pfSense
Patrick Dunford
trevor storr
Has anyone got this running on Hyper-V in their system? Thoughts, insights?
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-sch...@googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
Trevor
Trevor Storr
Director of eLearning, CantaNET http://educo.vln.school.nz
Waimate High School
Waimate
New Zealand
J B
I have just put pfsense on a VMware box (just for it, everything else is hyperv) as I could not get it going on any of the three lots of actual hardware I tried it on and would have needed another dedicated Nic in the hyperv server to do it safely, it either would not recognize the nics, went into a reboot loop or could not install to the hard drive. Had issues with the config to when assigning interfaces, in the end giving it the exact hardware it expected via VMware so the defaults worked got it going. Seems to be alright now if a bit unstable when trying to change the config interface from http to https.
Good luck, I think it should work well when it is going but BSD is just a nightmare compatibility wise.
Jeffrey.
Sent from my Windows Phone
From: trevor storr
Sent: 30/03/2015 9:00 p.m.
To: techies-f...@googlegroups.com
Subject: Re: [techies-for-schools] pfSense
Patrick Dunford
Pete Eaton
Patrick Dunford
Pete Eaton
Julian Davison
Captive portal is the thing.
Wireless systems often do offer a captive portal; N4L’s user integration will do that too, as will Linewize, or pfSense.
Historically pfSense hasn’t played well with Hyper-V, but was fine under VMWare – the older versions were based on a FreeBSD that wasn’t very good with Hyper-V. I believe that the current versions (post-2.2) are using a more recent FreeBSD that behaves much better.
J,
Note:
If you are not the intended
recipient of this email, please contact the sender immediately by return email
or by telephone on +64 3 4718232. In this case please do not act in
reliance on this email or any attachments, and destroy all copies of them. The
views expressed in this email are those of the sender and not necessarily of
Decision1 IT Solutions Ltd.
P Please consider the environment before printing this e-mail
This e-mail has been scanned by MailMarshal. Any enquiries should be directed to :---: in...@decision1.co.nz
Patrick Dunford
Julian Davison
A captive portal is the usual answer to this.
Sitting at the gateway it requires users to sign into a web page in order to allow their device (essentially their IP) access to external resources. pfSense does this admirably (I believe it will even offer you different captive portals for different interfaces/VLANs now).
Transparent proxies are an entirely different can of worms with a whole new range of pitfalls.
Both N4L and Linewize have solutions that will do this for you, based on integration with some directory or other (both support AD) and allow things like site exceptions from authentication. They allow different categorisation based on source (user, or user-is-member-of-group, or IP) along with (presumably) logging where people have gone.
I’m not entirely sure how far along the release path N4Ls per-user captive-portal-esque system is, but there are sites using it fairly effectively.
Linewize is available fairly immediately, though there is a cost involved.
pfSense is available immediately, is free, but does take some setting up. If you’re leading into the term break it might be an opportune time to deploy it with some scope for experimentation – or I’m sure there are people here who can help (including me J)
J,
Tim Harper
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
Andrew Godfrey
Essentially the system for wireless devices would be
- open wireless connection or one with a very simple password
A more secure system would be 802.1x.
- transparent proxy (pfSense) for the web browser
I wonder how much savings you make or performance improvements there will be using a proxy. We had our firewall, NAT and proxy on pfsense and it was struggling so now it only does firewall and NAT. Still only averaging 200Mbps during class time. Slower connections may benefit from a proxy if it doesn't slow down your pfsense too much.
- authenticating behind the proxy with a logon screen that authenticates them against their user account for Windows (using some system)
Linewize works great for this but will not prompt if your first site is SSL (as any reasonable non-man-in-the-middle attack server should). Perhaps N4L(actually Spark/CISCO) is using some dodgy mechanism to get around this and that is what is tripping iOS8 up? But maybe I'm wrong about that.
Mike Etheridge
Julian Davison
That does seem to be an integral part of their filtering-ssl system. Not really clear how practical that is in the world of BYOD.
I’m aware of at least one school that has said yes…
From: techies-f...@googlegroups.com [mailto:techies-f...@googlegroups.com]
On Behalf Of Mike Etheridge
Sent: Thursday, 2 April 2015 12:27 p.m.
To: techies-f...@googlegroups.com
Subject: Re: [techies-for-schools] pfSense
When our N4L router was put in, they wanted to stick a certificate on it which our hosts would trust - essentially allowing them to carry out man-in-the-middle attacks. We said no. Maybe others said yes?
Julian Davison
What were you running pfSense on? Fundamentally pfSense’s proxy tends to be squid running on FreeBSD which isn’t inherently terrible. The squid process can be a complex one, though, as it processes cache-item-availability and the likes, and it can be quite IO heavy so is a bit more sensitive to specs than some other loads…
J,
From: techies-f...@googlegroups.com [mailto:techies-f...@googlegroups.com]
On Behalf Of Andrew Godfrey
Sent: Thursday, 2 April 2015 12:20 p.m.
To: techies-f...@googlegroups.com
Subject: Re: [techies-for-schools] pfSense
On 2 April 2015 at 11:11, Patrick Dunford <kahuk...@gmail.com> wrote:
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
techies-for-sch...@googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
Andrew Godfrey
What were you running pfSense on? Fundamentally pfSense’s proxy tends to be squid running on FreeBSD which isn’t inherently terrible. The squid process can be a complex one, though, as it processes cache-item-availability and the likes, and it can be quite IO heavy so is a bit more sensitive to specs than some other loads…
Tim Harper
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
--
Julian Davison
I’ll argue that. “Man in the middle” is a description of a technique, not an exploit title.
Putting something ‘in the middle’ that’s examining the traffic is an example of the “Man in the Middle” technique. That’s exactly what the Cisco system does. Secret or not.
J,
From: techies-f...@googlegroups.com [mailto:techies-f...@googlegroups.com]
On Behalf Of Tim Harper
Sent: Thursday, 2 April 2015 12:52 p.m.
To: techies-f...@googlegroups.com
Subject: Re: [techies-for-schools] pfSense
N4L and authentication: I'm trialling this with Cisco and it works really well.
Mike Etheridge
On 2/04/2015, at 12:48 pm, Andrew Godfrey <godf...@burnside.school.nz> wrote:
On 2 April 2015 at 12:31, Julian Davison <Jul...@decision1.co.nz> wrote:What were you running pfSense on? Fundamentally pfSense’s proxy tends to be squid running on FreeBSD which isn’t inherently terrible. The squid process can be a complex one, though, as it processes cache-item-availability and the likes, and it can be quite IO heavy so is a bit more sensitive to specs than some other loads…
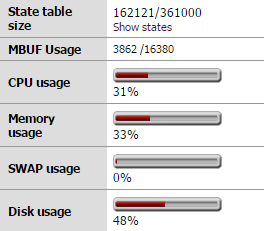
It's a fairly old ML110 with more memory than it first arrived with and several NICs added in as well. Squid is still running as some of our workstations haven't had their proxy settings removed but I've turned squidguard off as linewize has taken that job over. It's doing its job well at the moment so we'll leave it there for a little while longer.
<image.png>
_______________________________________Andrew Godfrey | Network Manager | Burnside High School | Christchurch | New Zealand
Patrick Dunford
Patrick Dunford
Patrick Dunford
I’ll argue that. “Man in the middle” is a description of a technique, not an exploit title.
Patrick Dunford
Tim Harper
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
Patrick Dunford
eaton...@gmail.com
Just a quick note that Google no longer mine student GAFE account and usage data for advertising, which was a valid concern for some when using their services at schools. Pete Saturday, 4 April 2015 1:44 pm +1300 from Patrick Dunford <kahuk...@gmail.com>: |
Tim Harper
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
Tim Harper
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
Andrew Godfrey
Hi Tim,
Do you also filter staff access this way?
Tim Harper
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
J B
If the N4L cert ever gets compromised, a softer target and possibly more lucrative than a single bank certificate there are going to be a large amount of devices and users open to exploitation.
I'll have to read more into the granular filtering somehow tied to LDAP as that could be useful but would be more than hesitant about using a third party global wildcard cert on devices for the same reasons I still throw up a firewall between N4L and hosts, the transparency of operation still is not there. What we get is 'yea, sure it's fine and secure, trust us', it may well be secure but without any real idea as to what is going on with the edge devices and no real consequences for n4l if they hash it everyone should take pause.
As with all of this stuff, no one is worried about the best case scenario but rather the worst case or that terrifying middle ground that MoE projects always seem to find. Where they demand to rip out half your network as an 'upgrade' or propone byod at all costs no matter if it is practical at all, in schools where kids don't get breakfast or lunch if the school does not provide it.
Sent from my Windows Phone
J B
Sent from my Windows Phone
Tim Harper
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
Mike Etheridge
Why not trust N4L? Because we don't know anything about their staff or their hiring policies. Our staff have to be police vetted. No disrespect intended, just a fact.
J B
Individual certs are better, I don't know about the platforms generation facility so there may still be holes but there always will be. There is a lot I don't know about it as the training never happened for it. Kind of like the Raspberry Pi that was supposedly something to do with it.
As to Apple I would not trust them as far as I could throw them and make decisions that include their competence and transparency as weighting factors.
N4L has a tough job of being trustable as it is an MoE project and there are a long line of burns and redirects I the past.
I never said that they could not be trusted but there is a saying, "trust but verify" and with N4L you can't verify as the device directly backing onto your network is a black box. Sure you can probe ports from the internet but that does not preclude a misconfig in the access lists letting some random internal N4L address have full access to internal hosts. There probably is not but you can't know and how can you honestly say to the school that you have protected their network (as best you can)when they are a config change away from an open network without anyone on site being any the wiser.
We now use the filtering which is good if a little annoying with its amateur hour green ticks and pop overs injected into searches. Still have and will for the foreseeable future have a firewall there though until the transparency is resolved. An old box with free VMware and pfsence is virtually free and will easily cope with the speeds I can manage through n4L even if it does limit filtering to one rule for all unless you static 1:1 Nat the whole set of ranges which is something I'm considering.
Jeffrey.
Sent from my Windows Phone
Tim Harper
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
J B
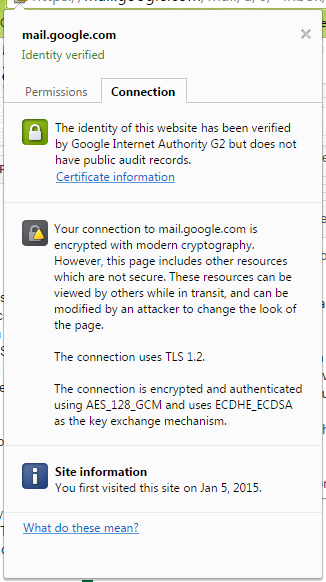
Oh realized I did not explain the cert bit, what I mean is check the cert in the browser title bar padlock bit to make sure it is not the inspection one when banking If that cert ever got compromised any device with it on could be vulnerable on whatever network. If using those certs the user should check beforehand that the cert is the right one incase for some reason the inspection is on for it or its being spoofed. You can't do this in stuff like phone apps. The main point is though that a trusted universal wildcard cert on a device opens it up to new threats and these should also be considered.
Thanks, I can get access to that area so may well switch that off as several of the staff were rightly concerned that their computers had been compromised by malware thanks to the pop overs and different behavior between home and work.
Sent from my Windows Phone
Mike Etheridge
Actually, Tim, I am serious. The Google mail example doesn't stack up. I can ( and do, off my phone) encrypt my mail because I actually don't trust Google. As a netadmin, I don't choose to subvert the intention of end to end secure connection that SSL is supposed to deliver. I won't train my users to agree to give away that security to a man in the middle.
This whole thing comes down to trust, but not between users and middle men (basic instruction: do not trust them) but between members of the school community. In a low trust model, there is no trust between staff and students (and management and lower levels), and low trust organizations are characterised by rigid hierarchies, centralized decision making, predetermined outcomes and high handed unilateral violation of privacy. High trust models are associated with needs and interest based networking, devolved decision making, flexibility, respect for the individual, innovation and fun. I know what kind of organization I prefer to belong to, and I will always promote the associated values.
Mike
Tim Harper
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
Tim Harper
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
Patrick Dunford
Mike Etheridge
I think you missed the point there. I'm talking about trusting our students and working SSL how it is intended. Not pretending to trust them (giving access to secure ports) then snooping anyway. That's worse than open distrust. Distrusting your ISP (and everyone else in the middle) on the other hand should be SOP.
Getting into trouble here for work emailing on holiday....
Patrick Dunford
Tim Harper
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
Tim Harper
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
Ict Technician
It was my opinion, and he reinforced it, that i was responsible for ensuring that the minors using the school network were not able to access objectionable material, or engage in illegal activity, with the proviso that if they deliberately work around reasonable restrictions then i'm not liable unless i know about it and fail to act.
The 'man in the middle' approach that n4l is taking to allow SSL traffic analysis is a good thing. Many big time network security appliances provide exactly such a service, with the responsibility for the security of their certificates (and the liability) being that of the service provider. It may make us feel powerless, but we are no more or less powerless than when any other certificate is used, beyond the scope of the potential breech.
We are not using n4l yet but plan to move on it as other workloads decrease. Having read everyone's concerns, the only thing i'd ask for was that i could exempt certain sites from packet interception. Namely banking sites (just in case), but potentially any that staff asked for. rather than throw around statements claiming that using the system will break banking t&c, i'd contact the banks and ask them.
I'd also ask n4l for a statement on liability. If they are not willing to wear it, then i wouldn't use the service.
Having SSL inspection is far more useful than dangerous, imo. Forced google safe search on https (a DNS fix requiring external DNS request blocking and breaking things like google voice search) is by-passable with simple IP based search request, or by using alternative search engines. I trust n4l more than i trust a 12 year old.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-schools+unsub...@googlegroups.com.
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-schools+unsub...@googlegroups.com.
Note:
If you are not the intended recipient of this email, please contact the sender immediately by return email or by telephone on +64 3 4718232. In this case please do not act in reliance on this email or any attachments, and destroy all copies of them. The views expressed in this email are those of the sender and not necessarily of Decision1 IT Solutions Ltd.
P Please consider the environment before printing this e-mail
This e-mail has been scanned by MailMarshal. Any enquiries should be directed to :---: in...@decision1.co.nz
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-schools+unsub...@googlegroups.com.
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-schools+unsub...@googlegroups.com.
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-schools+unsub...@googlegroups.com.
Tim Harper
Identified user 'nameremovedbyTimforprivacyreasons' from IP address 210.54.147.17 as part of company 'N4L_533_mtaspiringcollege'
User belongs to groups [mtaspiringcollege-standard, WinNT://master\Social-Media-OK, WinNT://master\MacSenior] User belongs to static groups [mtaspiringcollege-standard, WinNT://master\Social-Media-OK, WinNT://master\MacSenior, Statics, ISR Router] Site categorized as 'Social Networking' Evaluating 21 rules after reading request headers Evaluating rule 'School - Enforced Allow' Rule 'School - Enforced Allow' doesn't match Evaluating rule 'Direct_Out_Permitted_No_Auth' Rule 'Direct_Out_Permitted_No_Auth' doesn't match Evaluating rule 'MAC_Authenticate' Evaluating rule 'Students_Banned' Rule 'Students_Banned' doesn't match Evaluating rule 'No_Student_Access_HTTPS' Rule 'No_Student_Access_HTTPS' doesn't match Evaluating rule 'Unauthenticated YouTube' Rule 'Unauthenticated YouTube' doesn't match Evaluating rule 'Standard_Allow' Rule 'Standard_Allow' doesn't match Evaluating rule 'Authenticated Staff' Rule 'Authenticated Staff' doesn't match Evaluating rule 'Authenticated Block' Rule 'Authenticated Block' doesn't match Evaluating rule 'Social_Media_OK_1_2' Rule 'Social_Media_OK_1_2' doesn't match Evaluating rule 'Social_Media_OK_3_4' Taking allow action because of category 'Social Networking' Evaluating 0 rules at stage reqmod Evaluating 1 HTTPS rules HTTPS rule 'MAC_SSL' matches, using certificate 'N4L' to decrypt
Identified user 'nameremovedbyTimforprivacyreasons' from IP address 210.54.147.17 as part of company 'N4L_533_mtaspiringcollege'
User belongs to groups [mtaspiringcollege-standard, WinNT://master\Social-Media-OK, WinNT://master\MacSenior] User belongs to static groups [mtaspiringcollege-standard, WinNT://master\Social-Media-OK, WinNT://master\MacSenior, Statics, ISR Router] Site categorized as 'Finance'
Evaluating 21 rules after reading request headers Evaluating rule 'School - Enforced Allow' Rule 'School - Enforced Allow' doesn't match Evaluating rule 'Direct_Out_Permitted_No_Auth' Rule 'Direct_Out_Permitted_No_Auth' doesn't match Evaluating rule 'MAC_Authenticate' Evaluating rule 'Students_Banned' Rule 'Students_Banned' doesn't match Evaluating rule 'No_Student_Access_HTTPS' Rule 'No_Student_Access_HTTPS' doesn't match Evaluating rule 'Unauthenticated YouTube' Rule 'Unauthenticated YouTube' doesn't match Evaluating rule 'Standard_Allow' Rule 'Standard_Allow' doesn't match Evaluating rule 'Authenticated Staff' Rule 'Authenticated Staff' doesn't match Evaluating rule 'Authenticated Block' Rule 'Authenticated Block' doesn't match Evaluating rule 'Social_Media_OK_1_2' Rule 'Social_Media_OK_1_2' doesn't match Evaluating rule 'Social_Media_OK_3_4' Rule 'Social_Media_OK_3_4' doesn't match Evaluating rule 'Social_Media_OK_6' Rule 'Social_Media_OK_6' doesn't match Evaluating rule 'Student_Social_Block_1_2_HTTPS' Rule 'Student_Social_Block_1_2_HTTPS' doesn't match Evaluating rule 'Student_Social_Block_3_4_HTTPS' Rule 'Student_Social_Block_3_4_HTTPS' doesn't match Evaluating rule 'Student_Social_Block_6_HTTPS' Rule 'Student_Social_Block_6_HTTPS' doesn't match Evaluating rule 'Hostel_Prep_HTTPS' Rule 'Hostel_Prep_HTTPS' doesn't match Evaluating rule 'Authenticated_Allow_Explicit_Words' Rule 'Authenticated_Allow_Explicit_Words' doesn't match Evaluating rule 'Standard_Block' Rule 'Standard_Block' doesn't match Evaluating rule 'School - Enforced BLOCK' Rule 'School - Enforced BLOCK' doesn't match Evaluating rule 'Explict_keyword_master' Rule 'Explict_keyword_master' doesn't match Evaluating default rule at stage reqmod Taking allow action because of adv-rule-match 'No exception exists to allow this web page' Evaluating 0 rules at stage reqmod Evaluating 1 HTTPS rules HTTPS rule 'MAC_SSL' doesnt match
regards,
Tim Harper
Phone 0800 755 966 option 2 then 3 (SchoolZone)
Phone 03 443 5167 (DDI)
Mobile 027 443 1236
Fax 03 443 0491
t...@mtaspiring.school.nz
www.mtaspiring.school.nz
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-sch...@googlegroups.com.
trevor storr
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-sch...@googlegroups.com.
Trevor
Trevor Storr
Director of eLearning, CantaNET http://educo.vln.school.nz
Waimate High School
Waimate
New Zealand
Julian Davison
The trick with the ‘knowingly allowed’ test is that it’s either never true (You “know” that your filtering is failsafe) or always true (You recognise that any filtering system is flawed and can be bypassed). A technical solution to a social problem can only ever be ‘best effort’ and/or ‘reasonable effort’. As soon as you introduce customised filtering (different users/devices have different access) the can of worms becomes larger as you have to include the users in the equation – have they taken suitable precautions? Have you taken suitable steps to make them aware of suitable precautions? Legal issues are best left with the lawyer that’s going to have to defend the position they advise J
The ‘man in the middle’ approach is nothing more than a technique for snooping on content that’s intended to be unsnoopable. The two points of debate are whether or not deliberately putting a man in the middle lowers overall security and whether or not you should be snooping on the traffic in any case.
They are similar and related, but also separate arguments (and end-game, security is really about what you *can* do, not what you *actually* do – you *can* snoop on arbitrary SSL sites without notifying the user is the concern).
I like N4L overall. There are aspects which could potentially be improved, and alternatives that can be used to augment the N4L offering. It’s still a good path to go down, and seems to be getting better…
J,
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-sch...@googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-sch...@googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
Note:
If you are not the intended recipient of this email, please contact the sender immediately by return email or by telephone on +64 3 4718232. In this case please do not act in reliance on this email or any attachments, and destroy all copies of them. The views expressed in this email are those of the sender and not necessarily of Decision1 IT Solutions Ltd.
P Please consider the environment before printing this e-mail
This e-mail has been scanned by MailMarshal. Any enquiries should be directed to :---: in...@decision1.co.nz
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-sch...@googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-sch...@googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-sch...@googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to techies-for-sch...@googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
Patrick Dunford
Julian Davison
In an ideal world, that would be both true and adhered to by all users. In the schools I’ve dealt with it tends to be a little less black and white in reality.
From: techies-f...@googlegroups.com [mailto:techies-f...@googlegroups.com]
On Behalf Of Patrick Dunford
Sent: Tuesday, 7 April 2015 1:21 p.m.
To: techies-f...@googlegroups.com
Subject: Re: [techies-for-schools] pfSense
To me it’s simple, the network is for school use only, there should be no issue for school purposes as compared to personal purposes.
--
You received this message because you are subscribed to the Google Groups "Techies for schools" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
techies-for-sch...@googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
