HSTS Preload List: State of the Union 2016
996 views
Skip to first unread message
Lucas Garron
Feb 18, 2016, 4:30:46 PM2/18/16
to security-dev
Yarholsky!
tl;dr: the preload list is growing very quickly (peek at the chart below). Doc with more details here.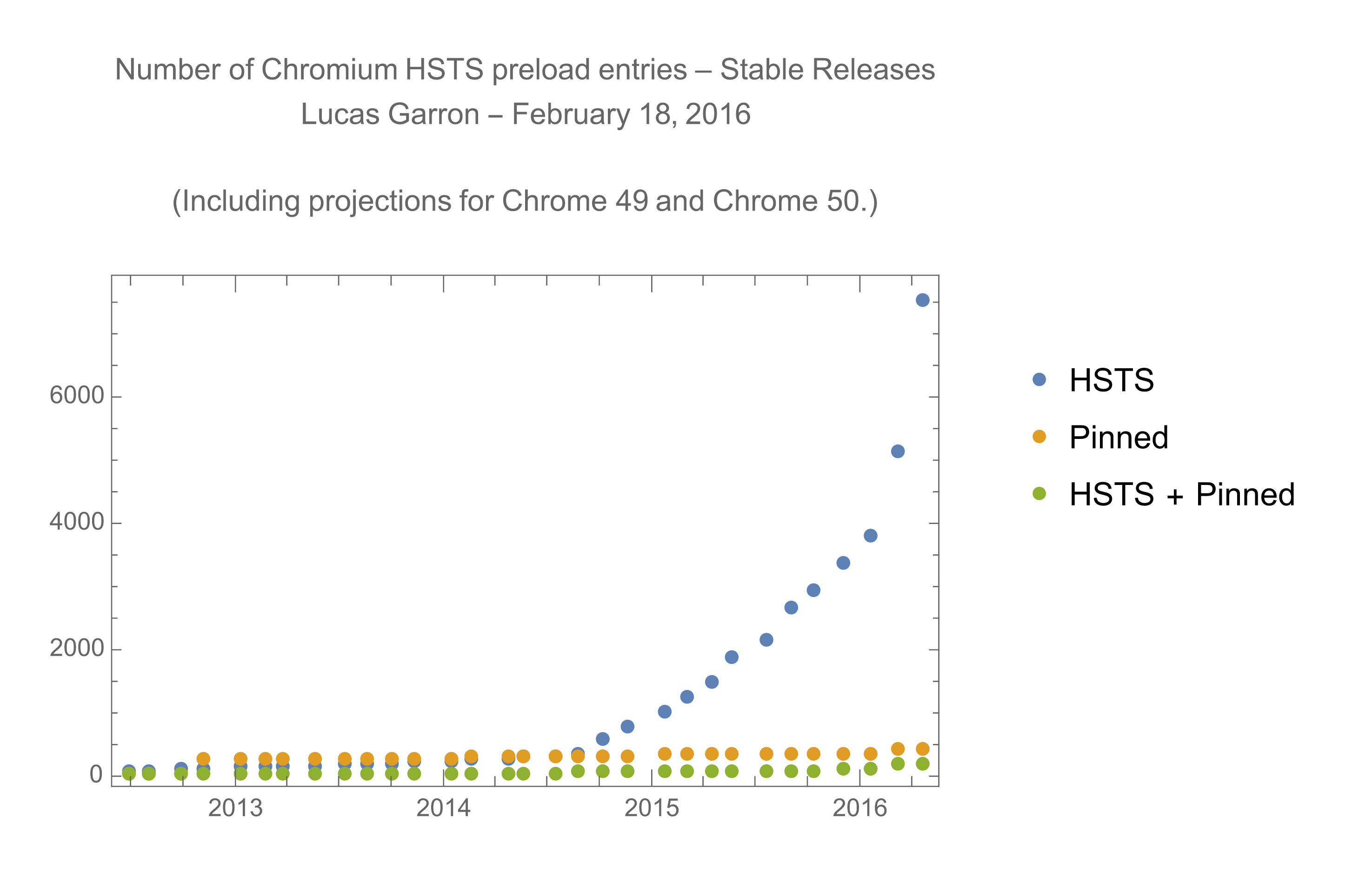

I took over the HSTS preload list from agl@ in late 2014, which is when submissions to hstspreload.appspot.com first took off. However, growth is accelerating as of Chrome 49. This may be a one-off event (e.g. due to Let's Encrypt), or it may continue into the future.
I've written up a doc with various concerns that have come up due to growth in the last year. For lack of creativity, it is titled HSTS Preload List: State of the Union 2016. Nothing in it should be especially surprising, but removals are on the rise and there are likely to be many stale entries by now.
I plan to start biting off tasks from the start of the doc:
- Issue 587957 Fold the HSTS "manual" review into hstspreload.appspot.com
- Issue 587973 Analyze HSTS Preload List trends
- Issue 587978 Create a form for HSTS removals.
The doc also has plenty more TODOs. If anyone is interested in tackling some of them, I'd be happy to get you up to speed with additional details.
G'fun,
»Lucas
PS(A): I'm keeping an eye out for HSTS advice that asks site operators to include the preload token without considering the implications for subdomains. This can result in "unintentional" preload submissions and upset emails and site operators. If you come across any such advice on the internet, please let me know.
Lucas Garron
Feb 29, 2016, 3:35:45 PM2/29/16
to security-dev
Followup: In order to handle the increasing number of removal requests, I'd like to introduce a token for sites to request that they should not be preloaded. My current strawman for this is `no-preload`.
Like the `preload` token, this is is not an officially specced token, just something to automate preload list handling. I'd like to start documenting it on https://hstspreload.appspot.com/ as the standard way to ask for removal, starting within the next few days.
If you have thoughts on this, please give feedback at https://crbug.com/590357
Lucas Garron
Feb 29, 2016, 3:37:07 PM2/29/16
to security-dev, Chrome-Security-Enamel, chrome-security-owp
[Internal forward.]
If no one objects, I'll be moving forward with it this week.
Lucas Garron
Apr 6, 2016, 11:35:53 PM4/6/16
to security-dev
Following up on this:
Based on the discussion in the bug, I have decided to try to avoid introducing a token/directive.
Per this comment, sites added as of Chrome 51 are now expected to continue to send the preload directive to stay preloaded. There are no active plans to prune domains who stop sending the directive, but we may look at pruning in the future. To this end, I am planning start a spec to standardize the semantics of the preload directive. Follow https://crbug.com/591212 for updates.
This means that the officially recommended way to authenticate a removal request is is simply to remove the preload directive and send an email request. I've added more detailed instructions at hstspreload.appspot.com .
As a site note, I've made a lot of progress overhauling the submission process so that all the requirements are checked during initial submission (instead of having a second review step). I plan to launch the new site this month. Star https://github.com/chromium/hstspreload for updates.
Cheers,
»LucasLucas Garron
May 18, 2016, 9:04:40 PM5/18/16
to security-dev
https://hstspreload.appspot.com/ has been updated to "v2". The page looks pretty much the same, but the backend has been entirely rewritten. If you're curious, the new system is described in this doc.
The requirement checking for preloading have been tightened up in a bunch of edge cases, especially when it comes to redirects. However, I think site owners will appreciate that the requirements are now all checked when the domain is submitted to hstspreload.appspot.com – there is no secondary review with additional checks, and you get feedback immediately when you enter the domain on the submission site.
If you know Go, you can take a look at the hstspreload package that powers this. You can also use a command-line tool to check preloadability as follows:
go get github.com/chromium/hstspreload/...
hstspreload preloadabledomain wikipedia.org
G'fun,
»Lucas
hmzhn...@gmail.com
Apr 12, 2018, 10:43:45 PM4/12/18
to Security-dev, lga...@google.com
در جمعه 19 فوریهٔ 2016، ساعت 1:00:46 (UTC+3:30)، Lucas Garron نوشته:
> Yarholsky!
>
>
> tl;dr: the preload list is growing very quickly (peek at the chart below). Doc with more details here.
>
>
>
>
>
>
> tl;dr: the preload list is growing very quickly (peek at the chart below). Doc with more details here.
>
>
>
>
> I took over the HSTS preload list from agl@ in late 2014, which is when submissions to hstspreload.appspot.com first took off. However, growth is accelerating as of Chrome 49. This may be a one-off event (e.g. due to Let's Encrypt), or it may continue into the future.
>
>
> I've written up a doc with various concerns that have come up due to growth in the last year. For lack of creativity, it is titled HSTS Preload List: State of the Union 2016. Nothing in it should be especially surprising, but removals are on the rise and there are likely to be many stale entries by now.
>
>
> I plan to start biting off tasks from the start of the doc:
> Issue 587957 Fold the HSTS "manual" review into hstspreload.appspot.com
> Issue 587973 Analyze HSTS Preload List trendsIssue 587978 Create a form for HSTS removals.
>
>
> I've written up a doc with various concerns that have come up due to growth in the last year. For lack of creativity, it is titled HSTS Preload List: State of the Union 2016. Nothing in it should be especially surprising, but removals are on the rise and there are likely to be many stale entries by now.
>
>
> I plan to start biting off tasks from the start of the doc:
> Issue 587957 Fold the HSTS "manual" review into hstspreload.appspot.com
>
> The doc also has plenty more TODOs. If anyone is interested in tackling some of them, I'd be happy to get you up to speed with additional details.
>
>
> G'fun,
> »Lucas
>
>
> PS(A): I'm keeping an eye out for HSTS advice that asks site operators to include the preload token without considering the implications for subdomains. This can result in "unintentional" preload submissions and upset emails and site operators. If you come across any such advice on the internet, please let me know.
Y by cu eRr e :-(z> The doc also has plenty more TODOs. If anyone is interested in tackling some of them, I'd be happy to get you up to speed with additional details.
>
>
> G'fun,
> »Lucas
>
>
> PS(A): I'm keeping an eye out for HSTS advice that asks site operators to include the preload token without considering the implications for subdomains. This can result in "unintentional" preload submissions and upset emails and site operators. If you come across any such advice on the internet, please let me know.
Reply all
Reply to author
Forward
0 new messages
