Android App Fido2 Registration Error
Ric Janus Sapasap
https://fido2-test.api.ewallet.pearlpay.io:8181/.well-known/assetlinks.json

Arshad Noor
Hi Janus,
I presume you're referring to the use of this API here: https://developers.google.com/android/reference/com/google/android/gms/fido/fido2/Fido2ApiClient
I wish we could help, but unfortunately, we haven't used this API to create an Android app that works with our server. One concern of ours was related to the fact that this is not an Android API, but a Google Play Services API - which requires (to the best of my understanding) an app using this API to require users of the app to have a Google Play Services account. Since these APIs most likely end up calling/using Google Play Services resources, there is some concern on our part that there may be privacy implications in the use of these APIs. I have no evidence of this, but I also do not see any assertions by Google that these APIs are privacy protecting.
If you're interested in a native Android API based library for
Android apps, there is another library we released in Preview Mode
last month:
https://github.com/StrongKey/fido2/tree/master/sampleapps/java/sacl.
Leveraging Android BiometricPrompt, AndroidKeystore
with TEE or SE (if present), and delivering an Android Key
Attestation to our FIDO2 Server, there is a proof-of-concept
Android app in that folder to demonstrate how it all comes
together. If you do decide to look into it and work with it,
please direct any questions you may have to the Github listserv
for that project- the FIDO-DEV list is intended for generalized
questions about the FIDO protocol rather than about specific
implementations.
Thanks.
Arshad Noor
StrongKey
--
You received this message because you are subscribed to the Google Groups "FIDO Dev (fido-dev)" group.
To unsubscribe from this group and stop receiving emails from it, send an email to fido-dev+u...@fidoalliance.org.
To view this discussion on the web visit https://groups.google.com/a/fidoalliance.org/d/msgid/fido-dev/c125fc92-baec-4ce9-927b-1a9c0dc91a6bn%40fidoalliance.org.
Manger, James
Will Android accept /.well-known/assetlinks.json hosted on non-standard port 8181? I’m not sure.
The point of /.well-known/ is to provide definitive info about a domain, perhaps not for an origin (scheme + domain + port).
--
James Manger
From:
fido...@fidoalliance.org <fido...@fidoalliance.org> on behalf of Ric Janus Sapasap <r...@pearlpay.io>
Date: Friday, 30 April 2021 at 1:29 am
To: FIDO Dev (fido-dev) <fido...@fidoalliance.org>
Subject: [FIDO-DEV] Android App Fido2 Registration Error
|
[External Email] This email was sent from outside the organisation – be cautious, particularly with links and attachments. |
Hi,
I'm currently creating a Proof of concept android application using Fido2, using the StrongKey fido2 open source server and their basic java server example:
I want to replicate the behavior in their basic java server example using an android app.
I'm having problems using the default android provided Fido2ApiClient, when calling getRegisterPendingIntent, it results in an error:
"The incoming request cannot be validated"
"SECURITY_ERR" error code 18
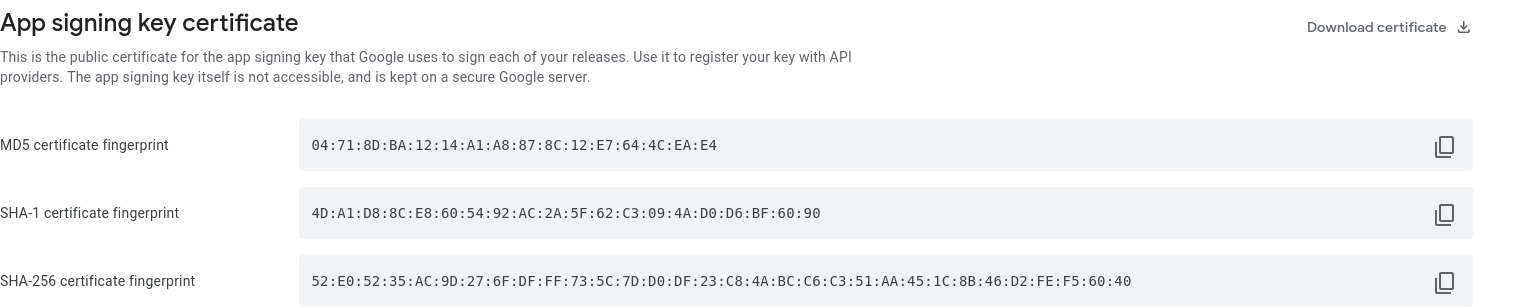
I have already have a public digital asset link hosted for both debug and internal release signing keys:
https://fido2-test.api.ewallet.pearlpay.io:8181/.well-known/assetlinks.json
I also tried doing an internal release APK to check if that is needed for the registration to work, to no avail.
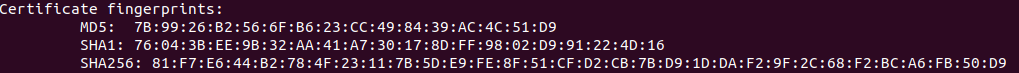
internal release SHA-256:

debug SHA-256:
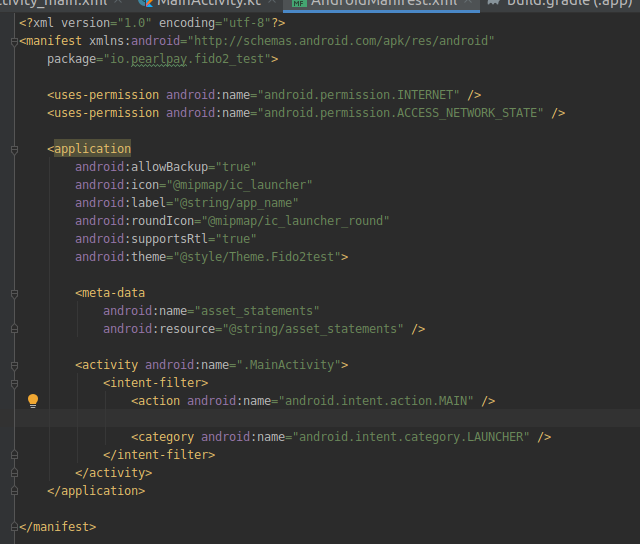
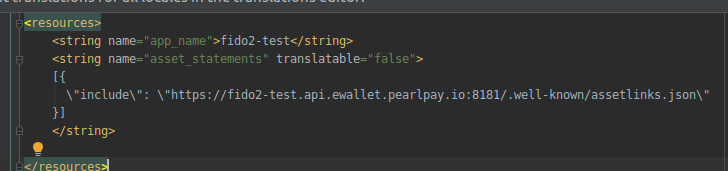
I have also added the corresponding settings in the android application (in AndroidManifest.xml and string asset_statements values):
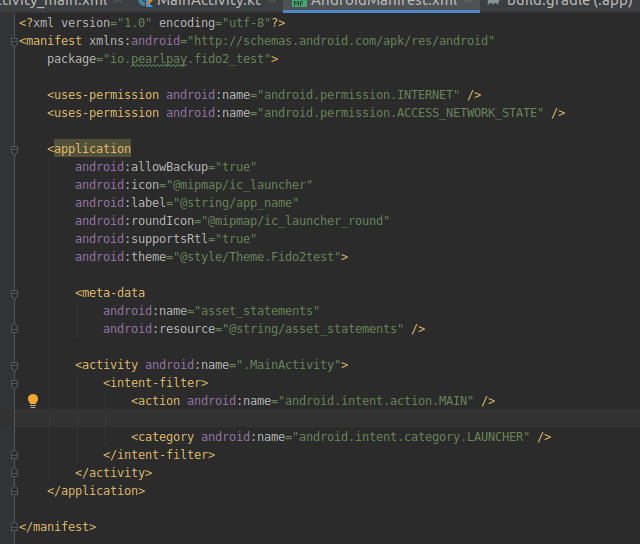

Can anyone help me to get this working? Thank you!
Please don't hesitate to ask for more information.
--
Ric Janus Sapasap
Ric Janus Sapasap
Dominik Schuermann
@Arshad: pretty interesting library, thanks for sharing :)
We also developed an SDK for Android to implement FIDO2 without using
the Google Play Services. Our use cases focus on the usage with external
USB and NFC security keys, that's why we implemented the CTAP2 part.
Maybe it's interesting for you:
A sample guide: https://hwsecurity.dev/guide/fido2/
We also have a GPLv3 version for inspecting the code:
https://github.com/cotechde/hwsecurity
Cheers
Dominik
On 29.04.21 21:03, Arshad Noor wrote:
> Hi Janus,
>
> I presume you're referring to the use of this API here:
> https://developers.google.com/android/reference/com/google/android/gms/fido/fido2/Fido2ApiClient
>
> I wish we could help, but unfortunately, we haven't used this API to
> create an Android app that works with our server. One concern of ours
> Play Services/ API - which requires (to the best of my understanding) an
> Services account. Since these APIs most likely end up calling/using
> Google Play Services resources, there is some concern on our part that
> there may be privacy implications in the use of these APIs. I have no
> evidence of this, but I also do not see any assertions by Google that
> these APIs are privacy protecting.
>
> If you're interested in a native Android API based library for Android
> apps, there is another library we released in Preview Mode last month:
> https://github.com/StrongKey/fido2/tree/master/sampleapps/java/sacl.
>
> (if present), and delivering an /Android Key Attestation/ to our FIDO2
>> debug SHA-256:
>>
>> I have also added the corresponding settings in the android
>> application (in AndroidManifest.xml and string asset_statements values):
>>
>>
>> Can anyone help me to get this working? Thank you!
>> Please don't hesitate to ask for more information.
>> --
>> You received this message because you are subscribed to the Google
>> Groups "FIDO Dev (fido-dev)" group.
>> To unsubscribe from this group and stop receiving emails from it, send
>> an email to fido-dev+u...@fidoalliance.org
>> https://groups.google.com/a/fidoalliance.org/d/msgid/fido-dev/c125fc92-baec-4ce9-927b-1a9c0dc91a6bn%40fidoalliance.org
> --
> You received this message because you are subscribed to the Google
> Groups "FIDO Dev (fido-dev)" group.
> To unsubscribe from this group and stop receiving emails from it, send
> an email to fido-dev+u...@fidoalliance.org
> <https://groups.google.com/a/fidoalliance.org/d/msgid/fido-dev/84db840e-bf5f-0ee7-fdf1-05481829e51b%40strongkey.com?utm_medium=email&utm_source=footer>.
Ric Janus Sapasap
Arshad Noor
interesting too. Please allow me some time to review and get back to you.
Arshad
Ric Janus Sapasap
Dominik Schuermann
the current version focuses on external authenticators and does not
provide support for platform authenticators. This is due to the fact
that our paying customers have high security requirements and deploy
Android devices in an industrial context, where one device is shared by
multiple users. This almost automatically leads to NFC smartcards /
security keys given to individual employees.
Sounds like Arshad's implementation supports platform authenticators,
but I haven't tried it out.
Cheers
Dominik
> >> Leveraging Android /BiometricPrompt/, /AndroidKeystore/ with TEE
> or SE
> >> (if present), and delivering an /Android Key Attestation/ to our
> FIDO2
> >> Server, there is a proof-of-concept Android app in that folder to
> >> demonstrate how it all comes together. If you do decide to look
> into
> >> it and work with it, please direct any questions you may have to
> the
> >> Github listserv for that project- the FIDO-DEV list is intended for
> >> generalized questions about the FIDO protocol rather than about
> >> specific implementations.
> >>
> >> Thanks.
> >>
> >> Arshad Noor
> >> StrongKey
> >>
> >> On 4/29/21 8:29 AM, Ric Janus Sapasap wrote:
> >>> Hi,
> >>>
> >>> I'm currently creating a Proof of concept android application
> using
> >>> Fido2, using the StrongKey fido2 open source server and their
> basic
> >>> java server example:
> >>>
> >>> https://github.com/StrongKey/fido2
> >>>
> >>> https://fido2-test.api.ewallet.pearlpay.io:8181/
>
> >>>
> >>
> >> --
> >> You received this message because you are subscribed to the Google
> >> Groups "FIDO Dev (fido-dev)" group.
> >> To unsubscribe from this group and stop receiving emails from
> it, send
> >> an email to fido-dev+u...@fidoalliance.org
> >> <mailto:fido-dev+u...@fidoalliance.org>.
> >> To view this discussion on the web visit
> >>
> https://groups.google.com/a/fidoalliance.org/d/msgid/fido-dev/84db840e-bf5f-0ee7-fdf1-05481829e51b%40strongkey.com
> <https://groups.google.com/a/fidoalliance.org/d/msgid/fido-dev/84db840e-bf5f-0ee7-fdf1-05481829e51b%40strongkey.com>
>
> >>
> <https://groups.google.com/a/fidoalliance.org/d/msgid/fido-dev/84db840e-bf5f-0ee7-fdf1-05481829e51b%40strongkey.com?utm_medium=email&utm_source=footer>>.
> >>
> >
>
> --
> You received this message because you are subscribed to the Google
> Groups "FIDO Dev (fido-dev)" group.
> To unsubscribe from this group and stop receiving emails from it, send
> an email to fido-dev+u...@fidoalliance.org
> <mailto:fido-dev+u...@fidoalliance.org>.
> To view this discussion on the web visit
> <https://groups.google.com/a/fidoalliance.org/d/msgid/fido-dev/b4c1939e-a618-4196-a405-2b8082d2dbcfn%40fidoalliance.org?utm_medium=email&utm_source=footer>.
