Log monitor stopped, and Upcoming Changes
Rob Stradling
Chris Hills
Shubham Agarwal
Rob Stradling
Chris Hills
Rob Stradling
Rob Stradling
Status update:
Although there's still more work for me to do to restore all of the crt.sh functionality that you all know and love(*), we have today made the new crt.sh front-end webservers publicly available. If you want to reach these new webservers instead of the old ones, for now please add the following entry to your "hosts" file:91.199.212.73 crt.sh
There's no port 5432 access yet, but this will follow soon.
The ct_monitor application has been running since Friday last week, but the backlog has grown slightly rather than gone down. I'm working on profiling the code to figure out what's slow and what can be optimized.
Nathan Goshen
Rob Stradling
Matt Lewis
Rob Stradling
Hi Rob,It seems the backlog is continuing to grow- is there any relative timeline to when the backlog should start reduce/crt.sh fully chew through it?
Additionally, do you have an average trailing wait time for crt.sh? (ie. is it currently 7 days delayed, 14 days, etc.)?
│ url │ latest_entry_timestamp │ backlog │
├───────────────────────────────────────────┼─────────────────────────┼──────────┤
│ https://oak.ct.letsencrypt.org/2020 │ 2019-12-09 15:45:10.122 │ 44508992 │
│ https://ct.googleapis.com/logs/xenon2020 │ 2019-12-10 04:01:22.657 │ 41579326 │
│ https://ct.googleapis.com/logs/argon2020 │ 2019-12-07 22:47:45.258 │ 39656366 │
│ https://ct.googleapis.com/rocketeer │ 2019-12-23 23:45:39.264 │ 3777285 │
│ https://ct.googleapis.com/pilot │ 2019-12-24 21:54:33.989 │ 3089800 │
│ https://ct.cloudflare.com/logs/nimbus2020 │ 2019-12-26 08:20:13.105 │ 1409520 │
└───────────────────────────────────────────┴─────────────────────────┴──────────┘
Rob Stradling
Rob Stradling
I've just added a "Latest Entry Age" column to https://crt.sh/monitored-logs
Matt Lewis
Nummer378
value "<cert id>" is out of range for type integer
SQL statement "SELECT replace(encode(c.CERTIFICATE, 'base64'), chr(10), '') FROM certificate c WHERE c.ID = cert_identifier::integer" PL/pgSQL function download_cert(text) line 12 at SQL statement PL/pgSQL function web_apis(text,text[],text[]) line 177 at RETURN
Rob Stradling
Rob Stradling
I don't yet have ETAs for when we'll be ready to flip the A/AAAA records for crt.sh to point to the new servers, or for when we will then decommission the old servers.
crt.sh has address 91.199.212.73
crt.sh has IPv6 address 2a0e:ac00:c7:d449::5bc7:d449
crt.sh has address 91.199.212.48
crt.sh has IPv6 address 2a0e:ac00:c7:d430::5bc7:d430
Chris Hills
Tom Lancaster
Rob Stradling
Tom Lancaster
--
You received this message because you are subscribed to the Google Groups "crt.sh" group.
To unsubscribe from this group and stop receiving emails from it, send an email to crtsh+un...@googlegroups.com.
To view this discussion on the web, visit https://groups.google.com/d/msgid/crtsh/46fb3e9b-c98e-4042-a5e5-9a3fd36ef56b%40googlegroups.com.
Rob Stradling
To unsubscribe from this group and stop receiving emails from it, send an email to crtsh+unsubscribe@googlegroups.com.
Steven
- Stopping lexeme creation at Public Suffix +1
- Adding a Public Suffix +1 index, falling back to the Public Suffix, and then to any non-standard TLD.
- Adding indexing by decoded IDN names
- Or only using the Public Suffix:
To unsubscribe from this group and stop receiving emails from it, send an email to cr...@googlegroups.com.
Jacob Hoffman-Andrews
> Thinking aloud...
>
> 1. Would it make sense to treat each domain component as a separate
> lexeme? e.g.,
> "www"
> "example"
> "com"
> "evil"
> This would shrink the size of the Full Text Search index and would
> enable the prefix searching use case, but it would also increase the
> number of false positives returned by the index that would then need
> to be filtered out. Would that hurt performance too much?
and "com", that you wouldn't index at all because they are too common.
Even though without knowing the details of Postgres' implementation, it
seems like intersecting the set of results for "www" and "com" would be
prohibitively expensive. So in the example of
"www.example.com.evil.com", with the existing strategy plus the new new,
plus stopwording, you'd have:
"www.example.com.evil.com"
"example.com.evil.com"
"com.evil.com"
"evil.com"
"example"
"evil"
Donncha Fahy
SELECT DISTINCT lexemeFROM certificate, unnest(identities(certificate))WHERE identities(certificate) @@ 'wikipedia.org:*' and lexeme like '%wikipedia.org%';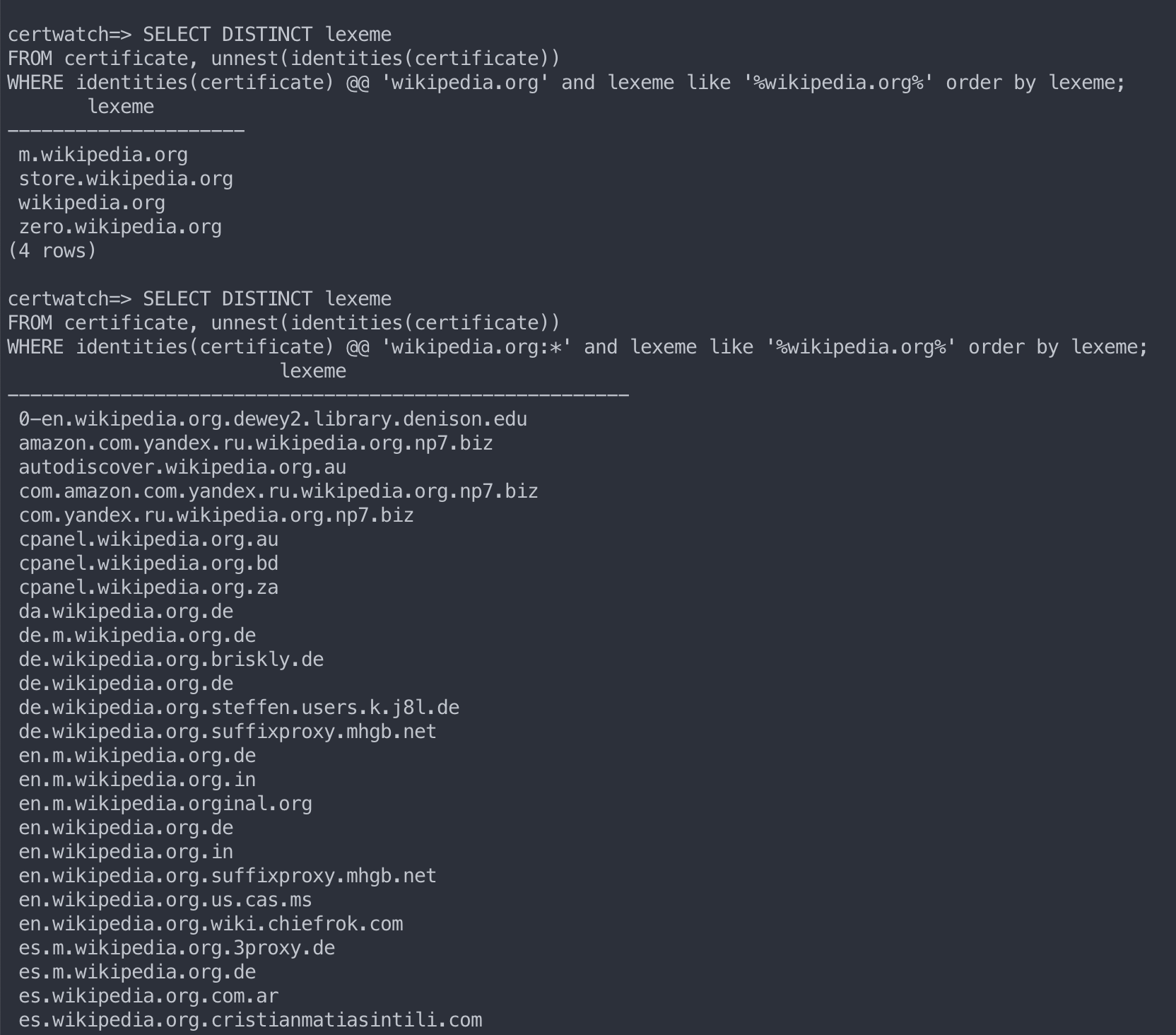
Rob Stradling
Rob Stradling
Tom Lancaster
--
You received this message because you are subscribed to the Google Groups "crt.sh" group.
To unsubscribe from this group and stop receiving emails from it, send an email to crtsh+un...@googlegroups.com.
To view this discussion on the web, visit https://groups.google.com/d/msgid/crtsh/532ce964-c1a4-4185-8826-384f45e223d3%40googlegroups.com.
Steven
For example, for a query on 'www.bad%oogle.com', I believe this works:
WHERE to_tsquery('www.bad:*') @@ identities(cai.CERTIFICATE)
AND to_tsquery('oogle.com') @@ identities(cai.CERTIFICATE)
AND cai.NAME_VALUE ILIKE ('www.bad%oogle.com')
And for 'bad.subdomain.%.%'
WHERE to_tsquery('bad.subdomain:*') @@ identities(cai.CERTIFICATE)
AND cai.NAME_VALUE ILIKE ('bad.subdomain.%.%')
Steven
For example, for a query on '%adgoogl%', I don't believe this will work:
WHERE to_tsquery('adgoogl:*') @@ identities(cai.CERTIFICATE)
AND cai.NAME_VALUE ILIKE ('%adgoogl%')
And it doesn't work for partial domain names:
WHERE to_tsquery('vil.com') @@ identities(cai.CERTIFICATE)
AND cai.NAME_VALUE ILIKE ('%vil.com')
And it doesn't work for common stems:
WHERE to_tsquery('security:*') @@ identities(cai.CERTIFICATE)
Steven
Rob Stradling
Steven
It strips anything that doesn't match [-a-z0-9._%], looks for leading text search strings and trailing text strings. It can also extract strings from the middle that could be used as leading text strings.
This allows a query like %.%.evil.com to match on www.example.com.evil.com and not www.evil.com (%.%.evil.com AND evil.com)
Or for www.example%.com (www.example%.com AND www.example:*)
Or for %w.example.com.% (%w.example.com.% AND example.com.:*)
I have not tested it against queries that include underscores, but I don't think the web UI appropriately respects them either.
Rob Stradling
The old crt.sh service is still available at the IP addresses below. I anticipate that we'll start to decommission the old servers in a month or two.
OLD:> host crt.sh
crt.sh has address 91.199.212.48
crt.sh has IPv6 address 2a0e:ac00:c7:d430::5bc7:d430
