Stored XSS vulnerability in subdomain of atsign
2 views
Skip to first unread message
shiva kurapati
Jul 12, 2022, 7:51:13 AM7/12/22
to devel...@atsign.com, tyler...@atsign.com, in...@atsign.com
Description: Stored XSS, also known as persistent XSS, is more damaging than non-persistent XSS. It occurs when a malicious script is injected directly into a vulnerable web application.
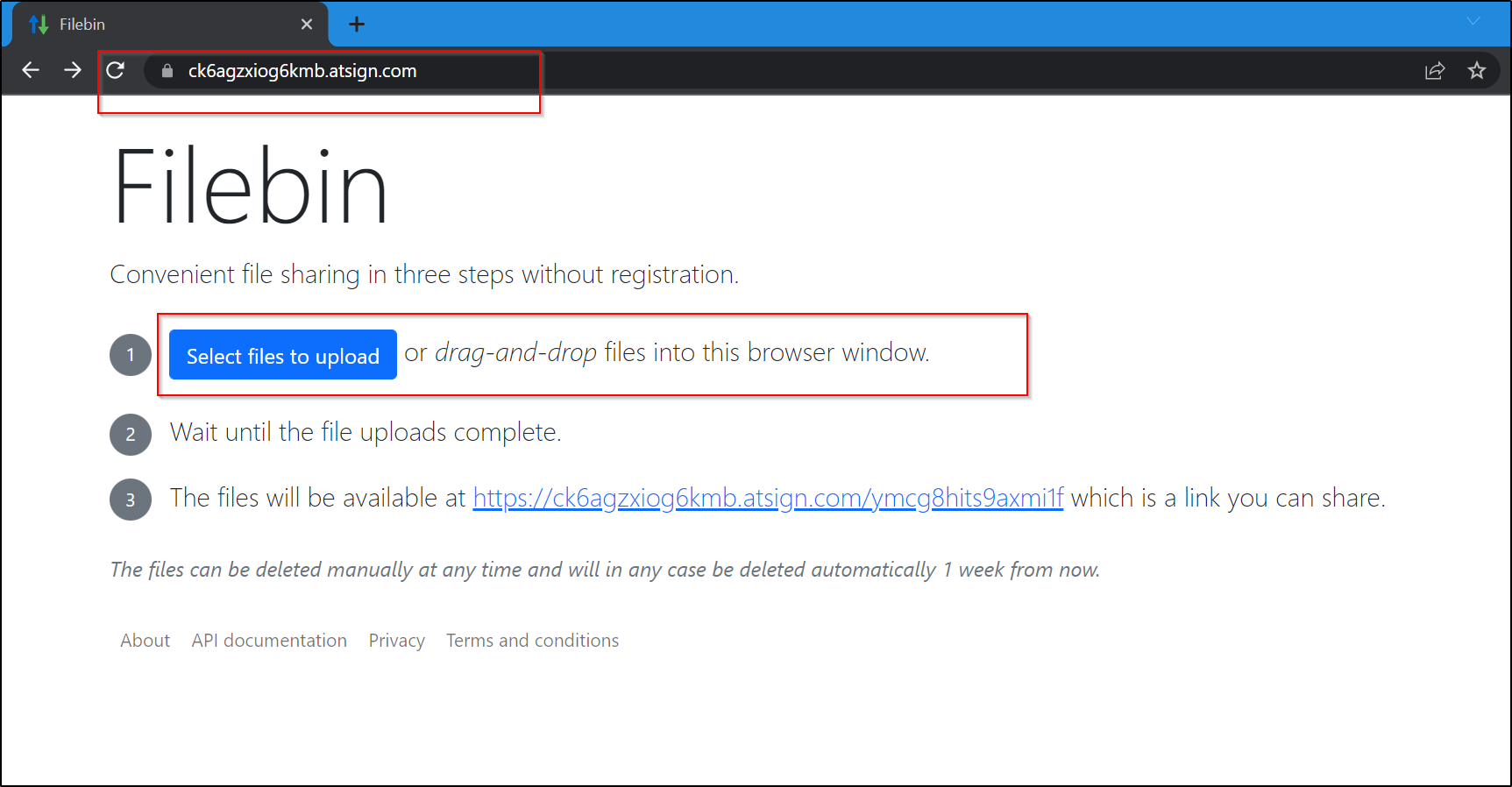
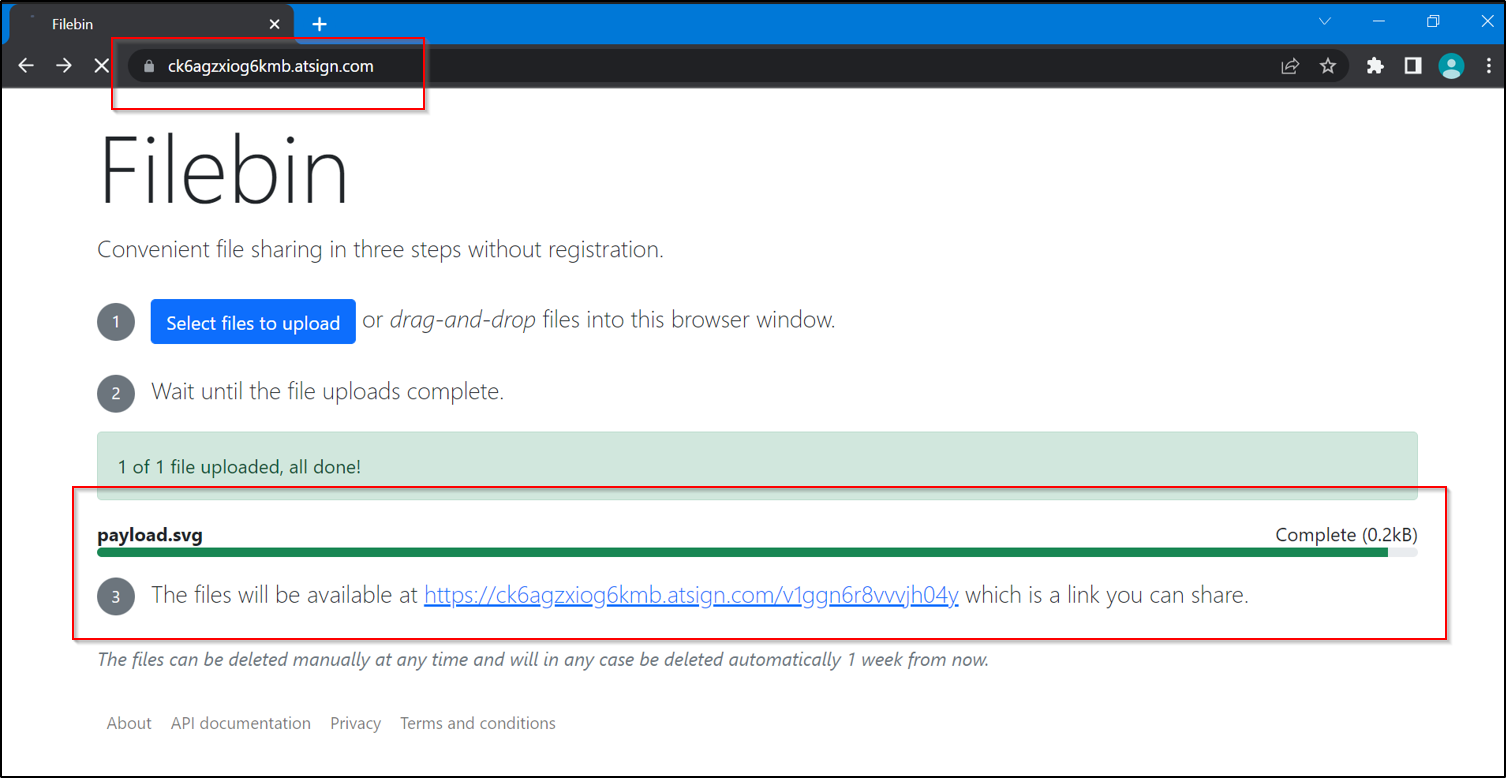
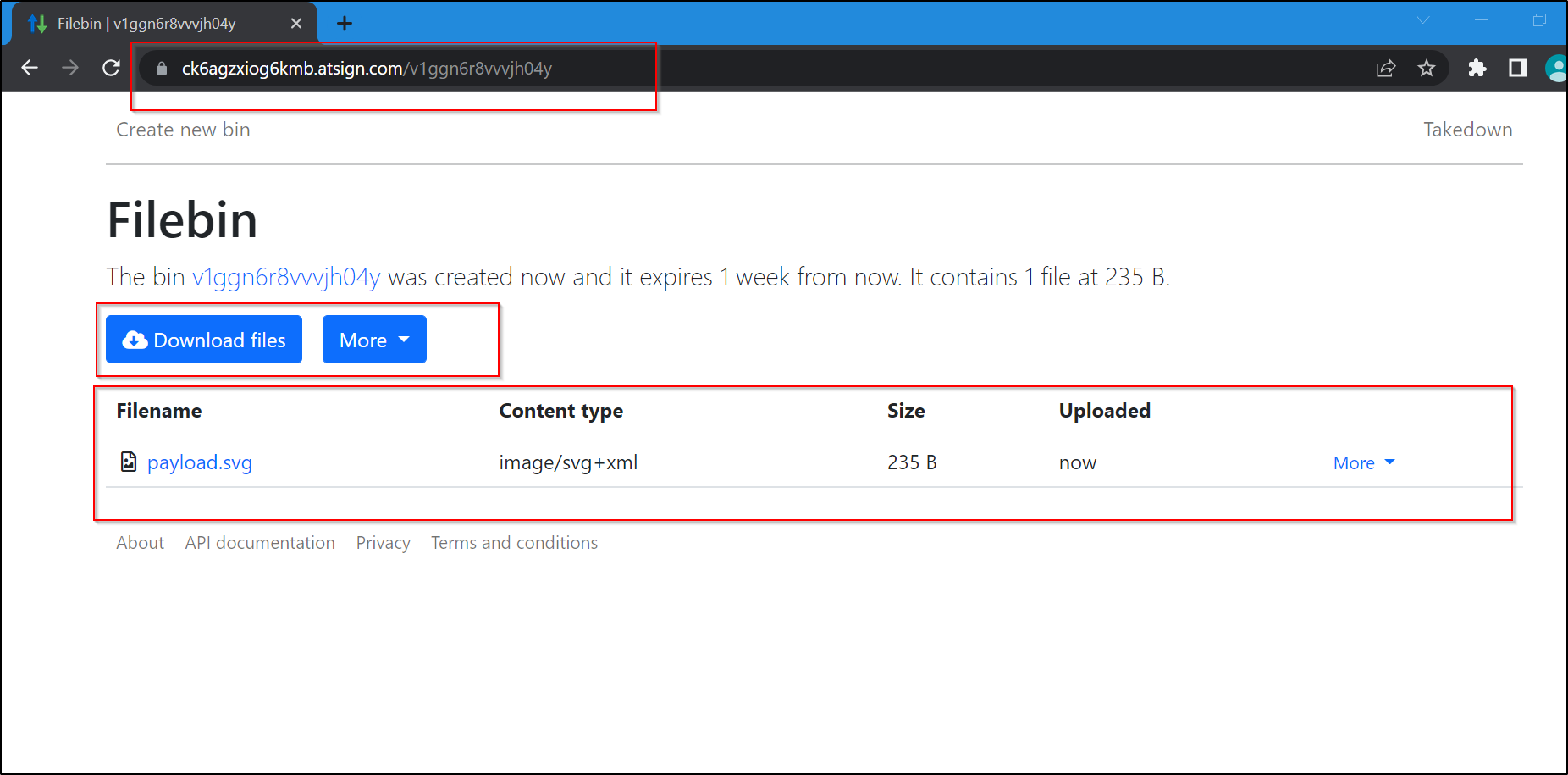
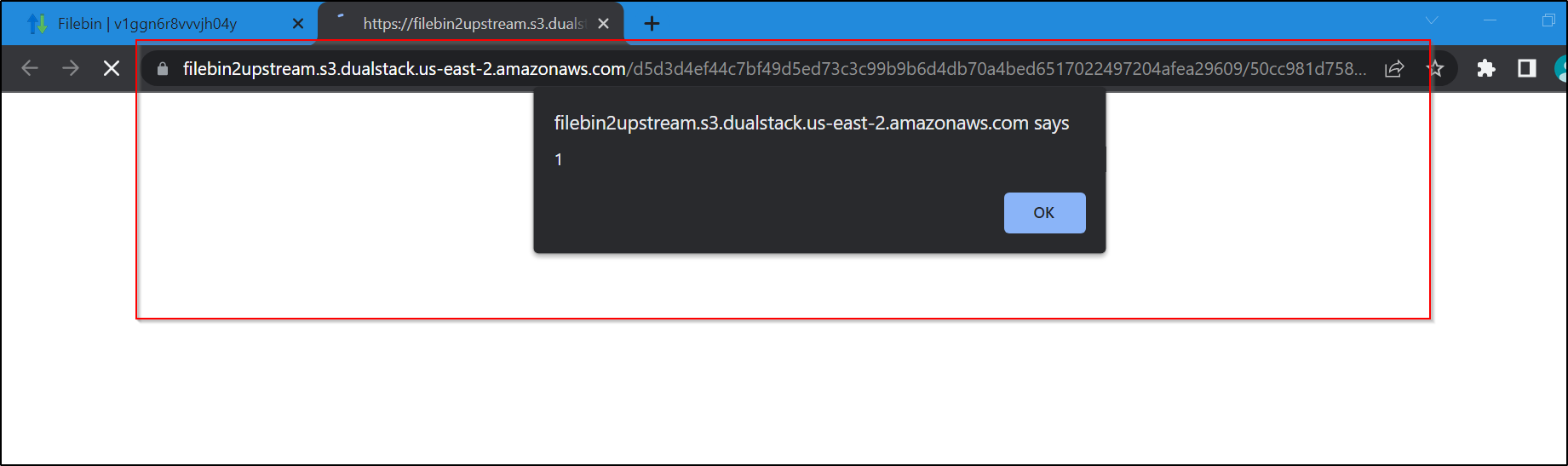
Steps to Reproduce:
2. click on " select files to upload"
3. upload the payload file which is given in this mail
4. click on the file after it gets uploaded
5. and the stored XSS gets popped up
6. To confirm it as stored XSS do refresh the tab multiple times yet u get the pop-up as usual which means the XSS is stored.
Impact:
1. Stored Cross-Site Scripting can have huge implications for a web application and its users and people can download malicious files without knowing them.
2. An attacker could steal credentials.
3. An attacker could exfiltrate sensitive data.
Mitigation :
1. Validate inputs.
2. Secure your cookies
3. Sanitize data
4. Use a web application firewall (WAF)
5. Whenever possible, prohibit HTML code in inputs.
2. Secure your cookies
3. Sanitize data
4. Use a web application firewall (WAF)
5. Whenever possible, prohibit HTML code in inputs.
POC:
1. go on to the vulnerable site ( https://ck6agzxiog6kmb.atsign.com/ ) and click on the select file to upload

2. upload the payload.svg file in it

3. after it gets uploaded , open the file in a new tab

4. and you will be able to see the stored XSS, To confirm it as stored XSS do refresh the tab multiple times yet u get the pop-up as usual which means the XSS is stored.

Reply all
Reply to author
Forward
0 new messages
