RCE used by Intermediate CA to issue certificates.
John Han (hanyuwei70)
https://github.com/acmesh-official/acme.sh/issues/4659
Seems like they exploited acme.sh and let user to evade certificate issuing procedure.
Andrew Ayer
and I don't see any evidence that the actual CAs in question evaded any
validation requirements.
HiCA/QuantumCA is just acting as an intermediary between subscribers
and the issuance APIs operated by actual CAs[1]. Literally anyone can
do this and do monumentally stupid/insecure things; it's not productive
to have a discussion every time this happens.
Regards,
Andrew
[1] It's true they have a reseller relationship with ssl.com, who are
operating a white-label intermediate CA with "QuantumCA" in the
subject, but HiCA/QuantnumCA are also fronting other CAs, including
GTS, which doesn't require a reseller agreement to access their free
ACME API, so I don't see that aspect as being productive to discuss
either.
Kurt Seifried
--
You received this message because you are subscribed to the Google Groups "dev-secur...@mozilla.org" group.
To unsubscribe from this group and stop receiving emails from it, send an email to dev-security-po...@mozilla.org.
To view this discussion on the web visit https://groups.google.com/a/mozilla.org/d/msgid/dev-security-policy/20230609090430.3a4e8396e6e0b856fc81c6ab%40andrewayer.name.
ku...@seifried.org
mochaaP
Although HiCA is not a CA itself, the person own HiCA seems also owns (or at least works for) Quantum CA[1][2]. they also confirmed that Quantum CA is operated by both their team and SSL.com team[3].
I think this probably is not as simple as a white-label intermediate CA being abused, rather a CA that resells their own product to themselves to prevent being punished for bad behaviors.
[1]: https://github.com/xiaohuilam (see "Pinned" section)
[2]: https://github.com/quantumca (see "People" section)
Xiaohui Lam
This is HiCA founder, let me to explain your concern, Mr John ,
the RCE is fully used to finish the challenge which validated by CAs, in another word, the ACME.sh-enrolled certificates which passing this RCE, it does compliant with each CA's BR validation requirements. CA did nothing wrong. And also by this trick can enroll any CA's certificate before acme.sh fix patch.
and to Mr @mochaaP, you said to punish our team, we're NOT a public CA or private CA(in my understanding, a CA must manage a or more PKI infrastructure physically), [3]so the clarify relationship to HiCA w/ QuantumCA is no necessary, but we still told we runs HiCA inside QuantumCA project's source code, it's a sub-application inside it.
I agree @Andrew's opinion, CAs shouldn't take any responsibilities to the RCE incidents. or there are hundreds acme-tools for CAs need to concern.
Thomas Zermeno
As a result, we took the initiative to further investigate and discovered that QUANTUM CA LIMITED dissolved on November 1, 2022. We were not notified about this change by Quantum.
Based on this fact, we plan to revoke the Quantum branded subCAs and all associated end-entity certificates within 7 days, as mandated by section 4.9.1.2 of our CP/CPS.
Kurt Seifried
--
You received this message because you are subscribed to the Google Groups "dev-secur...@mozilla.org" group.
To unsubscribe from this group and stop receiving emails from it, send an email to dev-security-po...@mozilla.org.
To view this discussion on the web visit https://groups.google.com/a/mozilla.org/d/msgid/dev-security-policy/528b5350-1a32-4730-8e7b-16644d135274n%40mozilla.org.
Kurt Seifried
--
You received this message because you are subscribed to the Google Groups "dev-secur...@mozilla.org" group.
To unsubscribe from this group and stop receiving emails from it, send an email to dev-security-po...@mozilla.org.
To view this discussion on the web visit https://groups.google.com/a/mozilla.org/d/msgid/dev-security-policy/431eb7de-181e-4a32-9d22-3698bc7b0d0bn%40mozilla.org.
Xiaohui Lam
Xiaohui Lam
mochaaP
Xiaohui Lam
Kurt Seifried
I think the title buries the most horrifying part of this. The HiCA certificate authority is relying on an RCE to do an end-run around the semantics of the ACME HTTP-01 validation method.
Fucked up and they should be booted from every root program for this.
0x0 1 day ago | prev | next [–]
Looks like they are issuing under a sub-CA of "ssl.com" according to https://github.com/acmesh-official/acme.sh/issues/4659#issue...
Interestingly, the mozilla dev-security-policy group seems to contain a recent discussion about including "ssl.com" in the root store here https://groups.google.com/a/mozilla.org/g/dev-security-polic...
Curious to know if this could, maybe it should, have ripple effects to the various SSL Root CA programs. Having someone run a subCA that actually exploits an RCE against ACME clients doesn't seem very trustworthy, and any CA enabling this behaviour should probably be kicked out of the trust stores?
reply
agwa 1 day ago | parent | next [–]
The sub CA is operated by ssl.com, not HiCA (which is not a trusted certificate authority). HiCA is relaying the certificate requests to ssl.com, which is properly validating the requests in accordance with all the requirements. ssl.com isn't doing anything wrong. That's why HiCA needs to exploit an RCE in acme.sh - ACME doesn't support relaying certificate requests to other CAs like this.
reply
0x0 23 hours ago | root | parent | next [–]
Someone posted a comment on github claiming they are the founder of Quantum (the sub CA of ssl.com - see https://crt.sh/?caid=200960 ) and that they are the provider of the HiCA service. So it does sound like there is a closer link here than your comment would indicate:
https://github.com/acmesh-official/acme.sh/issues/4659#issue...
reply
agwa 23 hours ago | root | parent | next [–]
Quantum is not a trusted CA. ssl.com has a white-labeled intermediate CA with the name "Quantum" in it, but this intermediate CA is operated by ssl.com under all the same controls as ssl.com's other intermediate CAs. Quantum has no ability to issue trusted certificates themselves.
reply
0x0 23 hours ago | root | parent | next [–]
So the person claiming to be the founder of "QuantumCA" does not possess the private key corresponding to https://crt.sh/?caid=200960 - can we be sure the private key is only accessible by ssl.com's CA system? So the certificates listed here aren't issued by this person, but by the ssl.com's system? https://crt.sh/?Identity=%25&iCAID=200960&exclude=expired&de...
Also, why would ssl.com even create a subCA named "QuantumCA"? Are they in business with this person claiming to be the founder of "QuantumCA" who appears to be responsible for exploiting this acme.sh 0day? What does this say about ssl.com's trustworthiness? Or is the person in the github comments lying?
reply
agwa 23 hours ago | root | parent | next [–]
> So the person claiming to be the founder of "QuantumCA" does not possess the private key corresponding to https://crt.sh/?caid=200960 - can we be sure the private key is only accessible by ssl.com's CA system? So the certificates listed here aren't issued by this person, but by the ssl.com's system? https://crt.sh/?Identity=%25&iCAID=200960&exclude=expired&de...
Correct. You can see the Quantum intermediates listed in ssl.com's most recent audit statement, meaning an auditor has verified that ssl.com has controls to protect the private key: https://www.cpacanada.ca/generichandlers/CPACHandler.ashx?at...
(The audit could be flawed, but it's the same amount of assurance we have for any intermediate CA's private key - the fact that "QuantumCA" is in the name does not change the risk calculus)
> Also, why would ssl.com even create a subCA named "QuantumCA"? Are they in business with this person claiming to be the founder of "QuantumCA" who appears to be responsible for exploiting this acme.sh 0day? What does this say about ssl.com's trustworthiness? Or is the person in the github comments lying?
There is a business relationship between QuantumCA and ssl.com. QuantumCA is a reseller of ssl.com, and they've paid extra to ssl.com so that the certificates they purchase get issued from an intermediate CA named "QuantumCA" rather than one of ssl.com's usual intermediate CAs which have "ssl.com" in the name. This lets QuantumCA pretend to be a real CA. This is a common practice in the industry, and I don't think it says anything about the trustworthiness of ssl.com, because the business relationship with QuantumCA doesn't in any way subvert the integrity of the WebPKI since ssl.com retains control of the issuance. Still, I wish intermediate CA white-labeling were banned because it causes terrible confusion about who is and isn't a CA.
reply
0x0 23 hours ago | root | parent | next [–]
I find it troubling that a root CA (ssl.com) is apparently OK with lending their name in a business relationship with an actor that is actively exploiting an acme.sh 0day.
tptacek 20 hours ago | root | parent | next [–]
This feels a little bit like doubling down to find ways to implicate the actual CA instead of the reseller. It's clear how mismanagement by a real CA would make a more interesting story than by this random no-longer-existing pseudo-reseller, but I don't think there's evidence to support that story yet.
reply
0x0 20 hours ago | root | parent | next [–]
But it's not a random pseudo-reseller? The one github comment from "the founder of Quantum CA" seems to say they are also the creator of HiCA, which is the entity that was exploiting the 0day in acme.sh. And the crt.sh link shows an intermediate CA cert named "QuantumCA", signed by ssl.com.
So QuantumCA == HiCA == exploiters of the acme.sh 0day, it's all the same entity? The intermediate CA could just as well be named "0dayexploitersCA"? Why is it not a huge concern that ssl.com is fine with operating such a "0dayexploitersCA" intermediate?
Am I missing something here?
reply
--
You received this message because you are subscribed to the Google Groups "dev-secur...@mozilla.org" group.
To unsubscribe from this group and stop receiving emails from it, send an email to dev-security-po...@mozilla.org.
To view this discussion on the web visit https://groups.google.com/a/mozilla.org/d/msgid/dev-security-policy/0f9174b3-02d6-4ff6-a7fa-3b931375076dn%40mozilla.org.
Kurt Seifried
Mr Seifried,
> Is this really a situation where something extremely suspicious (remote code execution, CA's with multiple entities, some of which don't seem to properly exist, etc.) is going to be swept under the rug with a simple "yeah, we revoked this bad actors certificates, everything is fine"?
We are a reseller, not a physical root CA. This is a widely accepted solution for cross border businesses. We have business accepts online payment, the China users needs pay via alipay or wechat, to sign up the merchant we must have a china company,and foreign needs stripe, merchant must be a non-MainlandChina company. this is not suspicious.*. I represent the above opinion of my company
> If HiCA can do this, how do we know there are not more intermediate/reseller CAs doing this?
Most CA has no necessary to exploiting this RCE, because they can natively compatible with RFC 8555, they can define own CPS and CP, which contains validation policy, we does because we are not CA and can't to provider RFC 8555 ACME endpoint like a CA does. so a physical root CA has no necessary to provide ACME simulation by RCE. and also there're more difficulties for a ssl reseller to provide ACME service which real CAs won't undergo.- CSR stage difference: Most CA's subscriber request process or reseller API process, requires CSR be submitted in the `new-order` API, ACME requires CSR be submitted in `finalize` API. I have a topic in letsencrypt community years ago about this - https://community.letsencrypt.org/t/why-acme-requires-domain-auth-first-before-csr/98482- Challenge difference: Most CA's subscriber request process or reseller API process's DNS validation requires `_<md5>` / `_dnsauth` dnshost, and dnstype possibly CNAME or possibly TXT, But ACME's DNS validation dnshost is constant: `_acme-challenge`, dnstype `TXT`. And in a more deep talk ACME's dnsvalue needs publickey's thumbprint + server token which is totally different than traditional way's dnsvalue.My opinion is community can research how many ACME was publicly provided, and investigate is the provider a physical CA. if is natively compatible with RFC 8555, no worry about that one and continue do investigate next.*. I represent the above opinion of my personal. not my company.Sincere,Bruce.
Amir Omidi (aaomidi)
Xiaohui, can you please confirm that ssl.com was the only actual CA that was used for issuance through HiCA?
Xiaohui Lam
Xiaohui Lam
Xiaohui Lam
Xiaohui Lam
Xiaohui Lam
Kurt Seifried
James Kasten
To be explicit, GTS does not have a business relationship with HiCA.
Normally ACME services have protections against these types of MitM-CAs, but the remote RCE allowed HiCA to bypass these controls [1, 2].
For instance, it is possible HiCA replaced the local client's key authorization during challenge validation with a key authorization provided by HiCA, granting authorization of the domain names to HiCA. HiCA could theoretically use these authorizations to continue to issue certificates for the affected domain names, or revoke the certificates that were issued.
So clients of HiCA should also consider the lasting effects on the the domains in addition to your normal recovery procedures for an RCE. It may be prudent to reissue and revoke any certificates with your choice of CA directly and to watch certificate transparency logs for any future unintended issuance. GTS allows authorization reuse up to 28 days on our ACME endpoint and issues certificates with lifetimes up to 90 days. Other CAs may differ. By the current baseline requirements CAs can issue 398 day certificates and reuse the authorizations for 398 days [3].
Google Trust Services
2. https://datatracker.ietf.org/doc/html/rfc8555#section-10.2
3. https://cabforum.org/wp-content/uploads/CA-Browser-Forum-BR-1.8.7.pdf
James Kasten
Xiaohui Lam
We apologize for the impact of the security incident on GTS.
I want to say that we will not do bad things, but we lack the means of notarization.
But there is a suggestion:
GTS could evaluate to disable pre-authorizations for domain names or IP addresses for the next 90 days, to reduce potential impacts of the incident.
Levi
In conclusion, there are things we know:
1. There is not any reported security of CA issues (Sectigo, GTS, and more).
2. HiCA used the RCE leak of ACME but has not caused any security problems (as of now).
3. People think the CA must take action to protect the system security (not only for CA's system)
Thomas Zermeno
However, SSL.com's free community ACME 90-day certs have been available since 2021 and we have no involvement, collaboration, or control over any ACME client scripts or applications including HiCA's acme.sh. Our courtesy ACME service is available in a similar vein as other free publicly trusted ACME TLS certificate providers with no restrictions or consideration on which ACME clients are allowed access to this service.
We do not collaborate on any projects with our SSL/TLS SubCA resellers other than to provide them brandable certificates. Many members of the community find brandable SubCAs valuable to help build reputation without having to invest in a fully dedicated CA infrastructure, and most reseller customers handle the privilege of their SubCAs responsibly. Unfortunately, there are cases where abuse, intentional or otherwise, may crop up. At SSL.com, we make every effort to respond swiftly and firmly whenever we are alerted of any issues related to our branded SubCAs.
In particular, SSL.com has already planned revocation of the branded SubCAs within the required 7-day time window from the moment we discovered the dissolution of QUANTUM CA LIMITED, in full compliance with our CP/CPS and the CA/B Forum Baseline Requirements. We are also reaching out to individual subscribers affected by this upcoming revocation event to minimize the impact.
Still, there are lessons to learn from this event. Although our CP/CPS stipulates customers’/resellers’ obligation to notify SSL.com of any business registration modification (which includes dissolution), we plan to introduce proactive measures, such as applying periodic reverification of all SubCA resellers' business registrations.
Finally, we view unwarranted statements, which are probably in violation of the Mozilla Community Participation Guidelines, or individual customer-to-company issues such as “refunds” as off-topic and will directly communicate with the reseller on such matters. We consider dev-security-policy group to be a public Forum to discuss ecosystem-wide security/policy issues and good practices. For example, we could discuss with other CAs to adopt the above-mentioned periodic reverification to further protect the ecosystem.
Xiaohui Lam
> in full compliance with our CP/CPS and the CA/B Forum Baseline Requirements. We are also reaching out to individual subscribers affected by this upcoming revocation event to minimize the impact.
There is a proverb called "My customer's customer, isn't my customer".
We stand against poaching our clients, and I'm sure any reseller does too.
Thomas Zermeno
Watson Ladd
>
> We agree with SSL.com canceling the 90-day certificate customers under Quantum subCA, but we object to the annual customer service payment.
> Should SSL.com refund some of the certificates because they were multi-year subscription certificates purchased?
>
> If not, why not cancel the product purchase entrance for more than 365 days on your website and interface?
>
> It's likely a fraud in business.
committed what looks to all the world like a CFAA violation. I'm
struggling to understand why you would think this was acceptable
conduct to use an RCE in issuance, in short running code on sensitive
machines without user consent.
Furthermore the CA business is built on trust. SSL.com is doing the right thing.
Sincerely,
Watson Ladd
> You received this message because you are subscribed to the Google Groups "dev-secur...@mozilla.org" group.
> To unsubscribe from this group and stop receiving emails from it, send an email to dev-security-po...@mozilla.org.
--
Astra mortemque praestare gradatim
John Liptak
Xiaohui Lam
Again,
We agree ssl.com to cancel free certificates.
It means there aren't only free certificates we're providing. But also paid certificates, if only annually(1 year) cert been cancelled it be fine we can take it, but there are many multiple year subscription purchased by our users(including some OV certs).
If you bought something with a period of many years, but delivered it on an annual basis, and the merchant ran away after one year, would you defend your consumer rights?
It should sounds fair to refund remaining subscriptions' fee if cancelled? Especially we haven't to proof OV or EV is associated with HiCA because the CA's OV/OV won't become issued automatically after domain names been validated. so HiCA didn't implement them ever.
We agree to revoke free certificates because our integrating on HiCA, certificates provided were only free. No CA's paid product was integrated ever.
personal word from me, Mr Ladd, It is recommended not to do serious injuries because that are not gentlemen. Did you see someone disclose that the server was hacked after run `acme.sh --issue --server https://acme.hi.cn/directory` on the Internet, or did you get a completely offensive injection code? We can accept a source code audit of the project w/ full git log and databases binlog if you're willing to bear the cost and we think it's fair because your keyboard swearing didn't pay for anything but electricity so you want to blame please prove it, if exists and we shall keep our ears open.
Xiaohui Lam
First, the cryptography license license is mandatory only for CAs (organizations who operate PKI facilities);
Secondly, There are many sole proprietorship (self-employed people) are also selling SSL digital certificates and running their own websites, which is totally unable to enroll ICP Registration License.
And your post is completely weering off topic.
Xiaohui Lam
Watson Ladd
>
> @Watson Ladd,
>
> Again,
>
> We agree ssl.com to cancel free certificates.
> It means there aren't only free certificates we're providing. But also paid certificates, if only annually(1 year) cert been cancelled it be fine we can take it, but there are many multiple year subscription purchased by our users(including some OV certs).
> If you bought something with a period of many years, but delivered it on an annual basis, and the merchant ran away after one year, would you defend your consumer rights?
Sincerely,
Watson Ladd
Amir Omidi
--
You received this message because you are subscribed to a topic in the Google Groups "dev-secur...@mozilla.org" group.
To unsubscribe from this topic, visit https://groups.google.com/a/mozilla.org/d/topic/dev-security-policy/heXVr8o83Ys/unsubscribe.
To unsubscribe from this group and all its topics, send an email to dev-security-po...@mozilla.org.
To view this discussion on the web visit https://groups.google.com/a/mozilla.org/d/msgid/dev-security-policy/CACsn0c%3DjQwd035WhDnWJe-BfrKY8Xfxq0_cKUFHDj2W4oWe6-Q%40mail.gmail.com.
Xiaohui Lam
Xiaohui Lam
Are you advising our client to accept deprivation of the remaining 4 years of the certificate w/o CA' evaluation whether it is affected by RCE certificates of them ?
Sorry we dare not make such a suggestion because we are resellers. Nor Akamai's resellers won't if incidents happen.
Sincerely,
Bruce Lam.
inao...@gmail.com
> First, the cryptography license license is mandatory only for CAs (organizations who operate PKI facilities);
John Liptak
xiaohuilam
I will introduce some of the origins of these IDs with me.
After Matthew Holt revealed that ACME.sh had an RCE vulnerability and was exploited by HiCA, our 2 Chinese servers and 6 overseas servers were severely attacked by DDOS, and also considered to so we try to close HiCA to avoid DDOS attacks from affecting our kernel business users (it is web page accepts CSR to issue certificates which registered online, which has nothing to do with ACME in command line).
However, due to DNS cache and other reasons, the attack continued; during this period, we analyzed the logs and switched routes to block a large number of IPs. Later we saw that acme.hi.cn and www1.hi.cn had no traffic at all and the attack was still affecting until we saw
- https://hostloc.com/thread-1177834-1-1.html
(He tried to call on others to participate in the CC Flood/DDOS website using the webbench tool made by golang, and we believe himself participated)
We contacted the attack source IP ASN owner/ISP: the abuse prevention team of IPXO LLC, and finally blocked the attacker's IP.
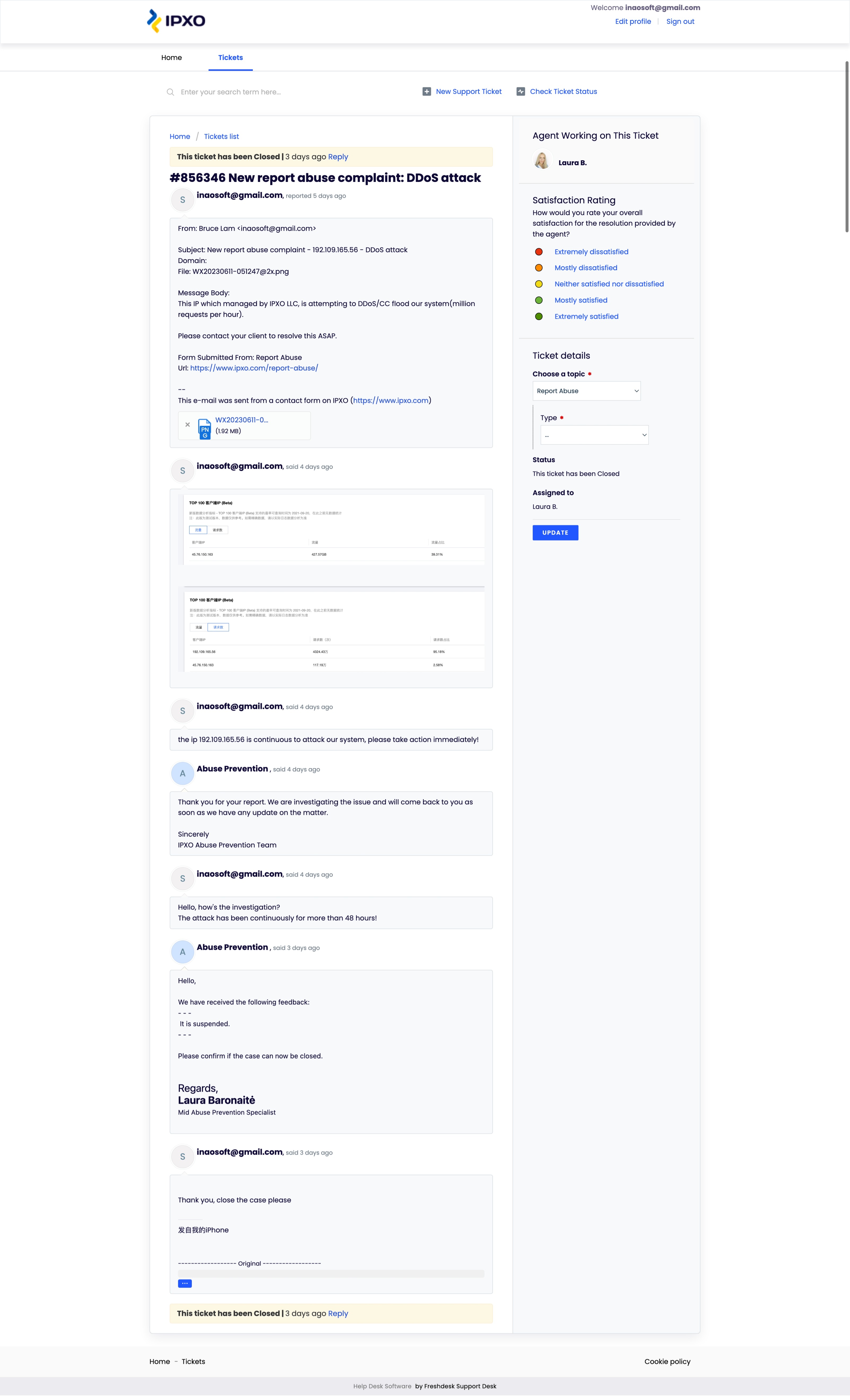
When we collected all the evidence and prepared to report the case added a statement on restored www1.hi.cn website and, the attacker’s settlement new topic came, to compromise
- https://hostloc.com/thread-1178837-1-1.html
- https://hostloc.com/thread-1179012-1-1.html
The other party expressed their willingness to pay for the part of the bill that we can prove to be related to him due to the loss caused by DDOS. We did not take the next legal action to advocate punishment for the network DDOS attackers because they did pay me:
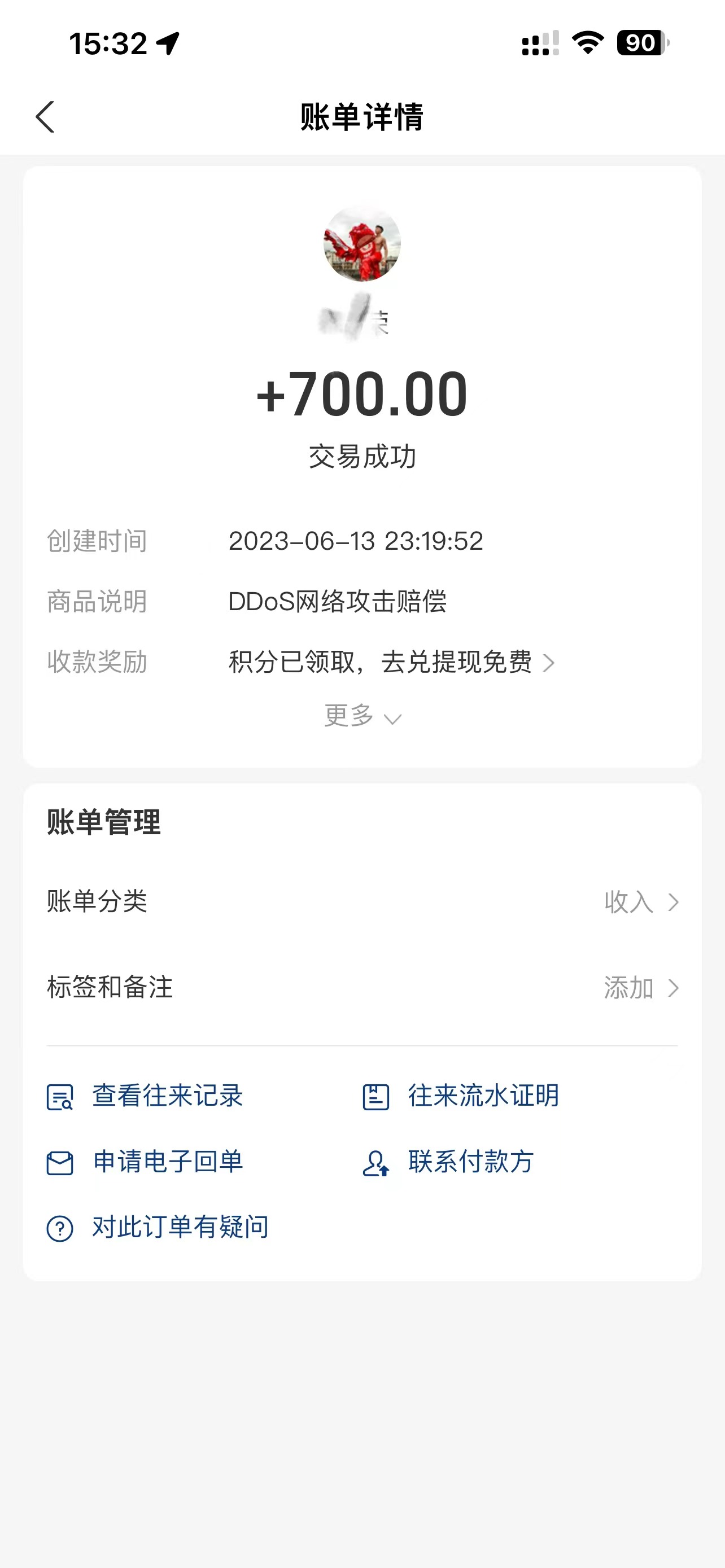
(Note that the memo information of the other party’s remarks is: DDOS attack compensation. To protect the privacy of him we did mosaic)
We thought the matter was over. I had some unanswered questions on twitter just before Matthew Holt's twitter reply. (Forgive the twitter account I registered more than ten years ago that has not been used for a long time and cannot meet the risk control; it took a lot of time to re-register one).
Until this Issues appeared,
- https://github.com/acmesh-official/acme.sh/issues/4675
It's hard to imagine such abusive voices in the community and on the dev-security-policy mailing list. Even though it's an accusation we can try to respond to, it's frustrating that this post isn't a technical accusation. And we found an interesting thing:
The issuer ID gzchjz007 of https://github.com/acmesh-official/acme.sh/issues/4675 is highly similar to the criminal ID gzchenjz of our ddos server!
When I pointed out that their slander is fake, this ID gzchjz007 and gzchenjz stopped acting, but a new ID appeared, and came to this dev-security-policy post. That's why I think they're suspicious:
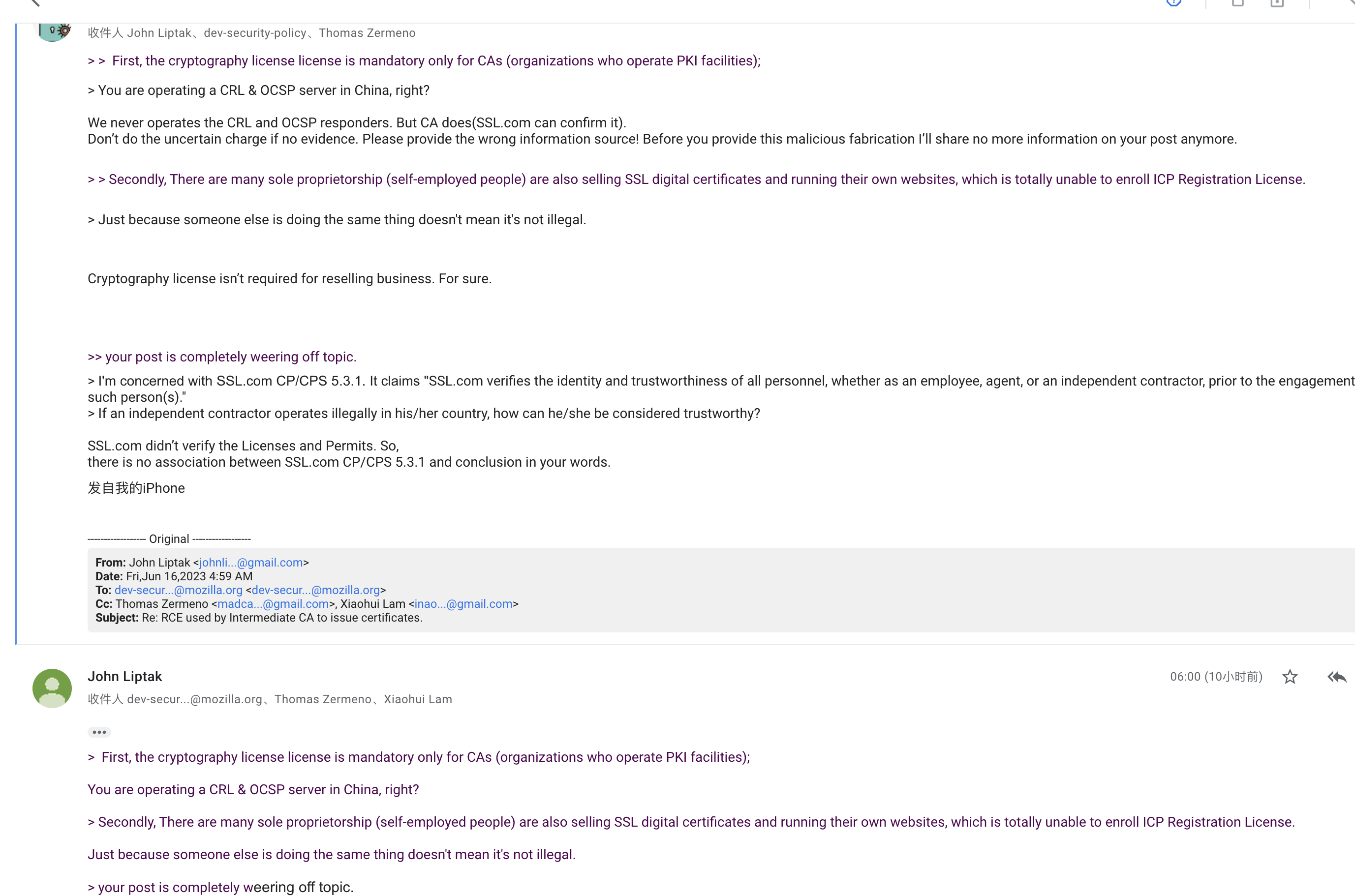
Dear members.
I have conducted a background check on HiCA administrator Xiaohui Lam and would like to share the following with you. These findings are for reference only, so please evaluate them for yourself.
First, in 2013, Xiaohui Lam hijacked AFF promotions by exploiting vulnerabilities in Aliyun forums, defrauded hostloc members by installing backdoors in Discuz forum plugins, and stole others' social accounts through leaked data from CSDN [^1].
Second, in 2015, Xiaohui Lam exploited a vulnerability in the GlobalSign system to sell a large number of 5-year wildcard certificates, but all certificates were revoked after they were discovered [^2].
I would like to emphasize that these are past actions of HiCA administrators and I do not think he will repeat the same mistakes again. However, these events show that he is not a developer who knows very little about security. In the past, he has been someone who knew how to mine vulnerabilities, exploit them and commit fraud and threats against customers.
Based on the above findings, I believe we need to take the following steps:
1. Considering that he suggested users to execute his script RCE[^3] with root privileges on his official website, we should send a reminder email to all users who have applied for a certificate, asking them to evaluate whether there is unauthorized code on their machines.
2. the results of the query found that Mr. Lam has two CAs: HiCA and Quantum CA. the website for registration information about Quantum CA is acme.hi.cn. then we need to confirm whether they are using the same infrastructure and whether Quantum CA also uses RCE to issue certificates [^4].
Mr. Lam has shut down HiCA's infrastructure after he was found to be using RCE, but we still need to do a more detailed assessment.
As a member of the community, I believe transparency and trust are vital to us. I hope Mr. Lam will provide the community with a more complete statement and evidence so that the community can evaluate this incident.
[^1]: https://web.archive.org/web/20130816004143/http://bbs.aliyun.com/read.php?tid=144441
Roger M Lambdin
I have conducted a background check on HiCA administrator Xiaohui Lam and would like to share the following with you. These findings are for reference only, so please evaluate them for yourself.
First, in 2013, Xiaohui Lam hijacked AFF promotions by exploiting vulnerabilities in Aliyun forums, defrauded hostloc members by installing backdoors in Discuz forum plugins, and stole others' social accounts through leaked data from CSDN [^1].
Second, in 2015, Xiaohui Lam exploited a vulnerability in the GlobalSign system to sell a large number of 5-year wildcard certificates, but all certificates were revoked after they were discovered [^2].
I would like to emphasize that these are past actions of HiCA administrators and I do not think he will repeat the same mistakes again. However, these events show that he is not a developer who knows very little about security. In the past, he has been someone who knew how to mine vulnerabilities, exploit them and commit fraud and threats against customers.
Based on the above findings, I believe we need to take the following steps:
1. Considering that he suggested users to execute his script RCE[^3] with root privileges on his official website, we should send a reminder email to all users who have applied for a certificate, asking them to evaluate whether there is unauthorized code on their machines.
2. the results of the query found that Mr. Lam has two CAs: HiCA and Quantum CA. the website for registration information about Quantum CA is acme.hi.cn. then we need to confirm whether they are using the same infrastructure and whether Quantum CA also uses RCE to issue certificates [^4].
Mr. Lam has shut down HiCA's infrastructure after he was found to be using RCE, but we still need to do a more detailed assessment.
As a member of the community, I believe transparency and trust are vital to us. I hope Mr. Lam will provide the community with a more complete statement and evidence so that the community can evaluate this incident.
[^1]: https://web.archive.org/web/20130816004143/http://bbs.aliyun.com/read.php?tid=144441
Amir Omidi
--
You received this message because you are subscribed to a topic in the Google Groups "dev-secur...@mozilla.org" group.
To unsubscribe from this topic, visit https://groups.google.com/a/mozilla.org/d/topic/dev-security-policy/heXVr8o83Ys/unsubscribe.
To unsubscribe from this group and all its topics, send an email to dev-security-po...@mozilla.org.
To view this discussion on the web visit https://groups.google.com/a/mozilla.org/d/msgid/dev-security-policy/CAEi6wDMyvGa26QOoa4CzqqbW-cYJfWDpJDpxS3e1EaGG1TbOng%40mail.gmail.com.
Xiaohui Lam
Rob Stradling
Sent: 16 June 2023 18:07
To: xiaoh...@e.hexdata.cn <xiaoh...@e.hexdata.cn>
Cc: John Liptak <johnli...@gmail.com>; Roger M Lambdin <bir...@gmail.com>; Thomas Zermeno <madca...@gmail.com>; dev-secur...@mozilla.org <dev-secur...@mozilla.org>
Subject: Re: RCE used by Intermediate CA to issue certificates.
To view this discussion on the web visit https://groups.google.com/a/mozilla.org/d/msgid/dev-security-policy/CAOG%3DJULbAtbs-nLrs8ZhapgNHj6-yno0hnytFV9F%3DQmPdMw4EQ%40mail.gmail.com.
John Liptak
inao...@gmail.com
John Liptak
Xiaohui Lam
Thomas Zermeno
With regards to other issues raised in the discussion and which mention SSL.com:
Before issuing SubCAs to any resellers, SSL.com performs verification equivalent to an Extended Validation review of the organization applying for the SubCA(s). In summary, this includes verification of the legal, physical and operational existence, and verification of the authorization of the request. It does not include background checks, reputational research, or any checks for criminal records of the organization representatives, other than checks against the applicable sanctions lists.
In the case of Quantum, our checks included doing lookups on the organization using the UK Registry Companies House and a Qualified Independent Information Source (QIIS), verifying the identity of contact persons representing the organization and comparing them against several US sanctions lists. Additionally, we performed live interviews with company representatives over teleconference and via the verified means of communication with the organization. All required verifications were performed and approved before issuance of QuantumCA’s SubCAs.
Furthermore, we confirm that the sole purpose of domain sslcom.cn was to serve CRL and OCSP responses, and SSL.com is the only entity operating the OCSP responders and CRL distribution points under that domain. There are no active certificates relying on that domain.
Finally, we would like to point out that section 5.3.1 of our CP/CPS only applies to employees, agents or independent contractors of SSL.com and delegated third parties which are engaged in the Certificate Management Process. As a branded SubCA consumer, QuantumCA was not a delegated third party of SSL.com. Although not required, SSL.com still performed EV review on them as we do with all other SubCA resellers.
To summarize, the Quantum SubCAs were never enabled for ACME by SSL.com and they could not have been used to issue certificates with the vulnerable acme.sh client. During the course of this discussion, due to the dissolution of Quantum CA Limited, we took additional action in revoking their SubCAs. We hope these statements address all relevant concerns regarding HiCA’s use of Quantum SubCAs issued by SSL.com.
San Wong
- ocsp.sslcom.cn returned an incorrect response to the ocsp verification request, so the certificate could not be revoked.
- crl.sslcom.cn responds to historical data (data before revoking), and the cache time is as long as 1 year.
```
# openssl crl -inform DER -in http://crl.sslcom.cn/SSLcom-RootCA-RSA-4096-R1.crl -text -issuer -hash -lastupdate -nextupdate
issuer=/C=US/ST=Texas/L=Houston/O=SSL Corporation/CN=SSL.com Root Certification Authority RSA
6fa5da56
lastUpdate=Jun 15 15:54:47 2023 GMT
nextUpdate=Jun 9 15:54:46 2024 GMT
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: /C=US/ST=Texas/L=Houston/O=SSL Corporation/CN=SSL.com Root Certification Authority RSA
Last Update: Jun 15 15:54:47 2023 GMT
Next Update: Jun 9 15:54:46 2024 GMT
CRL extensions:
X509v3 Authority Key Identifier:
keyid:DD:04:09:07:A2:F5:7A:7D:52:53:12:92:95:EE:38:80:25:0D:A6:59
X509v3 CRL Number:
19
Revoked Certificates:
...
```
Thomas Zermeno
San,
update and reissue CRLs at least:
• once every twelve (12) months and
• within twenty-four (24) hours after revoking a Subordinate CA Certificate,
and the value of the nextUpdate field must not be more than twelve (12) months beyond the
value of the thisUpdate field.
- 4E33A3DF038C94BD5611A51814F68CE9 (revoked 2023-06-15 15:53:15 UTC)
- 663E22B3F73CCB78DC74369353AB24C3 (revoked 2023-06-15 15:53:16 UTC)
- 50758BB068C7CA6BF84CC950ABC26539 (revoked 2023-06-15 15:53:17 UTC)
- 3348510D6AA99654904848A14BE65170 (revoked 2023-06-15 15:53:18 UTC)
- 0AF338327C1D48BA41753EBEB9EA6029 (revoked 2023-06-15 15:53:20 UTC)
- 4EB6AD64EA15BA233C32B0D491670063 (revoked 2023-06-15 15:53:21 UTC)
Jesper Kristensen
This is to provide an update on the revocation of the QuantumCA SubCAs. They were all revoked within the required timeframe. Since they were never enabled for ACME, there was never an issue with these SubCAs being used in the HiCA acme.sh RCE client.
