Regex negative lookahead in Rule
282 views
Skip to first unread message
Colin Edwards
Nov 30, 2022, 9:04:31 AM11/30/22
to Wazuh mailing list
Hi Everyone,
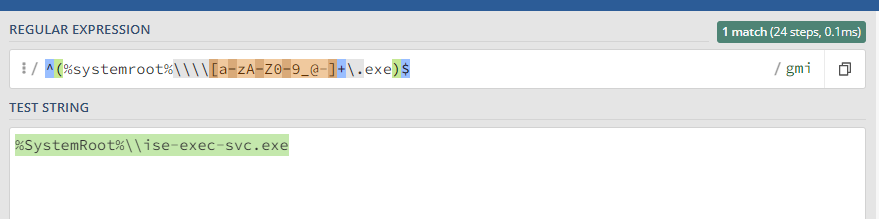
I'm trying to add a negative lookahead to Rule ID 92650 in 0840-win_event_channel.xml to filter out some known-good events, but I'm not having luck getting the rule to not trigger.
The default 92650 rule is...
<rule id="92650" level="12">
<if_sid>61138</if_sid>
<field name="win.eventdata.imagePath">^%systemroot%\\\\\w+\.exe$</field>
<options>no_full_log</options>
<description>New Windows Service Created to start from windows root path. Suspicious event as the binary may have been dropped using Windows Admin Shares.</description>
<mitre>
<id>T1021.002</id>
<id>T1569.002</id>
</mitre>
</rule>
<if_sid>61138</if_sid>
<field name="win.eventdata.imagePath">^%systemroot%\\\\\w+\.exe$</field>
<options>no_full_log</options>
<description>New Windows Service Created to start from windows root path. Suspicious event as the binary may have been dropped using Windows Admin Shares.</description>
<mitre>
<id>T1021.002</id>
<id>T1569.002</id>
</mitre>
</rule>
The environment that I'm monitoring uses a Cisco ISE-PIC integration in its firewall to identify what user is currently logged in on windows endpoints. ISE-PIC drops an exe that matches Rule 92650's pattern. It drops "%SystemRoot%\\ise-exec-svc.exe"
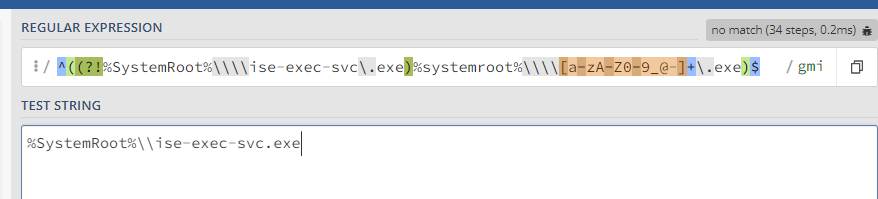
To try to stop the rule from triggering, I've updated the regex to include this Negative Lookahead...
^((?!%SystemRoot%\\\\ise-exec-svc\.exe)%systemroot%\\\\\w+\.exe)$
... but it's still triggering.
So, I guess I have a couple of questions...
1 - Any idea why that regex isn't working the way I expect it to? I did some quick testing using regex101. The "\w+" token there doesn't seem to match Wazuh's regex engine exactly (and the valid characters noted on the Wazuh Documentation for the syntax) so I changed that to "[a-zA-Z0-9_@-]+" and it matched without the negative lookahead and then didn't match with it.


2 - I'm new to Wazuh - is there a better way to accomplish the exclusion/exception that I'm trying to create?
Thanks,
Colin Edwards
CISSP, GDSA, GCIH, GMON, GCWN
Kevin Ledesma
Nov 30, 2022, 9:15:12 AM11/30/22
to Wazuh mailing list
Hello Collin!
Let me do some research and I'll be back to you as soon as possible!
Regards! Kevin
Kevin Ledesma
Dec 1, 2022, 2:23:48 PM12/1/22
to Wazuh mailing list
Hello Colin!
Well, in first place the regex is not working as you are testing on a PCRE2 engine and wazuh uses OS_Regex by default regex engine (check this doc).
To use PCRE2 as regex engine in wazuh, you can specify it to the field tag:
<field name="win.eventdata.imagePath" type="pcre2" negate="yes" >%SystemRoot%\\\\ise-exec-svc\.exe</field>
I tested it with this regex %SystemRoot%\\\\ise-exec-svc\.exe and it worked correctly.
I hope It was helpful! Have a nice day!
Regards! Kevin
Colin Edwards
Dec 5, 2022, 2:33:39 PM12/5/22
to Wazuh mailing list
I'm still not having any luck getting this rule to not trigger.
Below is the excerpt from my current /var/ossec/ruleset/rules/0840-win_event_channel.xml. I've also tried it without using type="pcre2" on the first Field Name line, the same way it is with the default rule file.
Any thoughts? I really want to understand what I'm doing wrong here since I'm just starting to explore using Wazuh, and writing exceptions like this is going to be critical to tuning an environment.
<rule id="92650" level="12">
<if_sid>61138</if_sid>
<field name="win.eventdata.imagePath" type="pcre2">^%systemroot%\\\\\w+\.exe$</field>
<field name="win.eventdata.imagePath" type="pcre2" negate="yes">^%SystemRoot%\\\\ise-exec-svc\.exe$</field>
<options>no_full_log</options>
<description>New Windows Service Created to start from windows root path. Suspicious event as the binary may have been dropped using Windows Admin Shares.</description>
<mitre>
<id>T1021.002</id>
<id>T1569.002</id>
</mitre>
</rule>
Thanks,
Colin
Colin Edwards
Dec 12, 2022, 3:42:32 PM12/12/22
to Wazuh mailing list
Hi Everyone,
<options>no_full_log</options>
<description>New Windows Service Created to start from windows root path. Suspicious event as the binary may have been dropped using Windows Admin Shares.</description>
<mitre>
<id>T1021.002</id>
<id>T1569.002</id>
</mitre>
</rule>
I've also tried to implement the rule with the exception (negate="yes") below in /var/ossec/etc/rules/local_rules.xml, and the rule is still being triggered. I've read through the documentation, and I feel like I have a pretty good understanding of how this is supposed to work. What am I missing here?
<group name="win_evt_channel,">
<!-- Filtering out known-good from Cisco ISE-PIC -->
<rule id="92650" level="12" overwrite="yes">
<if_sid>61138</if_sid>
<field name="win.eventdata.imagePath" type="pcre2">(?i)^%SystemRoot%\\\\\w+\.exe$</field>
<field name="win.eventdata.imagePath" type="pcre2" negate="yes">(?i)^%SystemRoot%\\\\ise-exec-svc\.exe$</field>
<!-- Filtering out known-good from Cisco ISE-PIC -->
<rule id="92650" level="12" overwrite="yes">
<if_sid>61138</if_sid>
<field name="win.eventdata.imagePath" type="pcre2">(?i)^%SystemRoot%\\\\\w+\.exe$</field>
<field name="win.eventdata.imagePath" type="pcre2" negate="yes">(?i)^%SystemRoot%\\\\ise-exec-svc\.exe$</field>
<options>no_full_log</options>
<description>New Windows Service Created to start from windows root path. Suspicious event as the binary may have been dropped using Windows Admin Shares.</description>
<mitre>
<id>T1021.002</id>
<id>T1569.002</id>
</mitre>
</rule>
</group>
Thanks,
Colin Edwards
CISSP, GDSA, GCIH, GMON, GCWN
Julián Morales
Dec 13, 2022, 9:35:06 AM12/13/22
to Wazuh mailing list
Hi Colin,
Sorry for the late response. I think the best option is to create a child rule, not to modify the original rule.
You could have a child rule that when rule 92650 is triggered then it analyzes the condition of the
`win.eventdata.imagePath` field and decides to mute itself. The rule should look like the following:
Sorry for the late response. I think the best option is to create a child rule, not to modify the original rule.
You could have a child rule that when rule 92650 is triggered then it analyzes the condition of the
`win.eventdata.imagePath` field and decides to mute itself. The rule should look like the following:
<group name="win_evt_channel,">
<rule id="100010" level="0">
<if_sid>92650</if_sid>
<field name="win.eventdata.imagePath" type="pcre2" negate="yes">(?i)^%SystemRoot%\\\\ise-exec-svc\.exe$</field>
<description>Silence 92650 - Known false positive.</description>
</rule>
</group>
If after adding this rule, and restarting the manager, for some reason it does not silence the event you want, you could share with me the alert in json format (Extracted from the security events in kibana) and I will test it in my personal environment.
Regards, Julian
If after adding this rule, and restarting the manager, for some reason it does not silence the event you want, you could share with me the alert in json format (Extracted from the security events in kibana) and I will test it in my personal environment.
Regards, Julian
Julián Morales
Dec 13, 2022, 9:40:23 AM12/13/22
to Julián Morales, Wazuh mailing list
My mistake, the negate=yes should not go, so the rule would be:
<group name="win_evt_channel,">
<group name="win_evt_channel,">
<rule id="100010" level="0">
<if_sid>92650</if_sid>
<field name="win.eventdata.imagePath" type="pcre2">(?i)^%SystemRoot%\\\\ise-exec-svc\.exe$</field>
<description>Silence 92650 - Known false positive.</description>
</rule>
</group>
--
You received this message because you are subscribed to the Google Groups "Wazuh mailing list" group.
To unsubscribe from this group and stop receiving emails from it, send an email to wazuh+un...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/wazuh/13fedbf1-b30e-4bae-a8e3-44d164fe0d54n%40googlegroups.com.
Colin Edwards
Dec 14, 2022, 8:04:53 AM12/14/22
to Wazuh mailing list
Hi Julian,
That worked. Thank you!
Colin
Reply all
Reply to author
Forward
0 new messages
