My upcoming talk
7 views
Skip to first unread message
Alan Karp
Jan 11, 2023, 7:58:42 PM1/11/23
to <friam@googlegroups.com>
I'll be giving a talk on SitePassword next week at an ACM Meetup,
I mentioned giving a dry run at this week's friam, but it's a 50 minute talk. What's the likelihood of getting through that in just 2 hours?
When I was at HP, I got in the habit of providing extensive speaker notes in case someone else had to present my slides, which proved valuable on more than one occasion. So, instead of presenting at friam, maybe you folks can give me comments from the slides. They're at https://github.com/alanhkarp/SitePassword. There's both Keynote and a PDF, but the latter doesn't have the speaker notes.
Don't bother wordsmithing the speaker notes. They're only an approximation of what I'll actually say when I give the talk.
--------------
Alan Karp
--------------
Alan Karp
Rob Meijer
Jan 12, 2023, 3:36:09 AM1/12/23
to fr...@googlegroups.com
I see a lot of overlap with my ZeroVault efforts a number of years ago.
Dan did a pretty thorough refactoring (almost a rewrite) of the initial code for that;
Not sure if the algorithms are up to date with the code, think the HMAC part is BLAKE2 ass well, but I'm not sure, its been a while, and the proposed username part is missing from the image, but this image gives a general idea of how ZeroVault uses two passphrases to generate password keys (that are then used to generate the actual passwords).
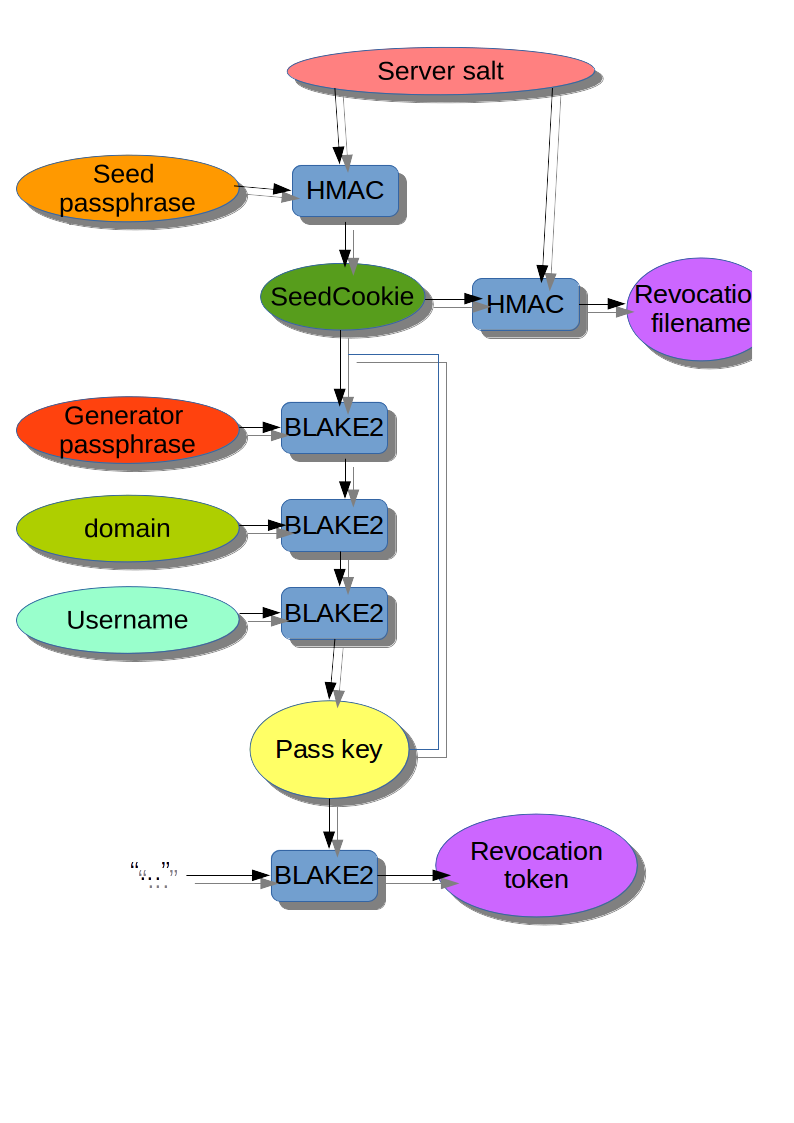
Basically you install a little CGI on your own server and set a server salt in the code. The server has really only two tasks, the rest of the functionality is purely local:
* Generate a SeedCookie if non is set from a seed passphrase.
* Maintain a revocation list for every known SeedCookie.
Basically the first time you use a browser with ZeroVault you must enter your Seed passphrase to bind to your Seed cookie.
Now assuming you have a seed cookie, you fetch the revocation list from the server using that cookie and you are set to go locally.
The idea is that you use a generator password per class of websites. for example:
1) misc
2) social media
3) webshops
4) government
5) work related
6) financial
Then instead of having to remember 50 passwords or reuse a few, you just have to remember these six. Now you give the generator password for the class of sites and the domain name of the site, with optionally a username, and ZeroVault will generate a Pass key for you using the seed cookie. It then will generate a revocation token from the pass key and will check if that token is in the revocation list. If it is, it will use the old pass key instead of the seed cookie and will generate an alternative pass key. This process is repeated until a revocation token is found that isn't in the revocation list.
Now if the user wants a new password for a site, she sends the revocation token to the server for addition to the revocation list, and all is fine.
I think there is some added security in using generated user names when possible. The ZeroVault implementation for that is rudimentary and could likely be improved upon, but I think it is very useful.
The way ZeroVault maps a key to a password (or proposed user name) is by using a maintained mapping config like this one:
In this sample the default key to username mapping for example generates 14 character usernames using characters from three "alphabets":
0: "bcdfghjklmnpqrstvwxz"
1: "aeiouy"
2: "0123456789"
With a structure defined by "01001010010222"
So a generated username could look like:
* fisfuzehrom946
* soqkatypwih558
Mapping to passwords works in the same way.
Hope this, I think conceptually quite similar, tool might bring some ideas for possible improvements to your project.
--
You received this message because you are subscribed to the Google Groups "friam" group.
To unsubscribe from this group and stop receiving emails from it, send an email to friam+un...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/friam/CANpA1Z3B8DCYJr%2BsGcC77mHWnipneY5_1s%3Dp0PxPfhJRZuuKJw%40mail.gmail.com.
Rob Meijer
Jan 12, 2023, 5:08:58 AM1/12/23
to fr...@googlegroups.com
The old posts on ZeroVault from 2016 : https://groups.google.com/g/cap-talk/search?q=zerovault
Rob Meijer
Jan 12, 2023, 5:21:13 AM1/12/23
to fr...@googlegroups.com
Dan's slides might be interesting as well : https://docs.google.com/presentation/d/1BicopAOLy1OTdzYCnTwPurTl7BjRTxCn8uucTAKPw9g/edit#slide=id.g3a76a8d21_12
Alan Karp
Jan 12, 2023, 1:10:57 PM1/12/23
to fr...@googlegroups.com
Thanks for the reminder. I had completely forgotten about this work.
There are other password calculators out there, e.g., https://www.lesspass.com. It looks to me that ZeroVault is based on a more complete threat model than any of the others I've seen. For example, the main mitigation against an offline attack against SitePassword's master password is its strength. ZeroVault has more extensive protection, if I understand correctly.
SitePassword includes some of ZeroVault's features. For example, you can use a different master password for each of the classes of sites. There's also no reason you couldn't use SitePassword to generate a userid, but it would involve an extra step since that feature never occurred to me. The biggest difference is that usability is the main motivating factor for SitePassword. I want my sister to be able to use it without reading any instructions.
--------------
Alan Karp
--------------
Alan Karp
To view this discussion on the web visit https://groups.google.com/d/msgid/friam/CAMpet1XQa%2BckdHrh5BwoecohhaCgsZSAuWrZuKjDZaY4Wrgdwg%40mail.gmail.com.
Raoul Duke
Jan 12, 2023, 1:53:03 PM1/12/23
to fr...@googlegroups.com
> I want [anybody] to be able to use it without reading any instructions.
excellent, yes please, cant wait. security and usability tend not to go together very well in the real world to date. i've been forced to use LastPass at work on mac, linux, and windows (all via chrome) and it has so much big and small ui ux friction imhumbleo.
Alan Karp
Jan 12, 2023, 2:23:45 PM1/12/23
to fr...@googlegroups.com
I'd appreciate your feedback. You can install it from https://chrome.google.com/webstore/detail/site-password/gmnnecpmpifmmjajmigodffkchhehfdl.
I blundered in that this version doesn't do the phishing check. Version 1.0.1 that fixes that will appear shortly. Everything else appears to be working.
--------------
Alan Karp
--------------
Alan Karp
On Thu, Jan 12, 2023 at 10:53 AM Raoul Duke <rao...@gmail.com> wrote:
> I want [anybody] to be able to use it without reading any instructions.excellent, yes please, cant wait. security and usability tend not to go together very well in the real world to date. i've been forced to use LastPass at work on mac, linux, and windows (all via chrome) and it has so much big and small ui ux friction imhumbleo.
--
You received this message because you are subscribed to the Google Groups "friam" group.
To unsubscribe from this group and stop receiving emails from it, send an email to friam+un...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/friam/CAJ7XQb7T1aCkGFdP4LSQxcjOYVJC3YEr67W0chMm46ir25iKTw%40mail.gmail.com.
Bill Frantz
Jan 12, 2023, 10:52:48 PM1/12/23
to Design
Slide 8: Has the text “Slide Subtitle near the top.
Slide 19: Firefox mispelled.
Slide 23: Has the text “Slide Subtitle near the top.
Slide 43:Has the text “Slide Subtitle near the top.
Slide 44: Has the text “Slide Subtitle near the top.
Slide 46: Has the text “Slide Subtitle near the top.
Slide 48: Has the text “Slide Subtitle near the top.
Slide 50: Has the text “Slide Subtitle near the top.
Slide 51: Has the text “Slide Subtitle near the top.
Slide 57: Has the text “Slide Subtitle near the top.
Slide 61: Has the text “Slide Subtitle near the top.
Slide 63: Has the text “Slide Subtitle near the top.
Slides 71 & 72 are the same
Cheers - Bill
--
You received this message because you are subscribed to the Google Groups "friam" group.
To unsubscribe from this group and stop receiving emails from it, send an email to friam+un...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/friam/CANpA1Z3B8DCYJr%2BsGcC77mHWnipneY5_1s%3Dp0PxPfhJRZuuKJw%40mail.gmail.com.
Alan Karp
Jan 12, 2023, 11:06:58 PM1/12/23
to fr...@googlegroups.com
"Slide subtitle" doesn't show up in presentation mode.
Nice catch on the typo.
--------------
Alan Karp
--------------
Alan Karp
To view this discussion on the web visit https://groups.google.com/d/msgid/friam/9EBE92D4-4CF3-4084-95BB-34234D95E7A1%40gmail.com.
Reply all
Reply to author
Forward
0 new messages
