Disable NTLM with Exchange 2016
Mayo, Bill
Due to security recommendations, I started looking into disabling NTLM in our domain. As a first step, turned on NTLM auditing and see that the vast majority of traffic is related to our Exchange 2016 environment. I tried researching how to disable NTLM for Exchange, but haven’t gotten a clear picture. I see where there is a Microsoft article for how to do this with Exchange 2019 (Disabling Legacy Authentication in Exchange Server 2019 - Microsoft Tech Community), but I am not seeing the same for 2016, which suggests maybe it is not possible. But I did find info on getting Exchange 2016 to use Kerberos for CAS, which maybe suggests there is a way (Configure Kerberos authentication for load-balanced Client Access services | Microsoft Docs).
I hope I am just not hitting the correct search phrase to get a definitive answer. Can anybody point me to any guidance on: 1) is it currently possible to disable NTLM when using Exchange 2016, and 2) if so, is there anything needed other than what is documented in the 2nd link above?
Thanks for any help,
Bill Mayo
Michael B. Smith
I don’t think you can completely remove NTLM from Exchange (more than single-server Exchange). Clusters use both Kerberos and NTLM until Server 2019. Certain things like cross-server move-mailbox also use NTLM.
You can reduce it, and certainly use “modern” NTLM, but not remove it.
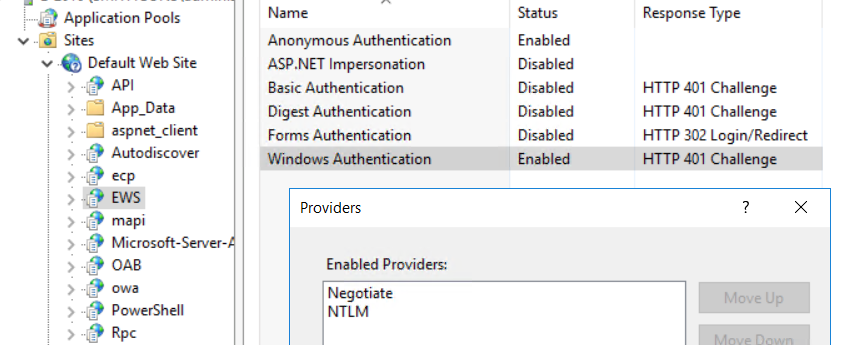
And yes, you need to remove the NTLM provider as an option in each IIS vDir that accepts IWA.
--
You received this message because you are subscribed to the Google Groups "ntexchange" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
ntexchange+...@googlegroups.com.
To view this discussion on the web visit
https://groups.google.com/d/msgid/ntexchange/38ab468f1fa54dfdb1b6ad6562b2a8ba%40pittcountync.gov.
Mayo, Bill
Thanks for the info. I took at look at IIS and see that most applications were set to allow Anonymous and Windows authentications (like in your screenshot). There were some, like OAB, that only allowed Windows Authentication. It seems like removing that would break OAB. Is there any way to know from which applications it is “safe” to remove authentication? And would it be necessary to follow the Microsoft article about enabling Kerberos for load-balanced CAS—I assume yes. I do suppose it is possible the extremely talented fellow that helped set us up might have done that; it wasn’t immediately obvious to me how to confirm/deny that may already be in place and I haven’t had time to sit down and try to figure it out.
To view this discussion on the web visit https://groups.google.com/d/msgid/ntexchange/074c01603b4847ed80cec64fc6ef4d50%40smithcons.com.
Mayo, Bill
Sorry, just realized that I missed an important aspect of what you show below in regards to the provider. Makes more sense now. That said, is there any specific thing that is likely to break if you remove NTLM under providers?
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Mayo, Bill
Sent: Wednesday, October 27, 2021 4:56 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] RE: Disable NTLM with Exchange 2016
Thanks for the info. I took at look at IIS and see that most applications were set to allow Anonymous and Windows authentications (like in your screenshot). There were some, like OAB, that only allowed Windows Authentication. It seems like removing that would break OAB. Is there any way to know from which applications it is “safe” to remove authentication? And would it be necessary to follow the Microsoft article about enabling Kerberos for load-balanced CAS—I assume yes. I do suppose it is possible the extremely talented fellow that helped set us up might have done that; it wasn’t immediately obvious to me how to confirm/deny that may already be in place and I haven’t had time to sit down and try to figure it out.
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Michael B. Smith
Sent: Wednesday, October 27, 2021 4:46 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] RE: Disable NTLM with Exchange 2016
I don’t think you can completely remove NTLM from Exchange (more than single-server Exchange). Clusters use both Kerberos and NTLM until Server 2019. Certain things like cross-server move-mailbox also use NTLM.
You can reduce it, and certainly use “modern” NTLM, but not remove it.
And yes, you need to remove the NTLM provider as an option in each IIS vDir that accepts IWA.
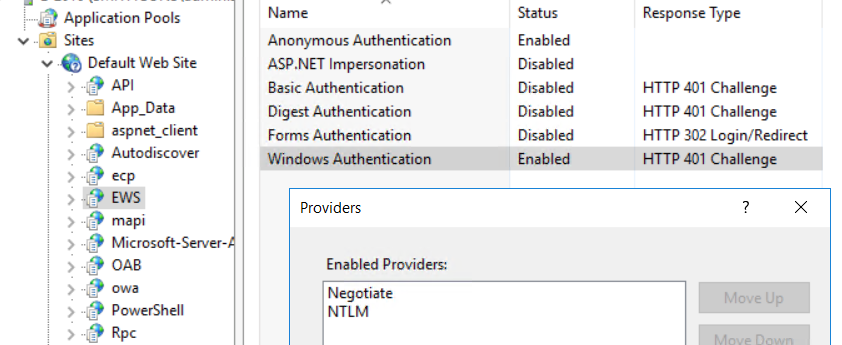
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Mayo, Bill
Sent: Wednesday, October 27, 2021 4:13 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] Disable NTLM with Exchange 2016
Due to security recommendations, I started looking into disabling NTLM in our domain. As a first step, turned on NTLM auditing and see that the vast majority of traffic is related to our Exchange 2016 environment. I tried researching how to disable NTLM for Exchange, but haven’t gotten a clear picture. I see where there is a Microsoft article for how to do this with Exchange 2019 (Disabling Legacy Authentication in Exchange Server 2019 - Microsoft Tech Community), but I am not seeing the same for 2016, which suggests maybe it is not possible. But I did find info on getting Exchange 2016 to use Kerberos for CAS, which maybe suggests there is a way (Configure Kerberos authentication for load-balanced Client Access services | Microsoft Docs).
I hope I am just not hitting the correct search phrase to get a definitive answer. Can anybody point me to any guidance on: 1) is it currently possible to disable NTLM when using Exchange 2016, and 2) if so, is there anything needed other than what is documented in the 2nd link above?
Thanks for any help,
Bill Mayo
--
You received this message because you are subscribed to the Google Groups "ntexchange" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
ntexchange+...@googlegroups.com.
To view this discussion on the web visit
https://groups.google.com/d/msgid/ntexchange/38ab468f1fa54dfdb1b6ad6562b2a8ba%40pittcountync.gov.
--
You received this message because you are subscribed to the Google Groups "ntexchange" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
ntexchange+...@googlegroups.com.
To view this discussion on the web visit
https://groups.google.com/d/msgid/ntexchange/074c01603b4847ed80cec64fc6ef4d50%40smithcons.com.
--
You received this message because you are subscribed to the Google Groups "ntexchange" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
ntexchange+...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/ntexchange/07694ab27ede4a0c83270029a6135c2c%40pittcountync.gov.
Michael B. Smith
Note: I did not say “remove authentication”, I said “remove the NTLM provider”. That means “Negotiate” is still there, which supports Kerberos.
I’ve done this at a couple places recently for internal apps.
The fellow who did your setup didn’t enable Kerberos for load-balanced CAS. You can verify if it’s been done by running “Get-ClientAccessService -IncludeAlternateServiceAccountCredentialStatus| fl *” in EMS. The field “AlternateServiceAccountConfiguration” will have a computer account specified (and that account will be assigned a variety of SPNs) if the configuration has been done.
To view this discussion on the web visit https://groups.google.com/d/msgid/ntexchange/07694ab27ede4a0c83270029a6135c2c%40pittcountync.gov.
Michael B. Smith
I haven’t seen anything.
If you use DirectAccess, you might want to test carefully. I have some vague memory that it wants NTLM.
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Mayo, Bill
Sent: Wednesday, October 27, 2021 5:03 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] RE: Disable NTLM with Exchange 2016
Sorry, just realized that I missed an important aspect of what you show below in regards to the provider. Makes more sense now. That said, is there any specific thing that is likely to break if you remove NTLM under providers?
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Mayo, Bill
Sent: Wednesday, October 27, 2021 4:56 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] RE: Disable NTLM with Exchange 2016
Thanks for the info. I took at look at IIS and see that most applications were set to allow Anonymous and Windows authentications (like in your screenshot). There were some, like OAB, that only allowed Windows Authentication. It seems like removing that would break OAB. Is there any way to know from which applications it is “safe” to remove authentication? And would it be necessary to follow the Microsoft article about enabling Kerberos for load-balanced CAS—I assume yes. I do suppose it is possible the extremely talented fellow that helped set us up might have done that; it wasn’t immediately obvious to me how to confirm/deny that may already be in place and I haven’t had time to sit down and try to figure it out.
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Michael B. Smith
Sent: Wednesday, October 27, 2021 4:46 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] RE: Disable NTLM with Exchange 2016
I don’t think you can completely remove NTLM from Exchange (more than single-server Exchange). Clusters use both Kerberos and NTLM until Server 2019. Certain things like cross-server move-mailbox also use NTLM.
You can reduce it, and certainly use “modern” NTLM, but not remove it.
And yes, you need to remove the NTLM provider as an option in each IIS vDir that accepts IWA.
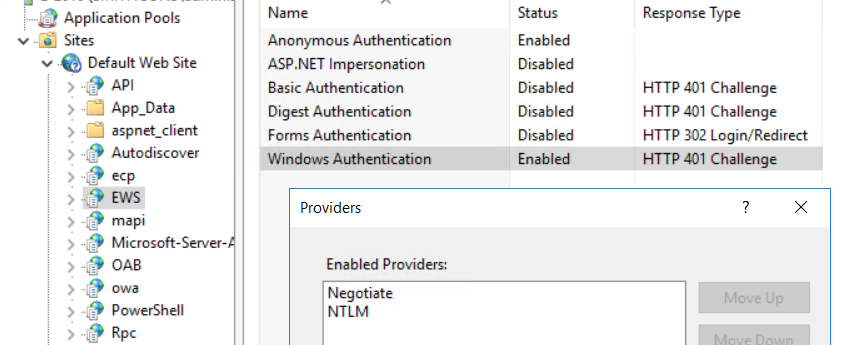
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Mayo, Bill
Sent: Wednesday, October 27, 2021 4:13 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] Disable NTLM with Exchange 2016
Due to security recommendations, I started looking into disabling NTLM in our domain. As a first step, turned on NTLM auditing and see that the vast majority of traffic is related to our Exchange 2016 environment. I tried researching how to disable NTLM for Exchange, but haven’t gotten a clear picture. I see where there is a Microsoft article for how to do this with Exchange 2019 (Disabling Legacy Authentication in Exchange Server 2019 - Microsoft Tech Community), but I am not seeing the same for 2016, which suggests maybe it is not possible. But I did find info on getting Exchange 2016 to use Kerberos for CAS, which maybe suggests there is a way (Configure Kerberos authentication for load-balanced Client Access services | Microsoft Docs).
I hope I am just not hitting the correct search phrase to get a definitive answer. Can anybody point me to any guidance on: 1) is it currently possible to disable NTLM when using Exchange 2016, and 2) if so, is there anything needed other than what is documented in the 2nd link above?
Thanks for any help,
Bill Mayo
--
You received this message because you are subscribed to the Google Groups "ntexchange" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
ntexchange+...@googlegroups.com.
To view this discussion on the web visit
https://groups.google.com/d/msgid/ntexchange/38ab468f1fa54dfdb1b6ad6562b2a8ba%40pittcountync.gov.
--
You received this message because you are subscribed to the Google Groups "ntexchange" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
ntexchange+...@googlegroups.com.
To view this discussion on the web visit
https://groups.google.com/d/msgid/ntexchange/074c01603b4847ed80cec64fc6ef4d50%40smithcons.com.
--
You received this message because you are subscribed to the Google Groups "ntexchange" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
ntexchange+...@googlegroups.com.
To view this discussion on the web visit
https://groups.google.com/d/msgid/ntexchange/07694ab27ede4a0c83270029a6135c2c%40pittcountync.gov.
--
You received this message because you are subscribed to the Google Groups "ntexchange" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
ntexchange+...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/ntexchange/5b62c325b453459abd119107fad6d7b1%40pittcountync.gov.
Mayo, Bill
The alternate service account configuration has you create a computer account for this authentication. There is also a computer account associated with the DAG. Am I correct in believing this should be 2 different computer accounts and that you should not use the DAG computer account for this purpose?
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Michael B. Smith
Sent: Wednesday, October 27, 2021 5:12 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] RE: Disable NTLM with Exchange 2016
Note: I did not say “remove authentication”, I said “remove the NTLM provider”. That means “Negotiate” is still there, which supports Kerberos.
I’ve done this at a couple places recently for internal apps.
The fellow who did your setup didn’t enable Kerberos for load-balanced CAS. You can verify if it’s been done by running “Get-ClientAccessService -IncludeAlternateServiceAccountCredentialStatus| fl *” in EMS. The field “AlternateServiceAccountConfiguration” will have a computer account specified (and that account will be assigned a variety of SPNs) if the configuration has been done.
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Mayo, Bill
Sent: Wednesday, October 27, 2021 4:56 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] RE: Disable NTLM with Exchange 2016
Thanks for the info. I took at look at IIS and see that most applications were set to allow Anonymous and Windows authentications (like in your screenshot). There were some, like OAB, that only allowed Windows Authentication. It seems like removing that would break OAB. Is there any way to know from which applications it is “safe” to remove authentication? And would it be necessary to follow the Microsoft article about enabling Kerberos for load-balanced CAS—I assume yes. I do suppose it is possible the extremely talented fellow that helped set us up might have done that; it wasn’t immediately obvious to me how to confirm/deny that may already be in place and I haven’t had time to sit down and try to figure it out.
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Michael B. Smith
Sent: Wednesday, October 27, 2021 4:46 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] RE: Disable NTLM with Exchange 2016
I don’t think you can completely remove NTLM from Exchange (more than single-server Exchange). Clusters use both Kerberos and NTLM until Server 2019. Certain things like cross-server move-mailbox also use NTLM.
You can reduce it, and certainly use “modern” NTLM, but not remove it.
And yes, you need to remove the NTLM provider as an option in each IIS vDir that accepts IWA.

From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Mayo, Bill
Sent: Wednesday, October 27, 2021 4:13 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] Disable NTLM with Exchange 2016
Due to security recommendations, I started looking into disabling NTLM in our domain. As a first step, turned on NTLM auditing and see that the vast majority of traffic is related to our Exchange 2016 environment. I tried researching how to disable NTLM for Exchange, but haven’t gotten a clear picture. I see where there is a Microsoft article for how to do this with Exchange 2019 (Disabling Legacy Authentication in Exchange Server 2019 - Microsoft Tech Community), but I am not seeing the same for 2016, which suggests maybe it is not possible. But I did find info on getting Exchange 2016 to use Kerberos for CAS, which maybe suggests there is a way (Configure Kerberos authentication for load-balanced Client Access services | Microsoft Docs).
I hope I am just not hitting the correct search phrase to get a definitive answer. Can anybody point me to any guidance on: 1) is it currently possible to disable NTLM when using Exchange 2016, and 2) if so, is there anything needed other than what is documented in the 2nd link above?
Thanks for any help,
Bill Mayo
--
You received this message because you are subscribed to the Google Groups "ntexchange" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
ntexchange+...@googlegroups.com.
To view this discussion on the web visit
https://groups.google.com/d/msgid/ntexchange/38ab468f1fa54dfdb1b6ad6562b2a8ba%40pittcountync.gov.
--
You received this message because you are subscribed to the Google Groups "ntexchange" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
ntexchange+...@googlegroups.com.
To view this discussion on the web visit
https://groups.google.com/d/msgid/ntexchange/074c01603b4847ed80cec64fc6ef4d50%40smithcons.com.
--
You received this message because you are subscribed to the Google Groups "ntexchange" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
ntexchange+...@googlegroups.com.
To view this discussion on the web visit
https://groups.google.com/d/msgid/ntexchange/07694ab27ede4a0c83270029a6135c2c%40pittcountync.gov.
--
You received this message because you are subscribed to the Google Groups "ntexchange" group.
To unsubscribe from this group and stop receiving emails from it, send an email to
ntexchange+...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/ntexchange/4b15066ded174b34a6a82d30646307fd%40smithcons.com.
Michael B. Smith
That’s correct, they should be two different computer accounts.
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Mayo, Bill
Sent: Thursday, October 28, 2021 9:05 AM
To: ntexc...@googlegroups.com
Subject: [ntexchange] RE: Disable NTLM with Exchange 2016
The alternate service account configuration has you create a computer account for this authentication. There is also a computer account associated with the DAG. Am I correct in believing this should be 2 different computer accounts and that you should not use the DAG computer account for this purpose?
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Michael B. Smith
Sent: Wednesday, October 27, 2021 5:12 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] RE: Disable NTLM with Exchange 2016
Note: I did not say “remove authentication”, I said “remove the NTLM provider”. That means “Negotiate” is still there, which supports Kerberos.
I’ve done this at a couple places recently for internal apps.
The fellow who did your setup didn’t enable Kerberos for load-balanced CAS. You can verify if it’s been done by running “Get-ClientAccessService -IncludeAlternateServiceAccountCredentialStatus| fl *” in EMS. The field “AlternateServiceAccountConfiguration” will have a computer account specified (and that account will be assigned a variety of SPNs) if the configuration has been done.
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Mayo, Bill
Sent: Wednesday, October 27, 2021 4:56 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] RE: Disable NTLM with Exchange 2016
Thanks for the info. I took at look at IIS and see that most applications were set to allow Anonymous and Windows authentications (like in your screenshot). There were some, like OAB, that only allowed Windows Authentication. It seems like removing that would break OAB. Is there any way to know from which applications it is “safe” to remove authentication? And would it be necessary to follow the Microsoft article about enabling Kerberos for load-balanced CAS—I assume yes. I do suppose it is possible the extremely talented fellow that helped set us up might have done that; it wasn’t immediately obvious to me how to confirm/deny that may already be in place and I haven’t had time to sit down and try to figure it out.
From: ntexc...@googlegroups.com <ntexc...@googlegroups.com>
On Behalf Of Michael B. Smith
Sent: Wednesday, October 27, 2021 4:46 PM
To: ntexc...@googlegroups.com
Subject: [ntexchange] RE: Disable NTLM with Exchange 2016
I don’t think you can completely remove NTLM from Exchange (more than single-server Exchange). Clusters use both Kerberos and NTLM until Server 2019. Certain things like cross-server move-mailbox also use NTLM.
You can reduce it, and certainly use “modern” NTLM, but not remove it.
And yes, you need to remove the NTLM provider as an option in each IIS vDir that accepts IWA.
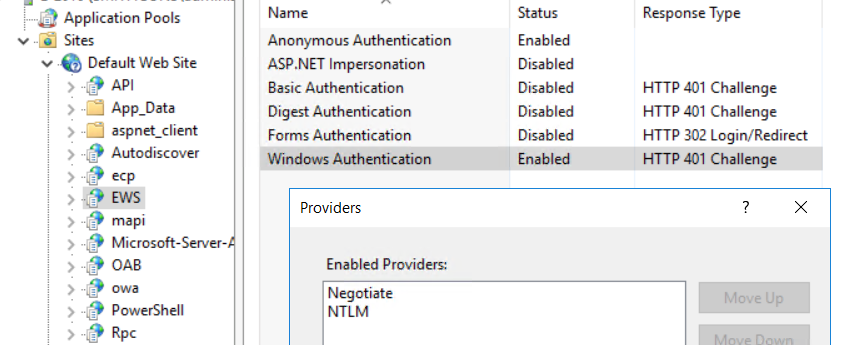
To view this discussion on the web visit https://groups.google.com/d/msgid/ntexchange/9d09ad57985644cdbbec009557aaa541%40pittcountync.gov.
Mayo, Bill
Thanks for all the helpful information. To summarize, it seems that the general process should be:
- Create the alternate service account.
- Configure Exchange to use the alternate service account.
- At this point, if “Negotiate” is at the top of the list on relevant IIS applications, Kerberos should be being used and NTLM auditing should reflect that.
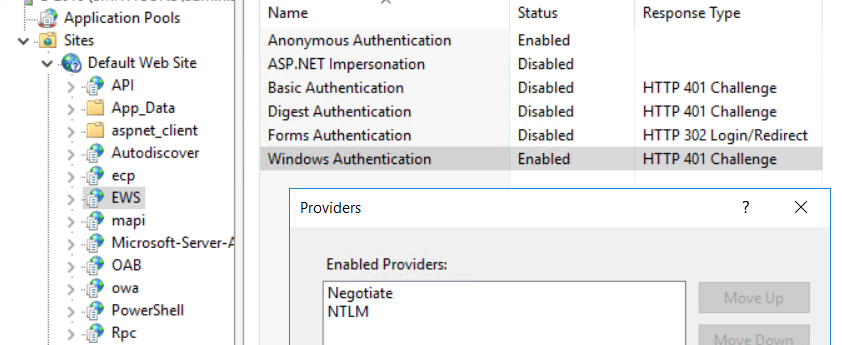
- To turn off NTLM, go into respective IIS applications and remove NTLM from “Enabled Providers” on the “Windows Authentication” authentication type.
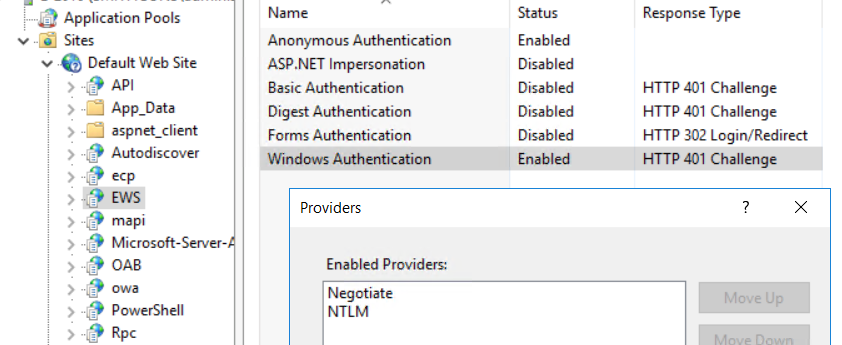
To view this discussion on the web visit https://groups.google.com/d/msgid/ntexchange/f82066f181f842c4b8e1f47891501e71%40smithcons.com.
Michael B. Smith
In re: [3] – I honestly don’t know for certain how that order is selected, and I wouldn’t be surprised if it depends on browser version and OS version.
If kernel-mode is selected, I know that Kerberos is preferred by the server.
In general, when a browser tries to access a resource that requires authentication, it gets returned an error by IIS (a 401) and that error includes a header which says the enabled providers: “WWW-Authenticate: Negotiate” and/or “WWW-Authenticate: NTLM”. Then the browser gets to choose.
Here are a couple of articles, but they aren’t definitive as to ordering:
https://docs.microsoft.com/en-us/troubleshoot/iis/troubleshoot-kerberos-failures-ie
Of particular interesting note – the second article says that by default, Kerberos isn’t supported if you are accessing a site on localhost.

To view this discussion on the web visit https://groups.google.com/d/msgid/ntexchange/26dc666382cb4d9790aae4488f9e1782%40pittcountync.gov.
Mayo, Bill
That is great information. I feel like I have a much better understanding at this point and have a direction. As always, thanks so much for your help!
To view this discussion on the web visit https://groups.google.com/d/msgid/ntexchange/5d4b5596f0d64b3081ed7c962a035619%40smithcons.com.
