Missing certificate in metadata
931 views
Skip to first unread message
Dick Visser
Jan 6, 2014, 6:00:05 AM1/6/14
to simplesamlphp
Hi guys
I'm trying to connect our SSP IdP to a new service provider called CrashPlan.
I already found out that this SP needs HTTP-POST, so I upgraded to
trunk (which included the composer.phar stuff).
Anyway, the metadata for the SP is
https://crashplan.terena.org:4285/api/SsoAuthSpMetadata:
<?xml version="1.0" encoding="UTF-8"?>
<md:EntityDescriptor entityID="https://crashplan.terena.org:4285"
xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata">
<md:SPSSODescriptor AuthnRequestsSigned="true"
WantAssertionsSigned="true"
protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="encryption">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:KeyValue>
<ds:RSAKeyValue>
<ds:Modulus>q0/dV5P0n5MJ+bvbpzxik8TQ1hHdXxIG7CYb0/XEuxLNNgu+fdZORwV0Jius7zICTlAPIibxRWeE
DtaGxW+xriIwOjLU6KRqmuVL8/vZVD3+WtqVyTQv5QpOEaZUNUb0ffCCXKR4nTWFR6YGYcp1LSY9
H4QrldQxN7sWZuY6tfcL8kLdJE+035liu/BD8utW4xHP9OnO3h8cncu3v0fFKw0GPZojDD8ikn7Z
ZnO35GR0N6pJmmK1IaJOmyt0gtsTE0K7uTrSqayNyCJsynfTbHejHbcrl/reO1njVjRji3o2FhLk
c0XXvz4WWV9arbUy0kvzomhTI3bJGtOYDXA0tw==</ds:Modulus>
<ds:Exponent>AQAB</ds:Exponent>
</ds:RSAKeyValue>
</ds:KeyValue>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:KeyValue>
<ds:RSAKeyValue>
<ds:Modulus>q0/dV5P0n5MJ+bvbpzxik8TQ1hHdXxIG7CYb0/XEuxLNNgu+fdZORwV0Jius7zICTlAPIibxRWeE
DtaGxW+xriIwOjLU6KRqmuVL8/vZVD3+WtqVyTQv5QpOEaZUNUb0ffCCXKR4nTWFR6YGYcp1LSY9
H4QrldQxN7sWZuY6tfcL8kLdJE+035liu/BD8utW4xHP9OnO3h8cncu3v0fFKw0GPZojDD8ikn7Z
ZnO35GR0N6pJmmK1IaJOmyt0gtsTE0K7uTrSqayNyCJsynfTbHejHbcrl/reO1njVjRji3o2FhLk
c0XXvz4WWV9arbUy0kvzomhTI3bJGtOYDXA0tw==</ds:Modulus>
<ds:Exponent>AQAB</ds:Exponent>
</ds:RSAKeyValue>
</ds:KeyValue>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</md:NameIDFormat>
<md:AssertionConsumerService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Location="https://crashplan.terena.org:4285/api/SsoAuthLoginResponse"
index="0" isDefault="true"/>
</md:SPSSODescriptor>
<md:Organization>
<md:OrganizationName xml:lang="en">CrashPlan PROe
Server</md:OrganizationName>
<md:OrganizationDisplayName xml:lang="en">CrashPlan PROe
Server</md:OrganizationDisplayName>
<md:OrganizationURL
xml:lang="en">https://crashplan.terena.org:4285</md:OrganizationURL>
</md:Organization>
<md:ContactPerson contactType="technical">
<md:Company>CrashPlan PROe Server</md:Company>
<md:EmailAddress>sysa...@terena.org</md:EmailAddress>
</md:ContactPerson>
</md:EntityDescriptor>
When I paste this into the Metadata parser at
https://login.terena.org/idp/admin/metadata-converter.php, I get this
array back:
$metadata['https://crashplan.terena.org:4285'] = array (
'entityid' => 'https://crashplan.terena.org:4285',
'name' =>
array (
'en' => 'CrashPlan PROe Server',
),
'description' =>
array (
'en' => 'CrashPlan PROe Server',
),
'OrganizationName' =>
array (
'en' => 'CrashPlan PROe Server',
),
'OrganizationDisplayName' =>
array (
'en' => 'CrashPlan PROe Server',
),
'url' =>
array (
'en' => 'https://crashplan.terena.org:4285',
),
'OrganizationURL' =>
array (
'en' => 'https://crashplan.terena.org:4285',
),
'contacts' =>
array (
0 =>
array (
'contactType' => 'technical',
'company' => 'CrashPlan PROe Server',
'emailAddress' =>
array (
0 => 'sysa...@terena.org',
),
),
),
'metadata-set' => 'saml20-sp-remote',
'AssertionConsumerService' =>
array (
0 =>
array (
'Binding' => 'urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST',
'Location' =>
'https://crashplan.terena.org:4285/api/SsoAuthLoginResponse',
'index' => 0,
'isDefault' => true,
),
),
'SingleLogoutService' =>
array (
),
'NameIDFormat' => 'urn:oasis:names:tc:SAML:2.0:nameid-format:transient',
'validate.authnrequest' => true,
'saml20.sign.assertion' => true,
);
I added this to saml20-sp-remote.php, but when I try to log in to the SP I get:
Backtrace:
1 /usr/share/simplesamlphp/idp.r3313/www/_include.php:37
(SimpleSAML_exception_handler)
0 [builtin] (N/A)
Caused by: SimpleSAML_Error_Exception: Missing certificate in metadata
for 'https://crashplan.terena.org:4285'
Backtrace:
3 /usr/share/simplesamlphp/idp.r3313/modules/saml/lib/Message.php:178
(sspmod_saml_Message::checkSign)
2 /usr/share/simplesamlphp/idp.r3313/modules/saml/lib/Message.php:252
(sspmod_saml_Message::validateMessage)
1 /usr/share/simplesamlphp/idp.r3313/modules/saml/lib/IdP/SAML2.php:298
(sspmod_saml_IdP_SAML2::receiveAuthnRequest)
0 /usr/share/simplesamlphp/idp.r3313/www/saml2/idp/SSOService.php:19 (N/A)
It looks like the ds:RSAKeyValue stuff isn't represented anywhere in
the the PHP array - which means that it's lost.
Could this be the problem?
Thanks!!
--
Dick Visser
System & Networking Engineer
TERENA Secretariat
Singel 468 D, 1017 AW Amsterdam
The Netherlands
I'm trying to connect our SSP IdP to a new service provider called CrashPlan.
I already found out that this SP needs HTTP-POST, so I upgraded to
trunk (which included the composer.phar stuff).
Anyway, the metadata for the SP is
https://crashplan.terena.org:4285/api/SsoAuthSpMetadata:
<?xml version="1.0" encoding="UTF-8"?>
<md:EntityDescriptor entityID="https://crashplan.terena.org:4285"
xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata">
<md:SPSSODescriptor AuthnRequestsSigned="true"
WantAssertionsSigned="true"
protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="encryption">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:KeyValue>
<ds:RSAKeyValue>
<ds:Modulus>q0/dV5P0n5MJ+bvbpzxik8TQ1hHdXxIG7CYb0/XEuxLNNgu+fdZORwV0Jius7zICTlAPIibxRWeE
DtaGxW+xriIwOjLU6KRqmuVL8/vZVD3+WtqVyTQv5QpOEaZUNUb0ffCCXKR4nTWFR6YGYcp1LSY9
H4QrldQxN7sWZuY6tfcL8kLdJE+035liu/BD8utW4xHP9OnO3h8cncu3v0fFKw0GPZojDD8ikn7Z
ZnO35GR0N6pJmmK1IaJOmyt0gtsTE0K7uTrSqayNyCJsynfTbHejHbcrl/reO1njVjRji3o2FhLk
c0XXvz4WWV9arbUy0kvzomhTI3bJGtOYDXA0tw==</ds:Modulus>
<ds:Exponent>AQAB</ds:Exponent>
</ds:RSAKeyValue>
</ds:KeyValue>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:KeyValue>
<ds:RSAKeyValue>
<ds:Modulus>q0/dV5P0n5MJ+bvbpzxik8TQ1hHdXxIG7CYb0/XEuxLNNgu+fdZORwV0Jius7zICTlAPIibxRWeE
DtaGxW+xriIwOjLU6KRqmuVL8/vZVD3+WtqVyTQv5QpOEaZUNUb0ffCCXKR4nTWFR6YGYcp1LSY9
H4QrldQxN7sWZuY6tfcL8kLdJE+035liu/BD8utW4xHP9OnO3h8cncu3v0fFKw0GPZojDD8ikn7Z
ZnO35GR0N6pJmmK1IaJOmyt0gtsTE0K7uTrSqayNyCJsynfTbHejHbcrl/reO1njVjRji3o2FhLk
c0XXvz4WWV9arbUy0kvzomhTI3bJGtOYDXA0tw==</ds:Modulus>
<ds:Exponent>AQAB</ds:Exponent>
</ds:RSAKeyValue>
</ds:KeyValue>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</md:NameIDFormat>
<md:AssertionConsumerService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Location="https://crashplan.terena.org:4285/api/SsoAuthLoginResponse"
index="0" isDefault="true"/>
</md:SPSSODescriptor>
<md:Organization>
<md:OrganizationName xml:lang="en">CrashPlan PROe
Server</md:OrganizationName>
<md:OrganizationDisplayName xml:lang="en">CrashPlan PROe
Server</md:OrganizationDisplayName>
<md:OrganizationURL
xml:lang="en">https://crashplan.terena.org:4285</md:OrganizationURL>
</md:Organization>
<md:ContactPerson contactType="technical">
<md:Company>CrashPlan PROe Server</md:Company>
<md:EmailAddress>sysa...@terena.org</md:EmailAddress>
</md:ContactPerson>
</md:EntityDescriptor>
When I paste this into the Metadata parser at
https://login.terena.org/idp/admin/metadata-converter.php, I get this
array back:
$metadata['https://crashplan.terena.org:4285'] = array (
'entityid' => 'https://crashplan.terena.org:4285',
'name' =>
array (
'en' => 'CrashPlan PROe Server',
),
'description' =>
array (
'en' => 'CrashPlan PROe Server',
),
'OrganizationName' =>
array (
'en' => 'CrashPlan PROe Server',
),
'OrganizationDisplayName' =>
array (
'en' => 'CrashPlan PROe Server',
),
'url' =>
array (
'en' => 'https://crashplan.terena.org:4285',
),
'OrganizationURL' =>
array (
'en' => 'https://crashplan.terena.org:4285',
),
'contacts' =>
array (
0 =>
array (
'contactType' => 'technical',
'company' => 'CrashPlan PROe Server',
'emailAddress' =>
array (
0 => 'sysa...@terena.org',
),
),
),
'metadata-set' => 'saml20-sp-remote',
'AssertionConsumerService' =>
array (
0 =>
array (
'Binding' => 'urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST',
'Location' =>
'https://crashplan.terena.org:4285/api/SsoAuthLoginResponse',
'index' => 0,
'isDefault' => true,
),
),
'SingleLogoutService' =>
array (
),
'NameIDFormat' => 'urn:oasis:names:tc:SAML:2.0:nameid-format:transient',
'validate.authnrequest' => true,
'saml20.sign.assertion' => true,
);
I added this to saml20-sp-remote.php, but when I try to log in to the SP I get:
Backtrace:
1 /usr/share/simplesamlphp/idp.r3313/www/_include.php:37
(SimpleSAML_exception_handler)
0 [builtin] (N/A)
Caused by: SimpleSAML_Error_Exception: Missing certificate in metadata
for 'https://crashplan.terena.org:4285'
Backtrace:
3 /usr/share/simplesamlphp/idp.r3313/modules/saml/lib/Message.php:178
(sspmod_saml_Message::checkSign)
2 /usr/share/simplesamlphp/idp.r3313/modules/saml/lib/Message.php:252
(sspmod_saml_Message::validateMessage)
1 /usr/share/simplesamlphp/idp.r3313/modules/saml/lib/IdP/SAML2.php:298
(sspmod_saml_IdP_SAML2::receiveAuthnRequest)
0 /usr/share/simplesamlphp/idp.r3313/www/saml2/idp/SSOService.php:19 (N/A)
It looks like the ds:RSAKeyValue stuff isn't represented anywhere in
the the PHP array - which means that it's lost.
Could this be the problem?
Thanks!!
--
Dick Visser
System & Networking Engineer
TERENA Secretariat
Singel 468 D, 1017 AW Amsterdam
The Netherlands
Olav Morken
Jan 6, 2014, 7:12:34 AM1/6/14
to simple...@googlegroups.com
metadata (though I agree that is cleaner that using a X509 certificate
and discarding everything but the RSA public key).
I don't really have any good solutions for you. Unless you can configure
CrashPlan to include a certificate in your metadata, the only
short-term solution is to build a certificate yourself based on the RSA
public key.
Unfortunately, I am not aware of any tools that allow you to take an
RSA public key and create a certificate from it. In theory it is
entirely doable -- just fill in the certificate details and sign it
using a random private key. I just think it is an unusual use-case.
(If CrashPlan allows you to retrieve the RSA private key, creating a
certificate using that should be far more straightforward.)
Best regards,
Olav Morken
UNINETT / Feide
Thijs Kinkhorst
Jan 6, 2014, 7:17:36 AM1/6/14
to simple...@googlegroups.com
Op maandag 6 januari 2014 13:12:34 schreef Olav Morken:
See the _getPublicKeyFromModExp() method in
modules/InfoCard/lib/RP/Zend_InfoCard_Xml_Security.php.
--
Thijs Kinkhorst <th...@uvt.nl> – LIS Unix
Universiteit van Tilburg – Library and IT Services • Postbus 90153, 5000 LE
Bezoekadres > Warandelaan 2 • Tel. 013 466 3035 • G 236 • http://www.uvt.nl
> I don't really have any good solutions for you. Unless you can configure
> CrashPlan to include a certificate in your metadata, the only
> short-term solution is to build a certificate yourself based on the RSA
> public key.
>
> Unfortunately, I am not aware of any tools that allow you to take an
> RSA public key and create a certificate from it. In theory it is
> entirely doable -- just fill in the certificate details and sign it
> using a random private key. I just think it is an unusual use-case.
I think there's code in the simpleSAMLphp distribution that should solve this.
> CrashPlan to include a certificate in your metadata, the only
> short-term solution is to build a certificate yourself based on the RSA
> public key.
>
> Unfortunately, I am not aware of any tools that allow you to take an
> RSA public key and create a certificate from it. In theory it is
> entirely doable -- just fill in the certificate details and sign it
> using a random private key. I just think it is an unusual use-case.
See the _getPublicKeyFromModExp() method in
modules/InfoCard/lib/RP/Zend_InfoCard_Xml_Security.php.
--
Thijs Kinkhorst <th...@uvt.nl> – LIS Unix
Universiteit van Tilburg – Library and IT Services • Postbus 90153, 5000 LE
Bezoekadres > Warandelaan 2 • Tel. 013 466 3035 • G 236 • http://www.uvt.nl
Dick Visser
Jan 6, 2014, 10:18:58 AM1/6/14
to simplesamlphp
On 6 January 2014 13:12, Olav Morken <olav....@uninett.no> wrote:
> Yes, we don't currently support using "pure" RSA public keys in
> metadata (though I agree that is cleaner that using a X509 certificate
> and discarding everything but the RSA public key).
>
> I don't really have any good solutions for you. Unless you can configure
> CrashPlan to include a certificate in your metadata, the only
> short-term solution is to build a certificate yourself based on the RSA
> public key.
>
> Unfortunately, I am not aware of any tools that allow you to take an
> RSA public key and create a certificate from it. In theory it is
> entirely doable -- just fill in the certificate details and sign it
> using a random private key. I just think it is an unusual use-case.
>
> (If CrashPlan allows you to retrieve the RSA private key, creating a
> certificate using that should be far more straightforward.)
> Yes, we don't currently support using "pure" RSA public keys in
> metadata (though I agree that is cleaner that using a X509 certificate
> and discarding everything but the RSA public key).
>
> I don't really have any good solutions for you. Unless you can configure
> CrashPlan to include a certificate in your metadata, the only
> short-term solution is to build a certificate yourself based on the RSA
> public key.
>
> Unfortunately, I am not aware of any tools that allow you to take an
> RSA public key and create a certificate from it. In theory it is
> entirely doable -- just fill in the certificate details and sign it
> using a random private key. I just think it is an unusual use-case.
>
> (If CrashPlan allows you to retrieve the RSA private key, creating a
> certificate using that should be far more straightforward.)
Actually,
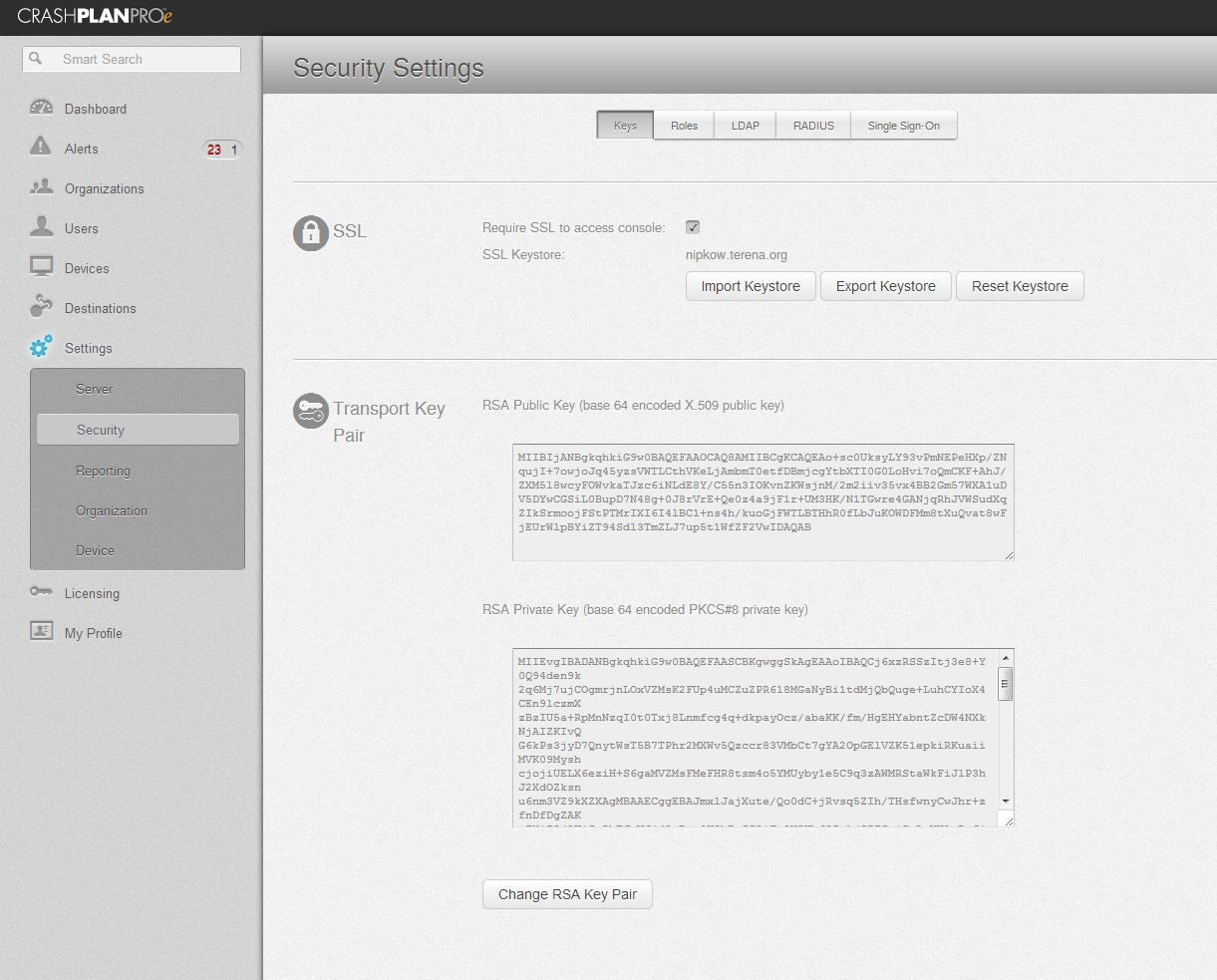
their management web interface does seem to support it
:
So I'll give this a try first.
Dick Visser
Jan 6, 2014, 11:20:46 AM1/6/14
to simplesamlphp
> (If CrashPlan allows you to retrieve the RSA private key, creating a
> certificate using that should be far more straightforward.)
In tried to do that:
> certificate using that should be far more straightforward.)
1. Copy the text in "RSA Private Key (base 64 encoded PKCS#8 private
key)" to a file key.der.base64, then extract the private key:
openssl enc -base64 -in key.der.base64 -d | openssl pkcs8 -inform DER -nocrypt
Then I generate self-signed certificate with this private key:
openssl req -new -x509 -key private.key -out cert.pem -days 36500
Then I stripped the tabs and headers:
openssl base64 -d -in cert.pem | base64 -w 0
I then add the resulting certificate to the metadata:
'keys' =>
array (
0 =>
array (
'encryption' => false,
0 =>
array (
'signing' => true,
'type' => 'X509Certificate',
'X509Certificate' =>
'MIIECTCCAvGgAwIBAgIJAM4Jf5h5Hh4pMA0GCSqGSIb3DQEBBQUAMIGZMQswCQYDVQQGEwJOTDELMAkGA1UECAwCTkgxFDASBgNVBAcMC0Ftc3RlcmRhbXp6MQ8wDQYDVQQKDAZURVJFTkExEzARBgNVBAsMCklUIFN1cHBvcnQxHTAbBgNVBAMMFGNyYXNocGxhbi50ZXJlbmEub3JnMSIwIAYJKoZIhvcNAQkBFhNzeXNhZG1pbkB0ZXJlbmEub3JnMCAXDTE0MDEwNjE1NTczNloYDzIxMTMxMjEzMTU1NzM2WjCBmTELMAkGA1UEBhMCTkwxCzAJBgNVBAgMAk5IMRQwEgYDVQQHDAtBbXN0ZXJkYW16ejEPMA0GA1UECgwGVEVSRU5BMRMwEQYDVQQLDApJVCBTdXBwb3J0MR0wGwYDVQQDDBRjcmFzaHBsYW4udGVyZW5hLm9yZzEiMCAGCSqGSIb3DQEJARYTc3lzYWRtaW5AdGVyZW5hLm9yZzCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKPrHNFJLMi2Pd7z5jRD3h16f2TaroyPu6MI6CauOcs7FVkywrYVSni4wJm5k9HrXwwZo3IGLW10yNBtC6B74u6EJgihfgISf2VzOZfMHMhTlr5Gkyc3OojS3RPGPwueZ9yDir52SlrI5zP9ptoor9+b8eAQdhpue1lwNbg1eQ2MAhkoi9AbqQ+zePIPtCfK1axPkHtM+GvYxda/lDNxyvzdUxsK3uBgDY6kYSVVkrnV6mSJEq5qKIxUrT0zKyFyOiOJQQtfp7OIf5LqBoxVkywUx4UdHy2ybijlgxTJvLV7kL2rfMBYxFK1paQWImU/eEnZd05mSye7qebdVn2RdlcCAwEAAaNQME4wHQYDVR0OBBYEFIIpGxQ6C/D0r1tGeeUZkqC0Yst1MB8GA1UdIwQYMBaAFIIpGxQ6C/D0r1tGeeUZkqC0Yst1MAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQEFBQADggEBAHPMIl2kY7RA09n8I2nrFSr2lgY64Vtv24DL+krAvwRwC6s5QTzi6PdwAQHvsV1PI+PLihKZRBcGdV/pLGsb11588849bYAst8dPFbphDfHst7ypRSono7w5dDqiBOygjuSWJgY5uWO5nQ8D82VjYwMGsECq5naw+MvGDSk8Ncm6e9x5p2Pq66abWdYvs84xdtfpTcl0MuQ+o0fM7cHPjx17+Rg3/dDRAWfomPmdw6Z1iHhtCOe5Vddf16OvckFW/qFIAh59cvab+DNYgXHOnATwIT6C2GUReSQWY9gN8RL6VXtP9GNG+dXPfeX8ED7Fz5GMuI7SiDSWxyv9/uNGKaI=',
),
1 =>
array (
'encryption' => true,
'signing' => false,
'type' => 'X509Certificate',
'X509Certificate' =>
'MIIECTCCAvGgAwIBAgIJAM4Jf5h5Hh4pMA0GCSqGSIb3DQEBBQUAMIGZMQswCQYDVQQGEwJOTDELMAkGA1UECAwCTkgxFDASBgNVBAcMC0Ftc3RlcmRhbXp6MQ8wDQYDVQQKDAZURVJFTkExEzARBgNVBAsMCklUIFN1cHBvcnQxHTAbBgNVBAMMFGNyYXNocGxhbi50ZXJlbmEub3JnMSIwIAYJKoZIhvcNAQkBFhNzeXNhZG1pbkB0ZXJlbmEub3JnMCAXDTE0MDEwNjE1NTczNloYDzIxMTMxMjEzMTU1NzM2WjCBmTELMAkGA1UEBhMCTkwxCzAJBgNVBAgMAk5IMRQwEgYDVQQHDAtBbXN0ZXJkYW16ejEPMA0GA1UECgwGVEVSRU5BMRMwEQYDVQQLDApJVCBTdXBwb3J0MR0wGwYDVQQDDBRjcmFzaHBsYW4udGVyZW5hLm9yZzEiMCAGCSqGSIb3DQEJARYTc3lzYWRtaW5AdGVyZW5hLm9yZzCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKPrHNFJLMi2Pd7z5jRD3h16f2TaroyPu6MI6CauOcs7FVkywrYVSni4wJm5k9HrXwwZo3IGLW10yNBtC6B74u6EJgihfgISf2VzOZfMHMhTlr5Gkyc3OojS3RPGPwueZ9yDir52SlrI5zP9ptoor9+b8eAQdhpue1lwNbg1eQ2MAhkoi9AbqQ+zePIPtCfK1axPkHtM+GvYxda/lDNxyvzdUxsK3uBgDY6kYSVVkrnV6mSJEq5qKIxUrT0zKyFyOiOJQQtfp7OIf5LqBoxVkywUx4UdHy2ybijlgxTJvLV7kL2rfMBYxFK1paQWImU/eEnZd05mSye7qebdVn2RdlcCAwEAAaNQME4wHQYDVR0OBBYEFIIpGxQ6C/D0r1tGeeUZkqC0Yst1MB8GA1UdIwQYMBaAFIIpGxQ6C/D0r1tGeeUZkqC0Yst1MAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQEFBQADggEBAHPMIl2kY7RA09n8I2nrFSr2lgY64Vtv24DL+krAvwRwC6s5QTzi6PdwAQHvsV1PI+PLihKZRBcGdV/pLGsb11588849bYAst8dPFbphDfHst7ypRSono7w5dDqiBOygjuSWJgY5uWO5nQ8D82VjYwMGsECq5naw+MvGDSk8Ncm6e9x5p2Pq66abWdYvs84xdtfpTcl0MuQ+o0fM7cHPjx17+Rg3/dDRAWfomPmdw6Z1iHhtCOe5Vddf16OvckFW/qFIAh59cvab+DNYgXHOnATwIT6C2GUReSQWY9gN8RL6VXtP9GNG+dXPfeX8ED7Fz5GMuI7SiDSWxyv9/uNGKaI=',
),
),
But now the signature can't be verified:
Jan 06 17:12:04 simplesamlphp INFO [06e111d47e] SAML2.0 -
IdP.SSOService: Accessing SAML 2.0 IdP endpoint SSOService
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] Received message:
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] <saml2p:AuthnRequest
xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol"
AssertionConsumerServiceURL="https://crashplan.terena.org:4285/api/SsoAuthLoginResponse"
Destination="https://login.terena.org/idp/saml2/idp/SSOService.php"
ForceAuthn="false" ID="_7d6a6a24-0e18-
4d94-9685-32d0e606d641" IsPassive="false"
IssueInstant="2014-01-06T16:10:22.500Z"
ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Version="2.0">
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] <saml2:Issuer
xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">https://crashplan.terena.org:4285</saml2:Issuer>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
<saml2p:NameIDPolicy AllowCreate="true"
SPNameQualifier="https://crashplan.terena.org:4285"/>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
<saml2p:RequestedAuthnContext Comparison="exact"/>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] <Signature
xmlns="http://www.w3.org/2000/09/xmldsig#">
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] <SignedInfo>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
<CanonicalizationMethod
Algorithm="http://www.w3.org/TR/2001/REC-xml-c14n-20010315"/>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
<SignatureMethod
Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] <Reference URI="">
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] <Transforms>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] <Transform
Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] </Transforms>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] <DigestMethod
Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
<DigestValue>5hj2bk+X21QBOLvrKtVORpALGBU=</DigestValue>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] </Reference>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] </SignedInfo>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
<SignatureValue>R0moeU+WI0KINkD6eSLrzr3XeKWbYvfxBJ6fPL/kTExDFwHq57JXNeFeqKe+wqPwCY02YbvJAYnE
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
921gV1GecYOgw4pdasHckHZpzoLtrRgXz+bloClWsx16bD6jN4NzJ0qurLak0zvofnU8PrphonCT
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
ems0pSW88CgyYn++DNAcEemi4WNRGSZLCUPaHt7YI1pZXqCtnkJjclI8KsOhVy5E0/29QyCeGKIa
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
H96LabJzb993bXcVAVDlVzkVj8qRFXQa0+dGAdWC4YSLa2Fo5ZsJrW/T65GzdJz6eEqtIep7GoWd
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
4Ex9mn7LD+JU57+ODn+JYjmBNsXcHzgF1stpYA==</SignatureValue>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] <KeyInfo>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] <KeyValue>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] <RSAKeyValue>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
<Modulus>q0/dV5P0n5MJ+bvbpzxik8TQ1hHdXxIG7CYb0/XEuxLNNgu+fdZORwV0Jius7zICTlAPIibxRWeE
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
DtaGxW+xriIwOjLU6KRqmuVL8/vZVD3+WtqVyTQv5QpOEaZUNUb0ffCCXKR4nTWFR6YGYcp1LSY9
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
H4QrldQxN7sWZuY6tfcL8kLdJE+035liu/BD8utW4xHP9OnO3h8cncu3v0fFKw0GPZojDD8ikn7Z
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
ZnO35GR0N6pJmmK1IaJOmyt0gtsTE0K7uTrSqayNyCJsynfTbHejHbcrl/reO1njVjRji3o2FhLk
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
c0XXvz4WWV9arbUy0kvzomhTI3bJGtOYDXA0tw==</Modulus>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
<Exponent>AQAB</Exponent>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] </RSAKeyValue>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] </KeyValue>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] </KeyInfo>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] </Signature>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] </saml2p:AuthnRequest>
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] Has 1 candidate keys
for validation.
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] Validation with key
#0 failed with exception: Unable to validate Signature
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e]
SimpleSAML_Error_Error: UNHANDLEDEXCEPTION
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] Backtrace:
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] 1
/usr/share/simplesamlphp/idp.r3313/www/_include.php:37
(SimpleSAML_exception_handler)
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] 0 [builtin] (N/A)
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] Caused by: Exception:
Unable to validate Signature
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] Backtrace:
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] 6
/usr/share/simplesamlphp/idp.r3313/vendor/simplesamlphp/saml2/src/SAML2/Utils.php:158
(SAML2_Utils::validateSignature)
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] 5 [builtin] (call_user_func)
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] 4
/usr/share/simplesamlphp/idp.r3313/vendor/simplesamlphp/saml2/src/SAML2/Message.php:212
(SAML2_Message::validate)
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] 3
/usr/share/simplesamlphp/idp.r3313/modules/saml/lib/Message.php:195
(sspmod_saml_Message::checkSign)
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] 2
/usr/share/simplesamlphp/idp.r3313/modules/saml/lib/Message.php:252
(sspmod_saml_Message::validateMessage)
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] 1
/usr/share/simplesamlphp/idp.r3313/modules/saml/lib/IdP/SAML2.php:298
(sspmod_saml_IdP_SAML2::receiveAuthnRequest)
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] 0
/usr/share/simplesamlphp/idp.r3313/www/saml2/idp/SSOService.php:19
(N/A)
Jan 06 17:12:04 simplesamlphp ERROR [06e111d47e] Error report with id
12d9dc1f generated.
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e]
/idp/saml2/idp/SSOService.php - Template: Could not find template file
[error.php] at [/usr/share/simplesamlphp/idp.r3313/modules/terena/themes/theme/default/error.php]
- now trying the base template
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] Template: Reading
[/usr/share/simplesamlphp/idp.r3313/dictionaries/errors]
Jan 06 17:12:04 simplesamlphp DEBUG [06e111d47e] Template: Reading
[/usr/share/simplesamlphp/idp.r3313/modules/terena/dictionaries/header]
I guess I'm now out of options....
Olav Morken
Jan 7, 2014, 8:40:53 AM1/7/14
to simple...@googlegroups.com
On Mon, Jan 06, 2014 at 17:20:46 +0100, Dick Visser wrote:
> On 6 January 2014 13:12, Olav Morken <olav....@uninett.no> wrote:
>
> > (If CrashPlan allows you to retrieve the RSA private key, creating a
> > certificate using that should be far more straightforward.)
>
>
> In tried to do that:
>
> 1. Copy the text in "RSA Private Key (base 64 encoded PKCS#8 private
> key)" to a file key.der.base64, then extract the private key:
>
>
> openssl enc -base64 -in key.der.base64 -d | openssl pkcs8 -inform DER -nocrypt
>
>
> Then I generate self-signed certificate with this private key:
>
> openssl req -new -x509 -key private.key -out cert.pem -days 36500
>
>
> Then I stripped the tabs and headers:
>
> openssl base64 -d -in cert.pem | base64 -w 0
>
> I then add the resulting certificate to the metadata:
[...]
> On 6 January 2014 13:12, Olav Morken <olav....@uninett.no> wrote:
>
> > (If CrashPlan allows you to retrieve the RSA private key, creating a
> > certificate using that should be far more straightforward.)
>
>
> In tried to do that:
>
> 1. Copy the text in "RSA Private Key (base 64 encoded PKCS#8 private
> key)" to a file key.der.base64, then extract the private key:
>
>
> openssl enc -base64 -in key.der.base64 -d | openssl pkcs8 -inform DER -nocrypt
>
>
> Then I generate self-signed certificate with this private key:
>
> openssl req -new -x509 -key private.key -out cert.pem -days 36500
>
>
> Then I stripped the tabs and headers:
>
> openssl base64 -d -in cert.pem | base64 -w 0
>
> I then add the resulting certificate to the metadata:
> But now the signature can't be verified:
[...]
> I guess I'm now out of options....
Hi,
I think something has gone wrong in the key conversion process.
According to the message, the modulus of the public key is:
q0/dV5P0n5MJ+bvbpzxik8TQ1hHdXxIG7CYb0/XEuxLNNgu+fdZORwV0Jius7zIC
TlAPIibxRWeEDtaGxW+xriIwOjLU6KRqmuVL8/vZVD3+WtqVyTQv5QpOEaZUNUb0
ffCCXKR4nTWFR6YGYcp1LSY9H4QrldQxN7sWZuY6tfcL8kLdJE+035liu/BD8utW
4xHP9OnO3h8cncu3v0fFKw0GPZojDD8ikn7ZZnO35GR0N6pJmmK1IaJOmyt0gtsT
E0K7uTrSqayNyCJsynfTbHejHbcrl/reO1njVjRji3o2FhLkc0XXvz4WWV9arbUy
0kvzomhTI3bJGtOYDXA0tw==
Which decodes to the following in hex:
00:ab:4f:dd:57:93:f4:9f:93:09:f9:bb:db:a7:3c:
62:93:c4:d0:d6:11:dd:5f:12:06:ec:26:1b:d3:f5:
c4:bb:12:cd:36:0b:be:7d:d6:4e:47:05:74:26:2b:
ac:ef:32:02:4e:50:0f:22:26:f1:45:67:84:0e:d6:
86:c5:6f:b1:ae:22:30:3a:32:d4:e8:a4:6a:9a:e5:
4b:f3:fb:d9:54:3d:fe:5a:da:95:c9:34:2f:e5:0a:
4e:11:a6:54:35:46:f4:7d:f0:82:5c:a4:78:9d:35:
85:47:a6:06:61:ca:75:2d:26:3d:1f:84:2b:95:d4:
31:37:bb:16:66:e6:3a:b5:f7:0b:f2:42:dd:24:4f:
b4:df:99:62:bb:f0:43:f2:eb:56:e3:11:cf:f4:e9:
ce:de:1f:1c:9d:cb:b7:bf:47:c5:2b:0d:06:3d:9a:
23:0c:3f:22:92:7e:d9:66:73:b7:e4:64:74:37:aa:
49:9a:62:b5:21:a2:4e:9b:2b:74:82:db:13:13:42:
bb:b9:3a:d2:a9:ac:8d:c8:22:6c:ca:77:d3:6c:77:
a3:1d:b7:2b:97:fa:de:3b:59:e3:56:34:63:8b:7a:
36:16:12:e4:73:45:d7:bf:3e:16:59:5f:5a:ad:b5:
32:d2:4b:f3:a2:68:53:23:76:c9:1a:d3:98:0d:70:
34:b7
Meanwhile, the certificate created has the following modulus:
00:a3:eb:1c:d1:49:2c:c8:b6:3d:de:f3:e6:34:43:
de:1d:7a:7f:64:da:ae:8c:8f:bb:a3:08:e8:26:ae:
39:cb:3b:15:59:32:c2:b6:15:4a:78:b8:c0:99:b9:
93:d1:eb:5f:0c:19:a3:72:06:2d:6d:74:c8:d0:6d:
0b:a0:7b:e2:ee:84:26:08:a1:7e:02:12:7f:65:73:
39:97:cc:1c:c8:53:96:be:46:93:27:37:3a:88:d2:
dd:13:c6:3f:0b:9e:67:dc:83:8a:be:76:4a:5a:c8:
e7:33:fd:a6:da:28:af:df:9b:f1:e0:10:76:1a:6e:
7b:59:70:35:b8:35:79:0d:8c:02:19:28:8b:d0:1b:
a9:0f:b3:78:f2:0f:b4:27:ca:d5:ac:4f:90:7b:4c:
f8:6b:d8:c5:d6:bf:94:33:71:ca:fc:dd:53:1b:0a:
de:e0:60:0d:8e:a4:61:25:55:92:b9:d5:ea:64:89:
12:ae:6a:28:8c:54:ad:3d:33:2b:21:72:3a:23:89:
41:0b:5f:a7:b3:88:7f:92:ea:06:8c:55:93:2c:14:
c7:85:1d:1f:2d:b2:6e:28:e5:83:14:c9:bc:b5:7b:
90:bd:ab:7c:c0:58:c4:52:b5:a5:a4:16:22:65:3f:
78:49:d9:77:4e:66:4b:27:bb:a9:e6:dd:56:7d:91:
76:57
Which is different.
I therefore wonder if the key was somehow changed during conversion?
I suggest examining the private key after you have converted it
by issuing the following command:
openssl rsa -text -in private.key
Make sure that the modulus in the output matches the one above
(starting with 00:ab). If it doesn't, you somehow have the wrong
private key.
For completenes, here is the public key in PEM format:
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAq0/dV5P0n5MJ+bvbpzxi
k8TQ1hHdXxIG7CYb0/XEuxLNNgu+fdZORwV0Jius7zICTlAPIibxRWeEDtaGxW+x
riIwOjLU6KRqmuVL8/vZVD3+WtqVyTQv5QpOEaZUNUb0ffCCXKR4nTWFR6YGYcp1
LSY9H4QrldQxN7sWZuY6tfcL8kLdJE+035liu/BD8utW4xHP9OnO3h8cncu3v0fF
Kw0GPZojDD8ikn7ZZnO35GR0N6pJmmK1IaJOmyt0gtsTE0K7uTrSqayNyCJsynfT
bHejHbcrl/reO1njVjRji3o2FhLkc0XXvz4WWV9arbUy0kvzomhTI3bJGtOYDXA0
twIDAQAB
-----END PUBLIC KEY-----
The contents of it can be displayed by running something like:
openssl rsa -pubin -text -in public.pem
Dick Visser
Jan 7, 2014, 11:08:02 AM1/7/14
to simplesamlphp
I think there is something weird going on with the CrashPlan keys.
If I press "Change RSA Key Pair", it asks for confirmation, and then a
new RSA key pair is generated. I can see that happening in the web
interface.
However, the <ds:Modulus> in the metadata
(https://crashplan.terena.org:4285/api/SsoAuthSpMetadata) stays
exactly the same.
But that should also change, right?
Dick
> --
> You received this message because you are subscribed to the Google Groups "simpleSAMLphp" group.
> To unsubscribe from this group and stop receiving emails from it, send an email to simplesamlph...@googlegroups.com.
> To post to this group, send email to simple...@googlegroups.com.
> Visit this group at http://groups.google.com/group/simplesamlphp.
> For more options, visit https://groups.google.com/groups/opt_out.
If I press "Change RSA Key Pair", it asks for confirmation, and then a
new RSA key pair is generated. I can see that happening in the web
interface.
However, the <ds:Modulus> in the metadata
(https://crashplan.terena.org:4285/api/SsoAuthSpMetadata) stays
exactly the same.
But that should also change, right?
Dick
> You received this message because you are subscribed to the Google Groups "simpleSAMLphp" group.
> To unsubscribe from this group and stop receiving emails from it, send an email to simplesamlph...@googlegroups.com.
> To post to this group, send email to simple...@googlegroups.com.
> Visit this group at http://groups.google.com/group/simplesamlphp.
> For more options, visit https://groups.google.com/groups/opt_out.
Olav Morken
Jan 8, 2014, 6:23:45 AM1/8/14
to simple...@googlegroups.com
On Tue, Jan 07, 2014 at 17:08:02 +0100, Dick Visser wrote:
> I think there is something weird going on with the CrashPlan keys.
> If I press "Change RSA Key Pair", it asks for confirmation, and then a
> new RSA key pair is generated. I can see that happening in the web
> interface.
>
> However, the <ds:Modulus> in the metadata
> (https://crashplan.terena.org:4285/api/SsoAuthSpMetadata) stays
> exactly the same.
>
> But that should also change, right?
Yes, the modulus is determined by the private key, so it must change
> I think there is something weird going on with the CrashPlan keys.
> If I press "Change RSA Key Pair", it asks for confirmation, and then a
> new RSA key pair is generated. I can see that happening in the web
> interface.
>
> However, the <ds:Modulus> in the metadata
> (https://crashplan.terena.org:4285/api/SsoAuthSpMetadata) stays
> exactly the same.
>
> But that should also change, right?
when the private key changes.
jimn...@jimbowho.com
May 20, 2018, 6:00:42 PM5/20/18
to SimpleSAMLphp
jimn...@jimbowho.com
May 20, 2018, 6:01:14 PM5/20/18
to SimpleSAMLphp
On Monday, January 6, 2014 at 3:00:05 AM UTC-8, Dick Visser wrote:
Reply all
Reply to author
Forward
0 new messages
