools trusting them a bit too much and not taking their own steps on top of N4L despite n4ls contention that we should all just trust their edge device to keep traffic safe.
Sent from my Windows 10 phone
> On 15/07/2016, at 8:00 am, Blake Richardson <bla...@stmargarets.school.nz> wrote:
>
>> There is an article about this in the press this morning, it seems to hint that it is only schools connected to the N4L network.
flow in
even with BYOD devices, it is hard to stop VLAN hopping. How many of us have simple double tagging protection in place? (https://www.nlogic.co/understanding-vlan-hopping-attacks/). We simple don't have the guidance from above on how to do it - each of us has to go and skill up. Who here knows how ruckus, aerohive, aruba, ubiquiti deal with that one problem? Who has dug into their switch capabilities to leverage them to help? As soon as compromised device joins the network, you could have any sort of attack occurring. There's just too much going on, with new threats every day, for any of us to keep up on our own. We need coordination and oversight.
I feel that the Ministry needs to provide PD and best practice guidance for network and system admins in school, plus monitor contracted services to make sure they are following it.
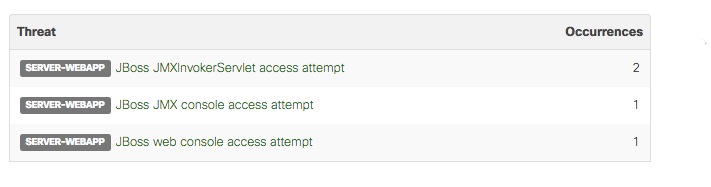
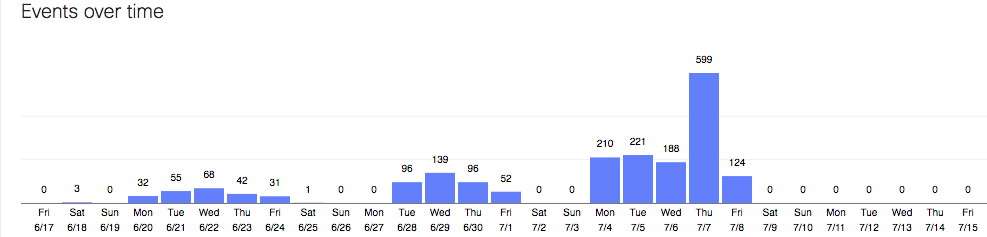
outgoing traffic events, initiated by malware, prevented in the last few weeks, in our small school:
--

Flow In, MA hons Cantab, MSc | ICT Technician | WESTLAND HIGH SCHOOL
Phone: 03 755 6054 | Cell: 022 027 5107 | Fax: 03 755 6269 | i...@westlandhigh.school.nz
PO Box 154, 140 Hampden Street, Hokitika 7842
http://www.westlandhigh.school.nz/
WHAKATERE I Ā TĀTOU HAERENGA - NAVIGATING OUR JOURNEYS
This message contains confidential information and is intended only for the individual named. If you are not the named addressee you should not disseminate, distribute or copy this e-mail. Please notify the sender immediately by e-mail if you have received this e-mail by mistake and delete this e-mail from your system.
--
You received this message because you are subscribed to a topic in the Google Groups "Techies for schools" group.
To unsubscribe from this topic, visit https://groups.google.com/d/topic/techies-for-schools/5H0dCCyOmFI/unsubscribe.
To unsubscribe from this group and all its topics, send an email to techies-for-sch...@googlegroups.com.
Patrick Dunford
It looks to me as though having a VLAN for internal wired access is a possibility that may prove to be necessary, at least in classrooms, with somewhat less restricted access in staff areas.
How far does it go, do you start looking at staff laptops as a risk for hacking your servers, as well?
Linewize has sent out an email saying the BYOD is one risk and the other one is remote access from outside NZ.
Patrick Dunford
One of the schools I work with the staff have been demanding their logins have admin rights to install software.
Peter Eaton
Matthew Strickland
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-schools+unsub...@googlegroups.com.
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-schools+unsub...@googlegroups.com.
J B
The tech you are after for the sepm thing is directaccess which gives the laptops a persistent background transparent tunnel back to the school if they have a net connection.
Matthew Strickland
On Sunday, 17 July 2016 17:57:57 UTC+12, synack wrote:
The tech you are after for the sepm thing is directaccess which gives the laptops a persistent background transparent tunnel back to the school if they have a net connection.
Sent from my Windows 10 phone
<snip>
trevor storr
Alan at Wadestown School
flow in
not really. discussing attack vectors and security weaknesses is pertinent. I'm sure last time someone exploited a public ftp ip, rdp came up as a weakness. Only addressing the _last_ hack is a great way to be vulnerable, and we are very vulnerable.
Alan at Wadestown School
flow in
https://securelist.com/blog/research/75120/the-tip-of-the-iceberg-an-unexpected-turn-in-the-xdedic-story/?utm_medium=blg&utm_source=kb_post_160621&utm_campaign=ww_promo
Patrick Dunford
Patrick Dunford
flow in
ouch. apparently lots of us are dumb enough to use the default vlan, too.
Pretty sure that paper i linked talked about hacks on variant ports, too.
Patrick Dunford
Julian Davison
trevor storr
flow in
http://www.fail2ban.org/wiki/index.php/Main_Page
flow in