Intent to Ship: Cookies Having Independent Partitioned State (CHIPS)
Dylan Cutler
Contact emails:
dylan...@google.com, kaust...@google.com
Proposal repository:
https://github.com/privacycg/CHIPS
Design doc:
https://docs.google.com/document/d/1wL2lCXpaVOi0cWOn_ehfLFIZQxT3t0SH-ANnZYPEB0I/edit?usp=sharing
Specification:
https://datatracker.ietf.org/doc/draft-cutler-httpbis-partitioned-cookies/
Summary:
Given that Chrome plans to deprecate unpartitioned third-party cookies, we want to give developers the ability to use cookies in cross-site contexts that are partitioned by top-level site to meet use cases that don't track users cross-site (e.g. SaaS embeds, headless CMS, sandbox domains, etc.). Chrome will introduce a mechanism to opt into having third-party cookies partitioned by top-level site using a new cookie attribute, Partitioned.
Since we announced our Intent to Experiment with CHIPS, there have been some changes to the API:
The Partitioned attribute no longer requires the __Host- prefix or its required attributes. The Secure requirement remains.
We are changing the per-partition-per-domain limit to be based on the total size (in bytes) of the cookies set by a domain in a particular partition in addition to the number of cookies. We intend to impose a limit of 10 KB per-embedded-site, per-top-level-site and increase the numeric limit from 10 to 180.
For sites embedded in top-level domains that are in a First-Party Set, their cookies' partition key will no longer be the owner domain of that set. Rather, the partition key will always be the top-level domain that the cookie was created on.
Blink component:
TAG review:
https://github.com/w3ctag/design-reviews/issues/654 (Supportive early review)
https://github.com/w3ctag/design-reviews/issues/779 (Oct 19 specification review)
Risks
Interoperability and Compatibility
Firefox: Positive
WebKit: Supported incubation, Official position pending
Web developers: Developers have indicated that CHIPS does solve for many use cases that depend on access to cookies in cross-site contexts (1, 2, 3). Through incubation, and the Origin Trial, we received feedback to improve ease-of-use, particularly to allow for easier migration of existing systems to use CHIPS. We believe we have satisfactorily resolved these concerns (see changes made listed under Summary section).
Other signals:
Ergonomics
N/A
Activation
This feature introduces a new cookie attribute, Partitioned, which is opt-in only. Sites which do not set their cookies with Partitioned should not see any change in the browser's behavior when we ship.
Security
WebView application risks
Does this intent deprecate or change behavior of existing APIs, such that it has potentially high risk for Android WebView-based applications?
This feature does not deprecate or change behavior of existing APIs. This feature is behind a killswitch.
Will this feature be supported on all six Blink platforms (Windows, Mac, Linux, Chrome OS, Android, and Android WebView)?
Yes
Is this feature covered by web platform tests?
Flag name
partitioned-cookies
Requires code in //chrome?
No
Tracking bug:
Non-OSS dependencies
Does the feature depend on any code or APIs outside the Chromium open source repository and its open-source dependencies to function?
Not anymore than cookies already do now.
Estimated milestones
Anticipated spec changes
Open questions about a feature may be a source of future web compat or interop issues. Please list open issues (e.g. links to known github issues in the project for the feature specification) whose resolution may introduce web compat/interop risk (e.g., changing to naming or structure of the API in a non-backward-compatible way).
List of open issues: https://github.com/privacycg/CHIPS/issues
Chrome Platform Status page:
https://chromestatus.com/feature/5179189105786880
Links to previous Intent discussions
Intent to Prototype:
https://groups.google.com/a/chromium.org/g/blink-dev/c/hvMJ33kqHRo/
Intent to Experiment: https://groups.google.com/a/chromium.org/g/blink-dev/c/_dJFNJpf91U/m/YqP09XbbAgAJ
Intent to Extend Experiment:
https://groups.google.com/a/chromium.org/g/blink-dev/c/kZRtetS8jsY/m/ppK4kDbqAwAJ
https://groups.google.com/a/chromium.org/g/blink-dev/c/MKQODOL0Fso/m/nZXI2dqwAQAJ
Dylan Cutler
Mike West
--
You received this message because you are subscribed to the Google Groups "blink-dev" group.
To unsubscribe from this group and stop receiving emails from it, send an email to blink-dev+...@chromium.org.
To view this discussion on the web visit https://groups.google.com/a/chromium.org/d/msgid/blink-dev/CAMCNMFScgacg%3D3ueyRyOtUz4QnoJiYA9BKTryeWp_%2B%3D1Mi6yRg%40mail.gmail.com.
Rick Byers
To view this discussion on the web visit https://groups.google.com/a/chromium.org/d/msgid/blink-dev/CAKXHy%3Dcyb4d07a8PO8LUsSCTR3W2qM_ur43mejN4D_6t2XGc9Q%40mail.gmail.com.
Dylan Cutler
Hey Mike,
Thanks for your comments, let me address your two points:
I'd be happier if we'd been able to keep the `__Host-`-like restrictions on `Domain` and `Path` (even if not the prefix); that seems like a missed opportunity, given that we're going to need to support CHIPS into the indefinite future. The patch removing these requirements (https://github.com/privacycg/CHIPS/pull/46) references discussion on a PrivacyCG(?) call, but I wasn't able to find minutes. Could you help me understand the rationale?
The PrivacyCG feedback is best summarized here but the notes are sparse. While it would be ideal to keep the Domain restriction, we came to the conclusion that requiring no-Domain will make adoption of partitioned cookies more difficult for websites based on partner feedback (example), since there is significant site re-architecting that may be needed to adapt to the requirement.
As for Path, restricting Path to only "/" seems not necessary after removing the Domain restriction. During a PrivacyCG call on the matter, we also heard from partners that third-party embeds have use cases for setting cookie paths. You can see notes on the call here.
We are still requiring that cookies set with Partitioned should be set with Secure, and have no plans to remove that requirement.
There are a few issues open against the spec that seem like they ought to be resolved before shipping. https://github.com/privacycg/CHIPS/issues/58, https://github.com/privacycg/CHIPS/issues/40, and https://github.com/privacycg/CHIPS/issues/2 all seem like they would benefit from explicit resolution. Do you think those ought to be considered blockers?
Let me address each issue you linked:
For issue 58, "Specify what happens when partitioned cookies collide with same-name unpartitioned cookies," we believe that the correct behavior is to save and send both cookies. There is precedent for saving/storing multiple cookies with the same name. The Storage Model section of RFC626bis already defines how to handle cookies with the same name by treating cookies as unique based on their {name, domain, path}. Our implementation adds the cookie's partition key to this tuple. We have added a PR to our draft spec which we are publishing to the IETF datatracker. The issue has been closed now.
Issue 40, "Keying of "CHIPS" cookies should align with other state," can be reworded as "Should the cookie partition key have a cross-site ancestor chain bit?". The primary difference between Chromium’s storage partition key and cookie partition key is that the storage key has an additional bit which indicates whether the frame has a cross-site ancestor. This was added in order to fix an existing limitation where SameSite cookie semantics are not accounted for in service workers. Our thinking is that this bit is not relevant for the cookie partition key, since site developers can restrict which cookies are available in embedded contexts using the SameSite attribute already.
Issue 2, "User agents should indicate to servers whether a request is cross-site," we have not come to a solution for this but we think that mechanism applies to state partitioning broadly (not just CHIPS), and probably doesn't affect the UA's treatment of cookies. So, our request is to not treat this as a blocker for the launch of CHIPS.
Given that we have closed #58, #40 has a proposed resolution, and #2 should not be a blocker for the launch of CHIPS, we think we are ready to ship.
—
Hey Rick,
Let me answer your question as well.
I see there is one failing subtest on Chrome 108. Known issue that will be fixed prior to shipping?
That failure is expected since partitioned cookies are not enabled in Chrome 108. Cookies set with the Partitioned attribute in that version will create unpartitioned third-party cookies. Once the feature is enabled in Chrome 109 then the test should pass.
Also the harness is failing on Safari and Firefox, is that just because the test has a dependency on the Cookie Store API (while CHIPS is orthogonal from the API)?
That is entirely possible. Good catch! I am fixing this and will have a CL up shortly.
If Firefox decided to implement CHIPS but not Cookie Store would we be able / willing to modify the tests to pass on Firefox?
I suppose any CookieStore-related test could be guarded on the existence of window.cookieStore, so that those tests are skipped if the browser does not support the API.
Mike Taylor
Hey Rick,
Let me answer your question as well.
I see there is one failing subtest on Chrome 108. Known issue that will be fixed prior to shipping?That failure is expected since partitioned cookies are not enabled in Chrome 108. Cookies set with the Partitioned attribute in that version will create unpartitioned third-party cookies. Once the feature is enabled in Chrome 109 then the test should pass.
Also the harness is failing on Safari and Firefox, is that just because the test has a dependency on the Cookie Store API (while CHIPS is orthogonal from the API)?That is entirely possible. Good catch! I am fixing this and will have a CL up shortly.
If Firefox decided to implement CHIPS but not Cookie Store would we be able / willing to modify the tests to pass on Firefox?I suppose any CookieStore-related test could be guarded on the existence of window.cookieStore, so that those tests are skipped if the browser does not support the API.
Mike Taylor
Unless we consider Cookie Store to be a normative requirement of CHIPS (and I don't think we do), that doesn't seem like a great outcome. Can I ask what WPT is missing to be able to write these tests in a cross-browser fashion? A better outcome would be to add the missing functionality to WPT itself.
Mike West
Yoav Weiss
Contact emails:
dylan...@google.com, kaust...@google.com
Proposal repository:
https://github.com/privacycg/CHIPS
Design doc:
https://docs.google.com/document/d/1wL2lCXpaVOi0cWOn_ehfLFIZQxT3t0SH-ANnZYPEB0I/edit?usp=sharing
Specification:
https://datatracker.ietf.org/doc/draft-cutler-httpbis-partitioned-cookies/
--
You received this message because you are subscribed to the Google Groups "blink-dev" group.
To unsubscribe from this group and stop receiving emails from it, send an email to blink-dev+...@chromium.org.
To view this discussion on the web visit https://groups.google.com/a/chromium.org/d/msgid/blink-dev/CAMCNMFTt9hEnH1%2BBzB6c0qQijbBEJwvUKPKSO2gu7E-A%2BY_v8w%40mail.gmail.com.
Johann Hofmann
On Thu, Oct 20, 2022 at 10:57 PM 'Dylan Cutler' via blink-dev <blin...@chromium.org> wrote:Contact emails:
dylan...@google.com, kaust...@google.com
Proposal repository:
https://github.com/privacycg/CHIPS
Design doc:
https://docs.google.com/document/d/1wL2lCXpaVOi0cWOn_ehfLFIZQxT3t0SH-ANnZYPEB0I/edit?usp=sharing
Specification:
https://datatracker.ietf.org/doc/draft-cutler-httpbis-partitioned-cookies/
Can you expand on the plans for this I-D? Have y'all talked to the HTTPWG?
To view this discussion on the web visit https://groups.google.com/a/chromium.org/d/msgid/blink-dev/CAL5BFfUDzq6pUpw_%2BGMBxzrsb23qtw5Vnv-QG6yZQ35G_j%2BZfQ%40mail.gmail.com.
Chris Harrelson
Hi Yoav,On Wed, Nov 23, 2022 at 5:28 AM Yoav Weiss <yoav...@chromium.org> wrote:On Thu, Oct 20, 2022 at 10:57 PM 'Dylan Cutler' via blink-dev <blin...@chromium.org> wrote:Contact emails:
dylan...@google.com, kaust...@google.com
Proposal repository:
https://github.com/privacycg/CHIPS
Design doc:
https://docs.google.com/document/d/1wL2lCXpaVOi0cWOn_ehfLFIZQxT3t0SH-ANnZYPEB0I/edit?usp=sharing
Specification:
https://datatracker.ietf.org/doc/draft-cutler-httpbis-partitioned-cookies/
Can you expand on the plans for this I-D? Have y'all talked to the HTTPWG?Yes, this is being discussed in HTTPWG. Dylan presented CHIPS at IETF 115, minutes are here: https://httpwg.org/wg-materials/ietf115/minutes.html#cookies
To view this discussion on the web visit https://groups.google.com/a/chromium.org/d/msgid/blink-dev/CAD_OO4gVfT1aAHE4%3D3Cs6KoCA54q14bGaPepuqofdTEKJVkkgw%40mail.gmail.com.
Johann Hofmann
On Wed, Nov 23, 2022 at 10:34 AM 'Johann Hofmann' via blink-dev <blin...@chromium.org> wrote:Hi Yoav,On Wed, Nov 23, 2022 at 5:28 AM Yoav Weiss <yoav...@chromium.org> wrote:On Thu, Oct 20, 2022 at 10:57 PM 'Dylan Cutler' via blink-dev <blin...@chromium.org> wrote:Contact emails:
dylan...@google.com, kaust...@google.com
Proposal repository:
https://github.com/privacycg/CHIPS
Design doc:
https://docs.google.com/document/d/1wL2lCXpaVOi0cWOn_ehfLFIZQxT3t0SH-ANnZYPEB0I/edit?usp=sharing
Specification:
https://datatracker.ietf.org/doc/draft-cutler-httpbis-partitioned-cookies/
Can you expand on the plans for this I-D? Have y'all talked to the HTTPWG?Yes, this is being discussed in HTTPWG. Dylan presented CHIPS at IETF 115, minutes are here: https://httpwg.org/wg-materials/ietf115/minutes.html#cookiesGreat. Were there any concerns raised there that might create a risk for CHIPS?
Yoav Weiss
On Wed, Nov 23, 2022 at 5:37 PM Chris Harrelson <chri...@chromium.org> wrote:On Wed, Nov 23, 2022 at 10:34 AM 'Johann Hofmann' via blink-dev <blin...@chromium.org> wrote:Hi Yoav,On Wed, Nov 23, 2022 at 5:28 AM Yoav Weiss <yoav...@chromium.org> wrote:On Thu, Oct 20, 2022 at 10:57 PM 'Dylan Cutler' via blink-dev <blin...@chromium.org> wrote:Contact emails:
dylan...@google.com, kaust...@google.com
Proposal repository:
https://github.com/privacycg/CHIPS
Design doc:
https://docs.google.com/document/d/1wL2lCXpaVOi0cWOn_ehfLFIZQxT3t0SH-ANnZYPEB0I/edit?usp=sharing
Specification:
https://datatracker.ietf.org/doc/draft-cutler-httpbis-partitioned-cookies/
Can you expand on the plans for this I-D? Have y'all talked to the HTTPWG?Yes, this is being discussed in HTTPWG. Dylan presented CHIPS at IETF 115, minutes are here: https://httpwg.org/wg-materials/ietf115/minutes.html#cookiesGreat. Were there any concerns raised there that might create a risk for CHIPS?Not as far as I'm aware of. I couldn't attend the meeting in person, but revisited it with the team. From what I was told the main discussion point was whether we shouldn't just partition all 3P cookies by default instead of giving developers the ability to decide. It's a valid question, but one that has been extensively discussed between browser vendors in Privacy CG, and both Safari and Chrome have made it clear that they strongly prefer blocking 3P cookies by default (with Firefox not being opposed to that). We'll of course keep on engaging with these concerns and questions in HTTPWG, but it seems like a decision that ultimately browsers should have the most authority on.In any case, I don't think that this discussion presents any compat risk for CHIPS, as the Partitioned attribute would be compatible with a hypothetical partition-by-default future (i.e. by being a no-op).
Rick Byers
To view this discussion on the web visit https://groups.google.com/a/chromium.org/d/msgid/blink-dev/CAL5BFfXOZKtBQPewkukz85JZdT6OXSqLTz8%2BvUZQ6rBaY4hQ3g%40mail.gmail.com.
Dylan Cutler
Dylan Cutler
Dylan Cutler
Dylan Cutler
Dylan Cutler
Dylan Cutler
Dylan Cutler
Hi @Dylan,
What's the current status of the rollout? Have you moved to 50%?
Best,
Alex M
Alexandru Mihai
What's the current status of the rollout? Have you moved to 50%?
Best,
Alex M
Kaustubha Govind
Alexandru Mihai
On Mar 30, 2023, at 03:49, Kaustubha Govind <kaust...@google.com> wrote:
Hi Alex,
Kaustubha Govind
Awesome, thanks for letting me know 🙂The rollout will cover all versions from 110 to current, not just the latest version right?
Kaustubha Govind
Eric Lawrence
Dylan Cutler
Eric Lawrence
I looked at traces and confirmed that the problem is that the Auth provider is setting its cookie as "Partitioned" and this causes the cookie to never appear in the subframe of the app. Turning off support for Partitioned cookies causes the site to work correctly.
I built a reduced repro here: https://debugtheweb.com/test/auth/app.html
Mircea Craciun
Kaustubha Govind
Kaustubha Govind
Kaustubha Govind
And the screenshot :
And can we have a link from where we can download the 114 version before the release at least to test it ?Would be really nice for us to be able to check the Chrome releases before they go live so we can adapt if needed or at least to communicate with you what issues we might have
Best regards,
Mircea
From: Kaustubha Govind <kaust...@google.com>
Sent: Saturday, 8 April 2023 02:21
To: blink-dev <blin...@chromium.org>
Cc: Kaustubha Govind <kaust...@google.com>; Mircea Craciun <mircea.craciun%sap...@gtempaccount.com>; Eric Lawrence <eri...@microsoft.com>; dylan...@google.com <dylan...@google.com>; Alexandru Mihai <a.m...@eyeo.com>; Chris Harrelson <chri...@chromium.org>; joha...@google.com <joha...@google.com>; blink-dev <blin...@chromium.org>; rby...@chromium.org <rby...@chromium.org>; yoav...@chromium.org <yoav...@chromium.org>; Eric Lawrence <bay...@gmail.com>
Subject: Re: [blink-dev] Intent to Ship: Cookies Having Independent Partitioned State (CHIPS)
You don't often get email from kaust...@google.com. Learn why this is important
Kaustubha Govind
Craciun, Mircea
On 8. Apr 2023, at 02:20, Kaustubha Govind <kaust...@google.com> wrote:
Craciun, Mircea
Hi Govid,
Thank you for the help but is not working:
You can test here:
https://salesdemo.successfactors.eu/login?company=SFPART061393
Welcome1!
Best regards,
Mircea
From: Kaustubha Govind <kaust...@google.com>
Sent: Saturday, 8 April 2023 02:21
To: blink-dev <blin...@chromium.org>
Cc: Kaustubha Govind <kaust...@google.com>; Mircea Craciun <mircea.craciun%sap...@gtempaccount.com>; Eric Lawrence <eri...@microsoft.com>; dylan...@google.com <dylan...@google.com>; Alexandru Mihai <a.m...@eyeo.com>; Chris Harrelson <chri...@chromium.org>;
joha...@google.com <joha...@google.com>; blink-dev <blin...@chromium.org>; rby...@chromium.org <rby...@chromium.org>; yoav...@chromium.org <yoav...@chromium.org>; Eric Lawrence <bay...@gmail.com>
Subject: Re: [blink-dev] Intent to Ship: Cookies Having Independent Partitioned State (CHIPS)
|
You don't often get email from kaust...@google.com. Learn why this is important |
Mircea:
Craciun, Mircea
And the screenshot :
And can we have a link from where we can download the 114 version before the release at least to test it ?Would be really nice for us to be able to check the Chrome releases before they go live so we can adapt if needed or at least to communicate with you what issues we might have
Best regards,
Mircea
From: Kaustubha Govind <kaust...@google.com>
Sent: Saturday, 8 April 2023 02:21
To: blink-dev <blin...@chromium.org>
Cc: Kaustubha Govind <kaust...@google.com>; Mircea Craciun <mircea.craciun%sap...@gtempaccount.com>; Eric Lawrence <eri...@microsoft.com>; dylan...@google.com <dylan...@google.com>; Alexandru Mihai <a.m...@eyeo.com>; Chris Harrelson <chri...@chromium.org>;
joha...@google.com <joha...@google.com>; blink-dev <blin...@chromium.org>; rby...@chromium.org <rby...@chromium.org>; yoav...@chromium.org <yoav...@chromium.org>; Eric Lawrence <bay...@gmail.com>
Subject: Re: [blink-dev] Intent to Ship: Cookies Having Independent Partitioned State (CHIPS)
|
You don't often get email from kaust...@google.com. Learn why this is important |
Mircea:
Craciun, Mircea
On 8. Apr 2023, at 15:25, Kaustubha Govind <kaust...@google.com> wrote:
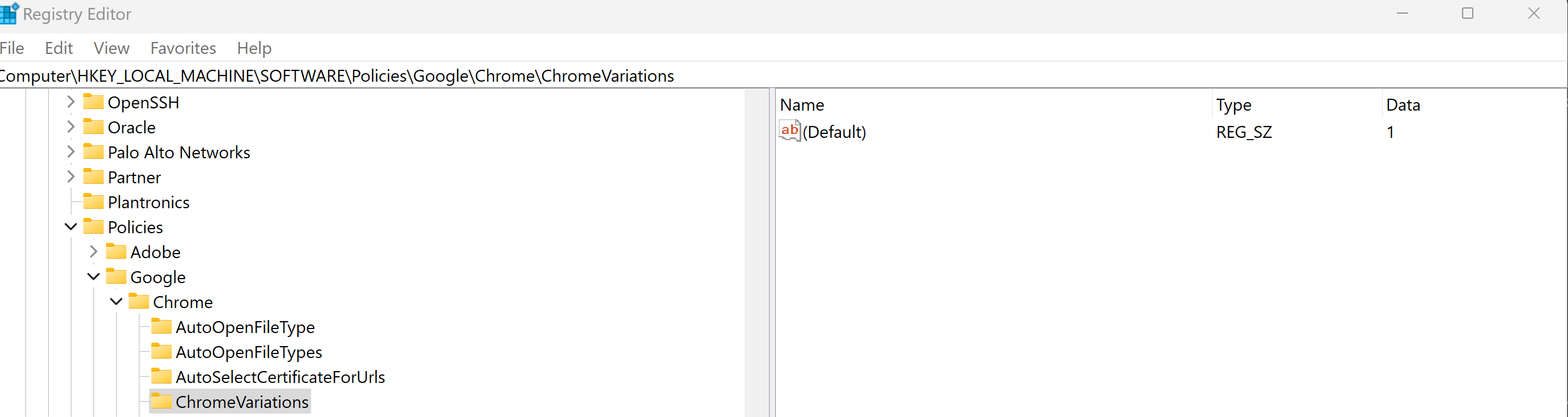
Circling back on the main thread. Setting the ChromeVariations policy to Value 1 did indeed disable CHIPS for the enterprise customer, and resolve the issue (as a reminder, this will only be effective through Chrome 113).
HUGE THANKS to Eric Lawrence for helping us figure out that Mircea's set up had chrome://flags#partitioned-cookies set to "Enabled", which was overriding the policy and keeping CHIPS enabled. Setting that back to "Default" was the solution.
On Sat, Apr 8, 2023, 7:35 AM Kaustubha Govind <kaust...@google.com> wrote:
Hi Mircea,
When I test your site; login works for me even regardless of whether PartitionedCookies is enabled/disabled. You can force enable/disable the feature by using the drop-down at chrome://flags#partitioned-cookies.
Happy to fork this discussion into a smaller/private thread, and report back here when we've come to a resolution.
K
On Sat, Apr 8, 2023 at 7:17 AM Craciun, Mircea <mircea....@sap.com> wrote:
And the screenshot :
<image001.png>